Hi,
I was reading this ticket https://abp.io/support/questions/6432/v800-Permission-issue and I am wondering how to apply the suggested solution in the context of OpenIddict module that has replaced IdentityServer module according to https://abp.io/docs/latest/modules/identity-server.
My actual problem is that user permissions are granted successfully, i.e. I can see the entries in AbpPermissionGrants table, but are never applied when running. To be more specific, I have a RadzenSplitButtonItem inside an AuthorizeView bound to a Policy. I've provided the user permissions for that Policy through the relative ABP Permissions Management screen but never see the RadzenSplitButtonItem when logging with the authorized user. On the contrary, when I apply the same Policy to one of the roles that the user in question has, the RadzenSplitButtonItem appears. I've logged out, flushed the Redis cache, restarted the application etc.
- ABP Framework version: v8.3.4
- UI Type: Blazor WASM
- Database System: EF Core (SQL Server)
- Tiered (for MVC) or Auth Server Separated (for Angular): Separate AuthServer project in the solution, which we start without debugging as a separate instance before running the application in development mode.
Thanks in advance Antonis Varkas Byte Computer
17 Answer(s)
-
0
To address your issue with user-level permissions not being applied in an ABP solution using the OpenIddict module (instead of IdentityServer), here are the key points and steps you should follow:
User vs. Role Permissions in ABP
- ABP's permission system supports granting permissions directly to users or via roles.
- If a permission is granted to a user, it should be effective immediately (after cache refresh, logout/login, etc.), just like role-based permissions.
OpenIddict vs. IdentityServer
- The workaround from the referenced ticket (disabling claim type updates in IdentityServer) is specific to IdentityServer and not required for OpenIddict.
- OpenIddict does not override or remap ABP claim types by default, so you do not need to add the
PreConfigureServicescode forAbpIdentityServerBuilderOptions.
Troubleshooting User Permissions Not Applying
- Ensure that the user is not only assigned the permission in the UI, but that the permission is granted in the
AbpPermissionGrantstable with the correctProviderName(Ufor user,Rfor role) andProviderKey(user ID). - Make sure your Blazor WASM client is requesting updated claims after login or after permissions change. Sometimes, the access token or user info is cached and not refreshed.
- If you are using Redis or distributed cache, ensure that the cache is cleared or invalidated after permission changes.
- The
AuthorizeViewcomponent in Blazor checks the current user's claims. If the permission is not present, it may be due to the claims not being refreshed or propagated to the client.
- Ensure that the user is not only assigned the permission in the UI, but that the permission is granted in the
Force Claims Refresh for User Permissions
- ABP uses dynamic claims and may require a refresh for the user's claims after a permission change. In Blazor WASM, this is typically handled by re-authenticating or explicitly triggering a claims refresh.
- If you are using ABP's dynamic claims system, ensure that the
app.UseDynamicClaims()middleware is configured only in the AuthServer and Web projects, not in all microservices. - If you have enabled dynamic claims, verify that the
AbpClaimsPrincipalFactoryOptions.IsDynamicClaimsEnabledis set appropriately (usuallytruefor dynamic claims).
Recommended Steps
- Log out and log in again after granting user permissions.
- If using distributed cache (e.g., Redis), flush the cache after permission changes.
- Ensure that your AuthServer and Web projects are correctly configured for dynamic claims (middleware and options).
- If the problem persists, check the logs for any errors related to claims or permission fetching.
Sample: Dynamic Claims Configuration
// In your AuthServer and Web module context.Services.Configure<AbpClaimsPrincipalFactoryOptions>(options => { options.IsDynamicClaimsEnabled = true; }); // In Startup/Program.cs app.UseDynamicClaims();- If You Still Have Issues
- Double-check that the user's claims are being refreshed and that the access token contains the expected permissions.
- Use ABP's built-in permission checking methods (e.g.,
IAuthorizationService.IsGrantedAsync) to debug on the server side.
Sources:
- ABP Permission System
- ABP Dynamic Claims
- ABP Identity Server Module Migration
- ABP Support Ticket 6432
This approach aligns with common ABP conventions for OpenIddict and dynamic claims. If you follow these steps and the issue persists, please check for customizations or middleware that might interfere with claims propagation.
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
hi
How can I reproduce your problem in a new template project?
Can you share some code and steps?
Thanks.
-
0
Hi,
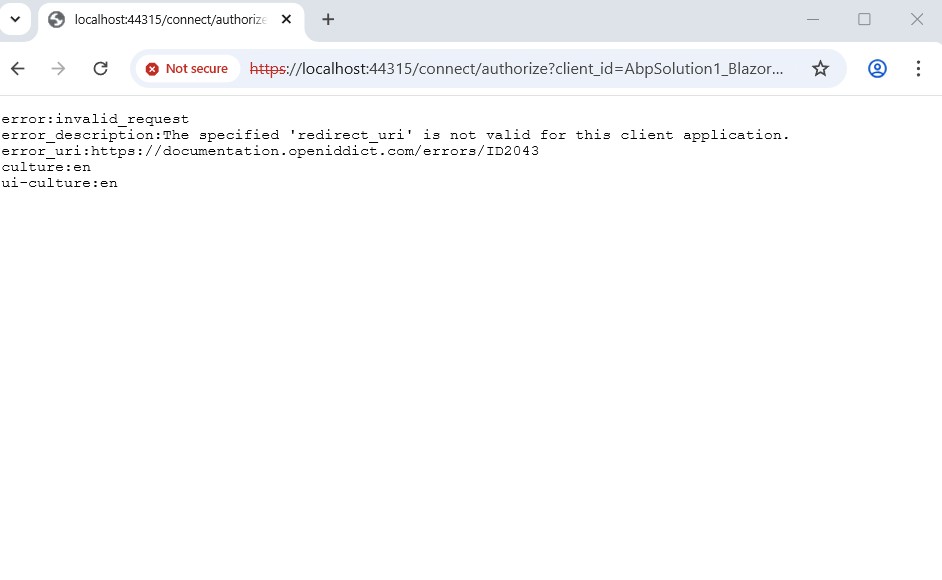
I tried to create a template solution through ABP Studio and simulate what I described but fail to display the menu under admin account, so that I have access to the Permissions management UI.
As far as the AI-Bot's notes are concerned, please note we have covered everything stated there.
Best Regards, Antonis Varkas Byte Computer
-
0
hi
but fail to display the menu under admin account,
Could you please share a screenshot and some code related to this case?
Thanks.
-
0
-
0
hi
Have you run the DbMigrator app to seed initial data to the database?
Please try to add a valid SSL certification.
https://learn.microsoft.com/en-us/dotnet/core/tools/dotnet-dev-certs#examples
Then share the logs.txt of
https://localhost:44315/website to liming.ma@volosoft.comThanks.
-
0
-
0
hi
Can you try to set up a valid SSL and run apps again.
If the problem still present, please share the
logs.txtof the web, api and authserver websites.liming.ma@volosoft.com
Thanks.
-
0
Hi,
I had already done that...
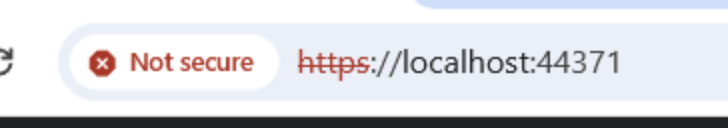
dotnet dev-certs https -ep ./certificate.pfx -p $CREDENTIAL_PLACEHOLDER$ --trustI used the above snippet from the link you shared. My browser keeps displaying the
Not securesign.I 'll email you the log files from the 3 projects...
-
0
-
0
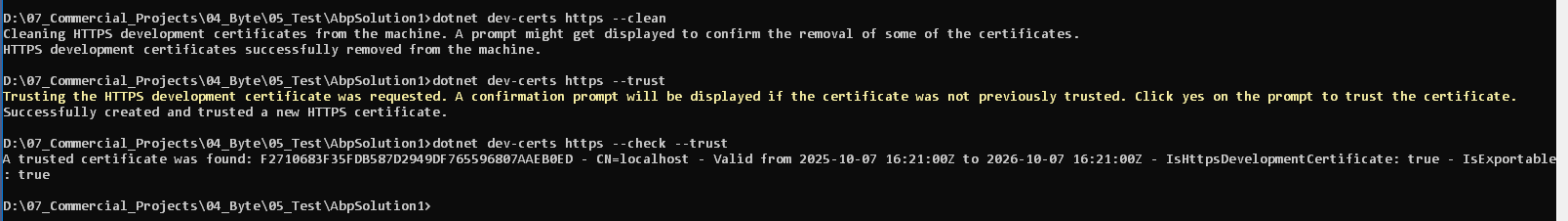
As I wrote, I executed the command I quoted. It ended up successfully in Visual Studio Terminal. The next run ended up in the
Not securesign on the browser. I have no idea why it ignores the certificate installed. If you can assist o that, please share your thoughts, since you believe this may affect the actual target of the ticket. -
0
hi
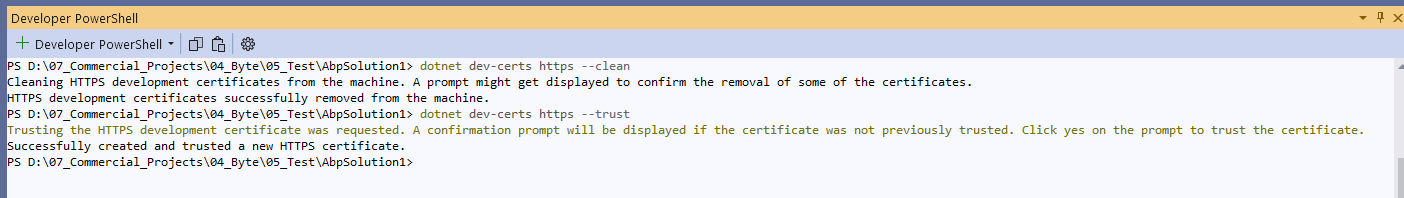
can you try to clean and create a new one?
dotnet dev-certs https --clean dotnet dev-certs https --trust dotnet dev-certs https --check --trustPlease share the output of these commands.
Thanks.
-
0
hi
Your logs show:
The SSL connection could not be established, see inner exception. ---> System.Security.Authentication.AuthenticationException: The remote certificate is invalid because of errors in the certificate chain: NotTimeValidThe problem is related to SSL.
Thanks
-
0
-
0
Hi
Try to run the commands in cmd/terminal windows with administrator mode.
-
0
-
0
hi
You can send a email to liming.ma@volosoft.com when you are free.
I will remotely check it by Zoom screensharing.
Thanks.