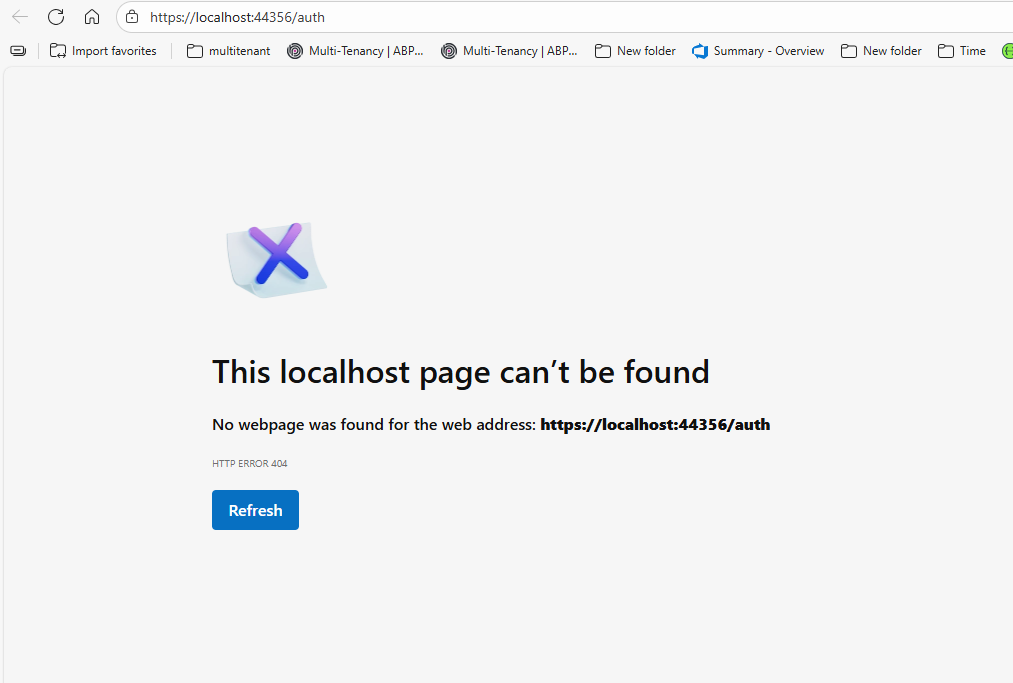
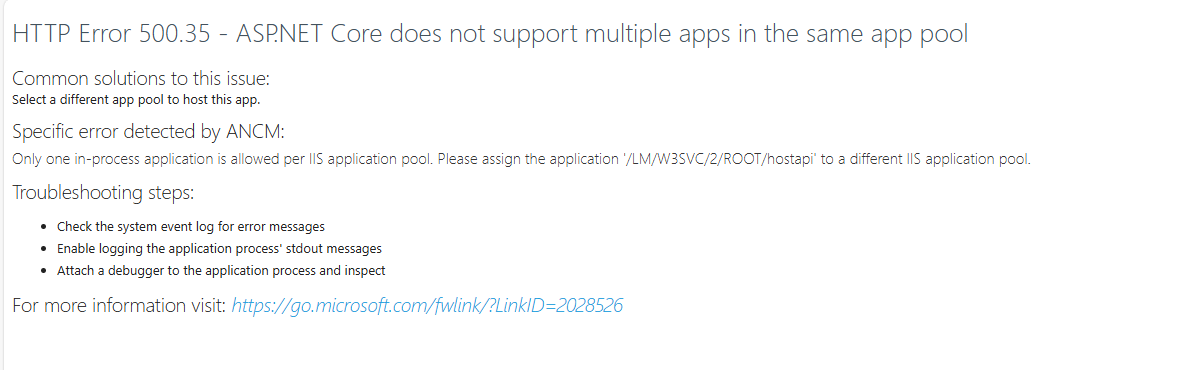
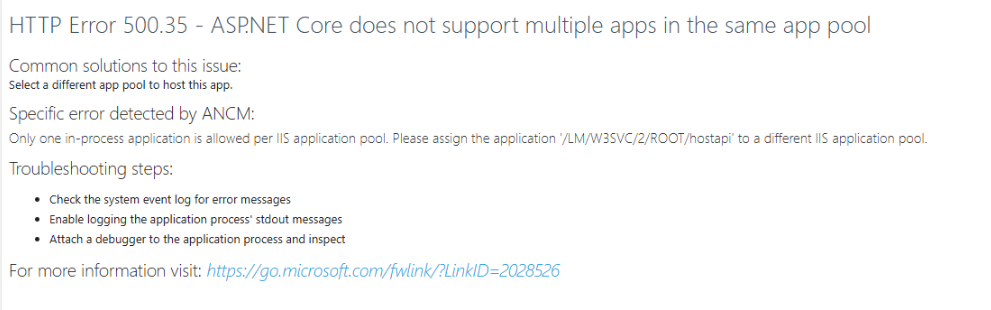
- Steps to reproduce the issue: Created a sample ABP project Auth server : https://localhost:44339 Host Server : Https://localhost:44342 WebServer : Https://localhost:44378
Goal is to make : Hostserver: Https://localhost:44378/api AuthServer: Https://localhost:44378/auth webServer: Https://localhost:44378
I tried reverse proxy but it is not working.
18 Answer(s)
-
0
To achieve your goal of exposing multiple ABP services (Host, Auth, Web) under a single domain and port using a reverse proxy, you need to ensure that:
- Each backend service is configured to work behind a reverse proxy.
- Path-based routing is set up in your reverse proxy (e.g., IIS, Nginx, or YARP).
- Forwarded headers are correctly handled in your ABP applications.
Key Steps
1. Configure Forwarded Headers Middleware
In each ABP application's
Startup.cs(orProgram.csfor .NET 6+), add the Forwarded Headers Middleware at the top of the middleware pipeline:app.UseForwardedHeaders(new ForwardedHeadersOptions { ForwardedHeaders = ForwardedHeaders.XForwardedFor | ForwardedHeaders.XForwardedProto });This ensures the application correctly interprets the original request's scheme and host.
2. Reverse Proxy Path Mapping
Configure your reverse proxy to map paths as follows:
/api→ Host Server (https://localhost:44342)/auth→ Auth Server (https://localhost:44339)/→ Web Server (https://localhost:44378)
For example, in IIS, you can use URL Rewrite rules or in YARP (Yet Another Reverse Proxy) you can define routes in
appsettings.json.3. Update ABP Configuration
- Set
App:SelfUrl,AuthServer:Authority, andRemoteServices:Default:BaseUrlin each app'sappsettings.jsonto use the public-facing URL (https://localhost:44378). - Ensure CORS and redirect URIs are set to the single domain.
4. Test and Debug
- Make sure all static files, cookies, and authentication flows work as expected.
- If you encounter issues with authentication or redirects, double-check the forwarded headers and public URLs.
Reference
This approach is required for correct operation behind a reverse proxy, especially for authentication and URL generation.
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
-
0
[sghorakavi@cpat.com] said: It is not working. I tried this as wellhttps://abp.io/docs/latest/deployment/forwarded-headers
Hi, are you using nginx (or traefik) as a reverse proxy? By any chance, can you share your reverse-proxy configuration? I need more information and preferably brief explanation about what you've done so far, to better assist you.
Btw, adding forwarded-headers is really good, you should keep it in your module class. It makes sure URLs/Cookies are produced correctly behind the proxy, so it's needed.
-
0
Laucnchsettings.json { "iisSettings": { "windowsAuthentication": false, "anonymousAuthentication": true, "iisExpress": { "applicationUrl": "https://localhost:44356/hostapi", "sslPort": 44356 } }, "profiles": { "IIS Express": { "commandName": "IISExpress", "launchBrowser": true, "environmentVariables": { "ASPNETCORE_ENVIRONMENT": "Development", "DOTNET_WATCH": "false"
} }, "Approach.HttpApi.Host": { "commandName": "Project", "launchBrowser": true, "applicationUrl": "https://localhost:44356/hostapi", "environmentVariables": { "ASPNETCORE_ENVIRONMENT": "Development" } }} }
-added frowardheader
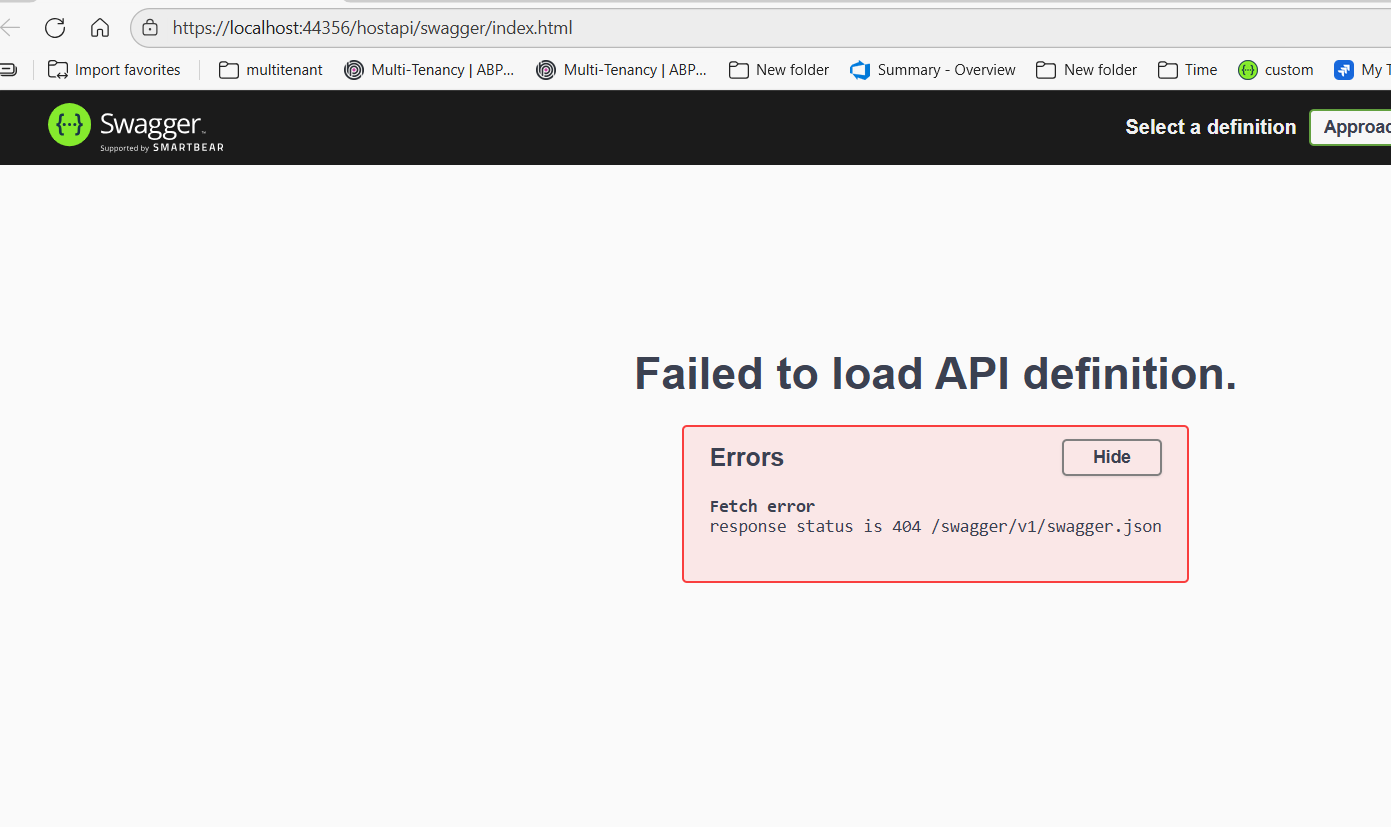
My swagger.json looks fine but swagger.html is not opening swagger.json. It cannot find hostapi in the path.
My appsettings.json has
"App": { "SelfUrl": "https://localhost:44356/hostapi", "CorsOrigins": "https://*.Approach.com;https://localhost:44356/hostapi", "DisablePII": false, "HealthCheckUrl": "/health-status" },
In the module:
app.UsePathBase("/hostapi");
app.UseAbpSwaggerUI(options => { options.SwaggerEndpoint("/swagger/v1/swagger.json", "Approach API"); options.RoutePrefix = "swagger";
var configuration = context.GetConfiguration(); options.OAuthClientId(configuration["AuthServer:SwaggerClientId"]);});
Can you pls let me know what did I miss. Do you need any other information ?
I started with sample ABP, MVC multi layer application. I need Host Service to open https://localhost:44356/hostapi/swagger/index.html properly. Thank you
-
0
[sghorakavi@cpat.com] said: Laucnchsettings.json { "iisSettings": { "windowsAuthentication": false, "anonymousAuthentication": true, "iisExpress": { "applicationUrl": "https://localhost:44356/hostapi", "sslPort": 44356 } }, "profiles": { "IIS Express": { "commandName": "IISExpress", "launchBrowser": true, "environmentVariables": { "ASPNETCORE_ENVIRONMENT": "Development", "DOTNET_WATCH": "false"
} }, "Approach.HttpApi.Host": { "commandName": "Project", "launchBrowser": true, "applicationUrl": "https://localhost:44356/hostapi", "environmentVariables": { "ASPNETCORE_ENVIRONMENT": "Development" } }} }
-added frowardheader
My swagger.json looks fine but swagger.html is not opening swagger.json. It cannot find hostapi in the path.
My appsettings.json has
"App": { "SelfUrl": "https://localhost:44356/hostapi", "CorsOrigins": "https://*.Approach.com;https://localhost:44356/hostapi", "DisablePII": false, "HealthCheckUrl": "/health-status" },
In the module:
app.UsePathBase("/hostapi");
app.UseAbpSwaggerUI(options => { options.SwaggerEndpoint("/swagger/v1/swagger.json", "Approach API"); options.RoutePrefix = "swagger";
var configuration = context.GetConfiguration(); options.OAuthClientId(configuration["AuthServer:SwaggerClientId"]);});
Can you pls let me know what did I miss. Do you need any other information ?
I started with sample ABP, MVC multi layer application. I need Host Service to open https://localhost:44356/hostapi/swagger/index.html properly. Thank you
Hi, I don't see any reverse-proxy configuration here. Instead, I only notice the code line
app.UsePathBase("/hostapi");, which sets the path-base and makes your application endpoints in the following format:/hostapi/<remaining-routes>And it seems this is not what you want, and I would not call it a reverse proxy, because it only sets the path-base and transforms the URLs. It does not redirect to an underlying service; for this purpose, you need a reverse proxy (If you need to expose all of your different apps that are running in different ports in the same port with distinct route configs, you need to use a reverse proxy like nginx, for example.)
An example config for nginx:
events {} http { server { listen 44378 ssl; server_name localhost; # 🔐 SSL certificate (use your own dev or real certs) (optional) ssl_certificate /path/to/dev-cert.pem; ssl_certificate_key /path/to/dev-key.pem; # Common headers proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; # Allow large bodies (optional) client_max_body_size 50m; # ===== /api → Host Server ===== location /api/ { proxy_pass https://localhost:44342/; proxy_ssl_verify off; } # ===== /auth → Auth Server ===== location /auth/ { proxy_pass https://localhost:44339/; proxy_ssl_verify off; } # ===== / → Web Server ===== location / { proxy_pass https://localhost:44378; proxy_ssl_verify off; } } }With this config, nginx ensures, when you send a request to the
https://localhost:44378/api, it redirects to the underlying service:https://localhost:44342.
If you just want to configure the hostpath, let me know, but in the current scenario you want, you need to use a reverse proxy.
-
0
Yes, I need to do this. Can you pls send me sample appsettings.json file for redirect to work in my case ?
My goal is to add reverse proxy to ABP MVC sample code to redirect hostapi url.
Note: I also tried this method with yarp revese proxy. Can you pls check.
``builder.Services.AddReverseProxy() .LoadFromConfig(builder.Configuration.GetSection("ReverseProxy"));
appsettiings.json goal is backend "https://localhost:44342/" redirect to "https://localhost:44356/hostapi""ReverseProxy": { "Routes": { "route1": { "ClusterId": "backend", "Match": { "Path": "/api/{**catch-all}" } } }, "Clusters": { "backend": { "Destinations": { "backend1": { "Address": "https://localhost:44342/" } } } } }``
-
0
[EngincanV] said:
[sghorakavi@cpat.com] said: Laucnchsettings.json
{
"iisSettings": {
"windowsAuthentication": false,
"anonymousAuthentication": true,
"iisExpress": {
"applicationUrl": "https://localhost:44356/hostapi",
"sslPort": 44356
}
},
"profiles": {
"IIS Express": {
"commandName": "IISExpress",
"launchBrowser": true,
"environmentVariables": {
"ASPNETCORE_ENVIRONMENT": "Development",
"DOTNET_WATCH": "false"} }, "Approach.HttpApi.Host": { "commandName": "Project", "launchBrowser": true, "applicationUrl": "https://localhost:44356/hostapi", "environmentVariables": { "ASPNETCORE_ENVIRONMENT": "Development" } }}
}-added frowardheader
My swagger.json looks fine but swagger.html is not opening swagger.json. It cannot find hostapi in the path.
My appsettings.json has
"App": {
"SelfUrl": "https://localhost:44356/hostapi",
"CorsOrigins": "https://*.Approach.com;https://localhost:44356/hostapi",
"DisablePII": false,
"HealthCheckUrl": "/health-status"
},In the module:
app.UsePathBase("/hostapi");
app.UseAbpSwaggerUI(options =>
{
options.SwaggerEndpoint("/swagger/v1/swagger.json", "Approach API");
options.RoutePrefix = "swagger";var configuration = context.GetConfiguration(); options.OAuthClientId(configuration["AuthServer:SwaggerClientId"]);});
Can you pls let me know what did I miss. Do you need any other information ?
I started with sample ABP, MVC multi layer application.
I need Host Service to open https://localhost:44356/hostapi/swagger/index.html properly.
Thank youHi, I don't see any reverse-proxy configuration here. Instead, I only notice the code line
app.UsePathBase("/hostapi");, which sets the path-base and makes your application endpoints in the following format:/hostapi/<remaining-routes>And it seems this is not what you want, and I would not call it a reverse proxy, because it only sets the path-base and transforms the URLs. It does not redirect to an underlying service; for this purpose, you need a reverse proxy (If you need to expose all of your different apps that are running in different ports in the same port with distinct route configs, you need to use a reverse proxy like nginx, for example.)
An example config for nginx:
events {} http { server { listen 44378 ssl; server_name localhost; # 🔐 SSL certificate (use your own dev or real certs) (optional) ssl_certificate /path/to/dev-cert.pem; ssl_certificate_key /path/to/dev-key.pem; # Common headers proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; # Allow large bodies (optional) client_max_body_size 50m; # ===== /api → Host Server ===== location /api/ { proxy_pass https://localhost:44342/; proxy_ssl_verify off; } # ===== /auth → Auth Server ===== location /auth/ { proxy_pass https://localhost:44339/; proxy_ssl_verify off; } # ===== / → Web Server ===== location / { proxy_pass https://localhost:44378; proxy_ssl_verify off; } } }With this config, nginx ensures, when you send a request to the
https://localhost:44378/api, it redirects to the underlying service:https://localhost:44342.
If you just want to configure the hostpath, let me know, but in the current scenario you want, you need to use a reverse proxy.
Ok, I have nginx setup on my windows computer for reverse proxy. Still getting same error: I am trying to fix hostapi now. aspnetcore-browser-refresh.js and rest of the files did not get BasePath variable. I am using windows. Attached is my basic nginx.config file. Please let me know where is the issue `#user nobody; worker_processes 1;
#error_log logs/error.log; #error_log logs/error.log notice; #error_log logs/error.log info;
#pid logs/nginx.pid;
events { worker_connections 1024; }
http { include mime.types; default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" ' # '$status $body_bytes_sent "$http_referer" ' # '"$http_user_agent" "$http_x_forwarded_for"'; #access_log logs/access.log main; sendfile on; #tcp_nopush on; #keepalive_timeout 0; keepalive_timeout 65; #gzip on; server { listen 8080; server_name localhost; #charset koi8-r; #access_log logs/host.access.log main; location / { root html; index index.html index.htm; } # Reverse proxy to your ABP Host API app location /hostapi/ { proxy_pass https://localhost:44356; proxy_http_version 1.1; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; # WebSocket / Hot Reload support proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } #error_page 404 /404.html; # redirect server error pages to the static page /50x.html # error_page 500 502 503 504 /50x.html; location = /50x.html { root html; } # proxy the PHP scripts to Apache listening on 127.0.0.1:80 # #location ~ \.php$ { # proxy_pass http://127.0.0.1; #} # pass the PHP scripts to FastCGI server listening on 127.0.0.1:9000 # #location ~ \.php$ { # root html; # fastcgi_pass 127.0.0.1:9000; # fastcgi_index index.php; # fastcgi_param SCRIPT_FILENAME /scripts$fastcgi_script_name; # include fastcgi_params; #} # deny access to .htaccess files, if Apache's document root # concurs with nginx's one # #location ~ /\.ht { # deny all; #} } # another virtual host using mix of IP-, name-, and port-based configuration # #server { # listen 8000; # listen somename:8080; # server_name somename alias another.alias; # location / { # root html; # index index.html index.htm; # } #} # HTTPS server # #server { # listen 443 ssl; # server_name localhost; # ssl_certificate cert.pem; # ssl_certificate_key cert.key; # ssl_session_cache shared:SSL:1m; # ssl_session_timeout 5m; # ssl_ciphers HIGH:!aNULL:!MD5; # ssl_prefer_server_ciphers on; # location / { # root html; # index index.html index.htm; # } #}} `
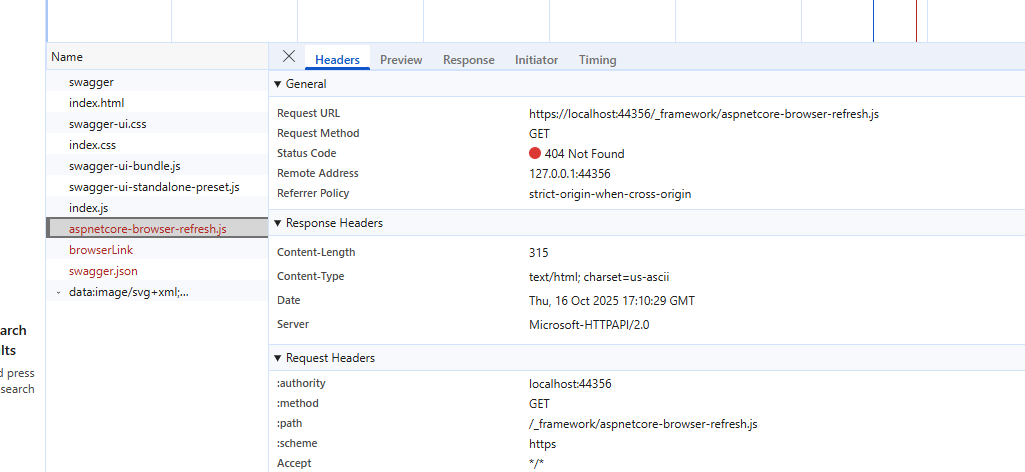
Output from ABP: Index.js got hostapi in the path fine but aspnetcore-browser-refresh.js is missing hostapi in the URL.
-
0
[EngincanV] said:
[sghorakavi@cpat.com] said: Laucnchsettings.json{"iisSettings": {"windowsAuthentication": false,"anonymousAuthentication": true,"iisExpress": {"applicationUrl": "https://localhost:44356/hostapi","sslPort": 44356}},"profiles": {"IIS Express": {"commandName": "IISExpress","launchBrowser": true,"environmentVariables": {"ASPNETCORE_ENVIRONMENT": "Development","DOTNET_WATCH": "false"
} }, "Approach.HttpApi.Host": { "commandName": "Project", "launchBrowser": true, "applicationUrl": "https://localhost:44356/hostapi", "environmentVariables": { "ASPNETCORE_ENVIRONMENT": "Development" } }}}
-added frowardheader
My swagger.json looks fine but swagger.html is not opening swagger.json. It cannot find hostapi in the path.
My appsettings.json has
"App": {"SelfUrl": "https://localhost:44356/hostapi","CorsOrigins": "https://*.Approach.com;https://localhost:44356/hostapi","DisablePII": false,"HealthCheckUrl": "/health-status"},
In the module:
app.UsePathBase("/hostapi");
app.UseAbpSwaggerUI(options =>{options.SwaggerEndpoint("/swagger/v1/swagger.json", "Approach API");options.RoutePrefix = "swagger";
var configuration = context.GetConfiguration(); options.OAuthClientId(configuration["AuthServer:SwaggerClientId"]);});
Can you pls let me know what did I miss. Do you need any other information ?
I started with sample ABP, MVC multi layer application.I need Host Service to open https://localhost:44356/hostapi/swagger/index.html properly.Thank you
Hi, I don't see any reverse-proxy configuration here. Instead, I only notice the code line
app.UsePathBase("/hostapi");, which sets the path-base and makes your application endpoints in the following format:/hostapi/<remaining-routes>And it seems this is not what you want, and I would not call it a reverse proxy, because it only sets the path-base and transforms the URLs. It does not redirect to an underlying service; for this purpose, you need a reverse proxy (If you need to expose all of your different apps that are running in different ports in the same port with distinct route configs, you need to use a reverse proxy like nginx, for example.)
An example config for nginx:
events {} http { server { listen 44378 ssl; server_name localhost; # 🔐 SSL certificate (use your own dev or real certs) (optional) ssl_certificate /path/to/dev-cert.pem; ssl_certificate_key /path/to/dev-key.pem; # Common headers proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; # Allow large bodies (optional) client_max_body_size 50m; # ===== /api → Host Server ===== location /api/ { proxy_pass https://localhost:44342/; proxy_ssl_verify off; } # ===== /auth → Auth Server ===== location /auth/ { proxy_pass https://localhost:44339/; proxy_ssl_verify off; } # ===== / → Web Server ===== location / { proxy_pass https://localhost:44378; proxy_ssl_verify off; } } }With this config, nginx ensures, when you send a request to the
https://localhost:44378/api, it redirects to the underlying service:https://localhost:44342.
If you just want to configure the hostpath, let me know, but in the current scenario you want, you need to use a reverse proxy.
Ok, I have nginx setup on my windows computer. The host server is working fine. There is authentication issue. After adding reverse proxy using nginx, I see this issue. Any suggestion ?
-
0
[sghorakavi@cpat.com] said:
[EngincanV] said:
[sghorakavi@cpat.com] said: Laucnchsettings.json{"iisSettings": {"windowsAuthentication": false,"anonymousAuthentication": true,"iisExpress": {"applicationUrl": "https://localhost:44356/hostapi","sslPort": 44356}},"profiles": {"IIS Express": {"commandName": "IISExpress","launchBrowser": true,"environmentVariables": {"ASPNETCORE_ENVIRONMENT": "Development","DOTNET_WATCH": "false"
} }, "Approach.HttpApi.Host": { "commandName": "Project", "launchBrowser": true, "applicationUrl": "https://localhost:44356/hostapi", "environmentVariables": { "ASPNETCORE_ENVIRONMENT": "Development" } }}}
-added frowardheader
My swagger.json looks fine but swagger.html is not opening swagger.json. It cannot find hostapi in the path.
My appsettings.json has
"App": {"SelfUrl": "https://localhost:44356/hostapi","CorsOrigins": "https://*.Approach.com;https://localhost:44356/hostapi","DisablePII": false,"HealthCheckUrl": "/health-status"},
In the module:
app.UsePathBase("/hostapi");
app.UseAbpSwaggerUI(options =>{options.SwaggerEndpoint("/swagger/v1/swagger.json", "Approach API");options.RoutePrefix = "swagger";
var configuration = context.GetConfiguration(); options.OAuthClientId(configuration["AuthServer:SwaggerClientId"]);});
Can you pls let me know what did I miss. Do you need any other information ?
I started with sample ABP, MVC multi layer application.I need Host Service to open https://localhost:44356/hostapi/swagger/index.html properly.Thank you
Hi, I don't see any reverse-proxy configuration here. Instead, I only notice the code line
app.UsePathBase("/hostapi");, which sets the path-base and makes your application endpoints in the following format:/hostapi/<remaining-routes>And it seems this is not what you want, and I would not call it a reverse proxy, because it only sets the path-base and transforms the URLs. It does not redirect to an underlying service; for this purpose, you need a reverse proxy (If you need to expose all of your different apps that are running in different ports in the same port with distinct route configs, you need to use a reverse proxy like nginx, for example.)
An example config for nginx:
events {} http { server { listen 44378 ssl; server_name localhost; # 🔐 SSL certificate (use your own dev or real certs) (optional) ssl_certificate /path/to/dev-cert.pem; ssl_certificate_key /path/to/dev-key.pem; # Common headers proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; # Allow large bodies (optional) client_max_body_size 50m; # ===== /api → Host Server ===== location /api/ { proxy_pass https://localhost:44342/; proxy_ssl_verify off; } # ===== /auth → Auth Server ===== location /auth/ { proxy_pass https://localhost:44339/; proxy_ssl_verify off; } # ===== / → Web Server ===== location / { proxy_pass https://localhost:44378; proxy_ssl_verify off; } } }With this config, nginx ensures, when you send a request to the
https://localhost:44378/api, it redirects to the underlying service:https://localhost:44342.
If you just want to configure the hostpath, let me know, but in the current scenario you want, you need to use a reverse proxy.
Ok, I have nginx setup on my windows computer. The host server is working fine. There is authentication issue. After adding reverse proxy using nginx, I see this issue. Any suggestion ?
Hi, your nginx config seems right. To address the problem in your auth-server project, can you share its logs, please?
-
0
Thank you, Here is the log information. I took code from sample project and adding reverse proxy. Now UI is showing all types of authorization. I want to show one only one type.
10/17/2025 9:38:34 PM [Debug] Executing HealthCheck collector HostedService. 10/17/2025 9:38:34 PM [Information] Start processing HTTP request "GET" "https://localhost:44356/AUTH/health-status" 10/17/2025 9:38:34 PM [Information] Sending HTTP request "GET" "https://localhost:44356/AUTH/health-status" 10/17/2025 9:38:34 PM [Information] Request starting "HTTP/1.1" "GET" "https"://"localhost:44356""/AUTH""/health-status""" - null null 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ValidateHostHeader". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateValidatedTokens". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromAuthorizationHeader". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromBodyForm". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromQueryString". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was marked as rejected by "OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens". 10/17/2025 9:38:34 PM [Debug] AuthenticationScheme: "OpenIddict.Validation.AspNetCore" was not authenticated. 10/17/2025 9:38:34 PM [Information] Executing endpoint '"Health checks"' 10/17/2025 9:38:34 PM [Information] Executed endpoint '"Health checks"' 10/17/2025 9:38:34 PM [Information] Request finished "HTTP/1.1" "GET" "https"://"localhost:44356""/AUTH""/health-status""" - 200 null "application/json" 7.6449ms 10/17/2025 9:38:34 PM [Information] Received HTTP response headers after 76.3202ms - 200 10/17/2025 9:38:34 PM [Information] End processing HTTP request after 76.6487ms - 200 10/17/2025 9:38:34 PM [Debug] HealthReportCollector - health report execution history saved. 10/17/2025 9:38:34 PM [Debug] HealthReport history already exists and is in the same state, updating the values. 10/17/2025 9:38:34 PM [Debug] HealthReportCollector has completed. 10/17/2025 9:38:34 PM [Debug] HealthCheck collector HostedService executed successfully. 10/17/2025 9:38:44 PM [Debug] Executing HealthCheck collector HostedService. 10/17/2025 9:38:44 PM [Information] Start processing HTTP request "GET" "https://localhost:44356/AUTH/health-status" 10/17/2025 9:38:44 PM [Information] Sending HTTP request "GET" "https://localhost:44356/AUTH/health-status" 10/17/2025 9:38:44 PM [Information] Request starting "HTTP/1.1" "GET" "https"://"localhost:44356""/AUTH""/health-status""" - null null 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ValidateHostHeader". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateValidatedTokens". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromAuthorizationHeader". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromBodyForm". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromQueryString". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was marked as rejected by "OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens". 10/17/2025 9:38:44 PM [Debug] AuthenticationScheme: "OpenIddict.Validation.AspNetCore" was not authenticated. 10/17/2025 9:38:44 PM [Information] Executing endpoint '"Health checks"'
-
0
[EngincanV] said:
[sghorakavi@cpat.com] said: Laucnchsettings.json
{
"iisSettings": {
"windowsAuthentication": false,
"anonymousAuthentication": true,
"iisExpress": {
"applicationUrl": "https://localhost:44356/hostapi",
"sslPort": 44356
}
},
"profiles": {
"IIS Express": {
"commandName": "IISExpress",
"launchBrowser": true,
"environmentVariables": {
"ASPNETCORE_ENVIRONMENT": "Development",
"DOTNET_WATCH": "false"} }, "Approach.HttpApi.Host": { "commandName": "Project", "launchBrowser": true, "applicationUrl": "https://localhost:44356/hostapi", "environmentVariables": { "ASPNETCORE_ENVIRONMENT": "Development" } }}
}-added frowardheader
My swagger.json looks fine but swagger.html is not opening swagger.json. It cannot find hostapi in the path.
My appsettings.json has
"App": {
"SelfUrl": "https://localhost:44356/hostapi",
"CorsOrigins": "https://*.Approach.com;https://localhost:44356/hostapi",
"DisablePII": false,
"HealthCheckUrl": "/health-status"
},In the module:
app.UsePathBase("/hostapi");
app.UseAbpSwaggerUI(options =>
{
options.SwaggerEndpoint("/swagger/v1/swagger.json", "Approach API");
options.RoutePrefix = "swagger";var configuration = context.GetConfiguration(); options.OAuthClientId(configuration["AuthServer:SwaggerClientId"]);});
Can you pls let me know what did I miss. Do you need any other information ?
I started with sample ABP, MVC multi layer application.
I need Host Service to open https://localhost:44356/hostapi/swagger/index.html properly.
Thank youHi, I don't see any reverse-proxy configuration here. Instead, I only notice the code line
app.UsePathBase("/hostapi");, which sets the path-base and makes your application endpoints in the following format:/hostapi/<remaining-routes>And it seems this is not what you want, and I would not call it a reverse proxy, because it only sets the path-base and transforms the URLs. It does not redirect to an underlying service; for this purpose, you need a reverse proxy (If you need to expose all of your different apps that are running in different ports in the same port with distinct route configs, you need to use a reverse proxy like nginx, for example.)
An example config for nginx:
events {} http { server { listen 44378 ssl; server_name localhost; # 🔐 SSL certificate (use your own dev or real certs) (optional) ssl_certificate /path/to/dev-cert.pem; ssl_certificate_key /path/to/dev-key.pem; # Common headers proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; # Allow large bodies (optional) client_max_body_size 50m; # ===== /api → Host Server ===== location /api/ { proxy_pass https://localhost:44342/; proxy_ssl_verify off; } # ===== /auth → Auth Server ===== location /auth/ { proxy_pass https://localhost:44339/; proxy_ssl_verify off; } # ===== / → Web Server ===== location / { proxy_pass https://localhost:44378; proxy_ssl_verify off; } } }With this config, nginx ensures, when you send a request to the
https://localhost:44378/api, it redirects to the underlying service:https://localhost:44342.
If you just want to configure the hostpath, let me know, but in the current scenario you want, you need to use a reverse proxy.
Ok, I have nginx setup on my windows computer.
10/17/2025 9:38:34 PM [Debug] Executing HealthCheck collector HostedService. 10/17/2025 9:38:34 PM [Information] Start processing HTTP request "GET" "https://localhost:44356/AUTH/health-status" 10/17/2025 9:38:34 PM [Information] Sending HTTP request "GET" "https://localhost:44356/AUTH/health-status" 10/17/2025 9:38:34 PM [Information] Request starting "HTTP/1.1" "GET" "https"://"localhost:44356""/AUTH""/health-status""" - null null 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ValidateHostHeader". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateValidatedTokens". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromAuthorizationHeader". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromBodyForm". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromQueryString". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens". 10/17/2025 9:38:34 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was marked as rejected by "OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens". 10/17/2025 9:38:34 PM [Debug] AuthenticationScheme: "OpenIddict.Validation.AspNetCore" was not authenticated. 10/17/2025 9:38:34 PM [Information] Executing endpoint '"Health checks"' 10/17/2025 9:38:34 PM [Information] Executed endpoint '"Health checks"' 10/17/2025 9:38:34 PM [Information] Request finished "HTTP/1.1" "GET" "https"://"localhost:44356""/AUTH""/health-status""" - 200 null "application/json" 7.6449ms 10/17/2025 9:38:34 PM [Information] Received HTTP response headers after 76.3202ms - 200 10/17/2025 9:38:34 PM [Information] End processing HTTP request after 76.6487ms - 200 10/17/2025 9:38:34 PM [Debug] HealthReportCollector - health report execution history saved. 10/17/2025 9:38:34 PM [Debug] HealthReport history already exists and is in the same state, updating the values. 10/17/2025 9:38:34 PM [Debug] HealthReportCollector has completed. 10/17/2025 9:38:34 PM [Debug] HealthCheck collector HostedService executed successfully. 10/17/2025 9:38:44 PM [Debug] Executing HealthCheck collector HostedService. 10/17/2025 9:38:44 PM [Information] Start processing HTTP request "GET" "https://localhost:44356/AUTH/health-status" 10/17/2025 9:38:44 PM [Information] Sending HTTP request "GET" "https://localhost:44356/AUTH/health-status" 10/17/2025 9:38:44 PM [Information] Request starting "HTTP/1.1" "GET" "https"://"localhost:44356""/AUTH""/health-status""" - null null 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext" was successfully processed by "OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ValidateHostHeader". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateValidatedTokens". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromAuthorizationHeader". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromBodyForm". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromQueryString". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was successfully processed by "OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens". 10/17/2025 9:38:44 PM [Debug] The event "OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext" was marked as rejected by "OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens". 10/17/2025 9:38:44 PM [Debug] AuthenticationScheme: "OpenIddict.Validation.AspNetCore" was not authenticated. 10/17/2025 9:38:44 PM [Information] Executing endpoint '"Health checks"'
-
0
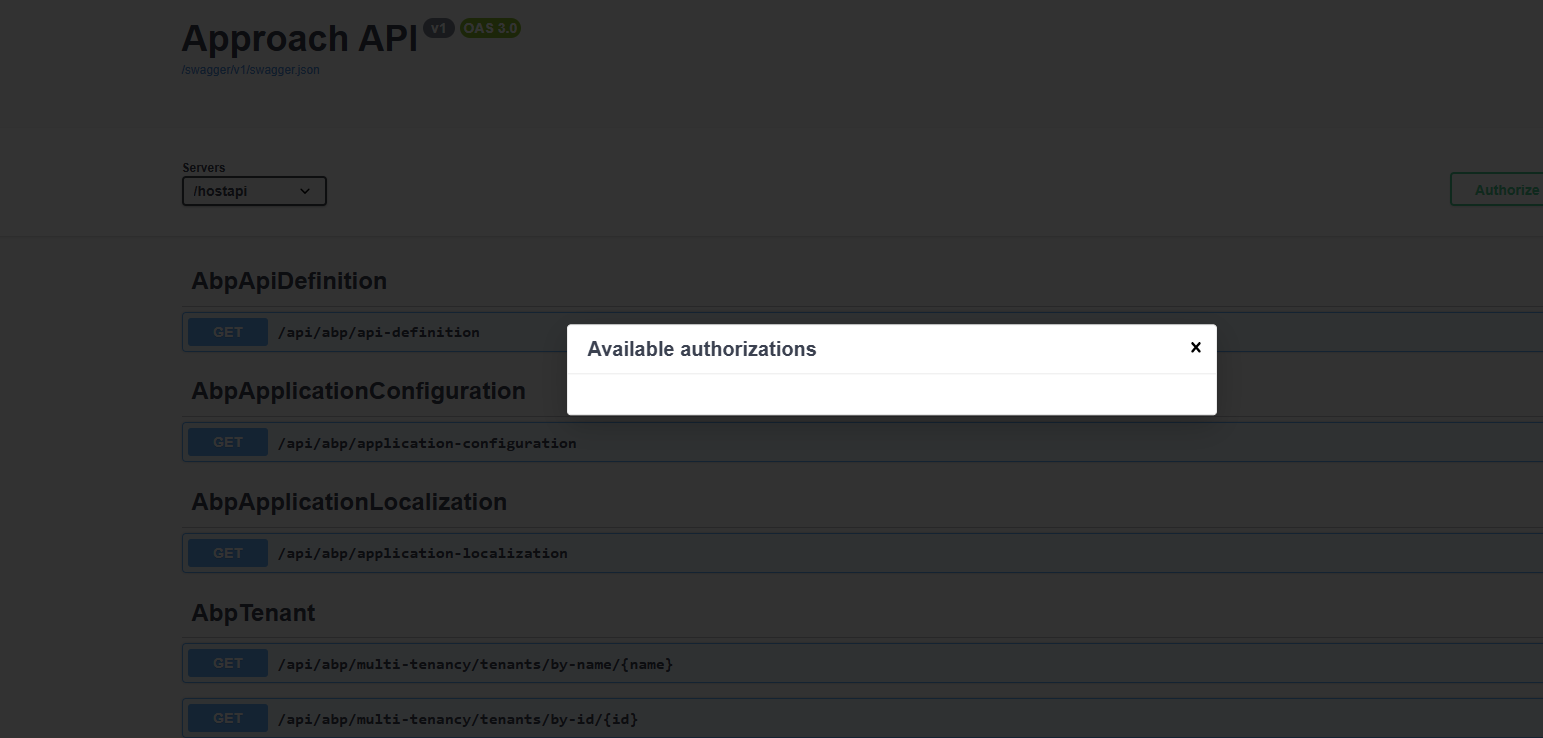
Here is the latest update: changed RequireHttpsMetadata in appsettings.json of host to false: "AuthServer": { "Authority": "https://localhost:44356/auth", "RequireHttpsMetadata": false, "MetaAddress": "https://localhost:44356/auth", "SwaggerClientId": "Approach_Swagger" }, Now it shows may auths : When I select one get following error:
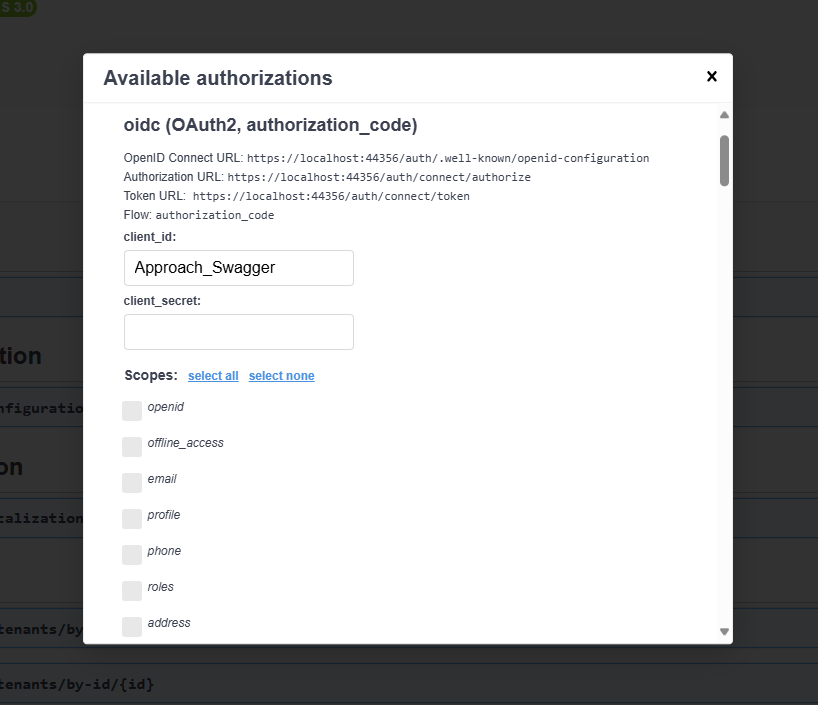
Does ABP support same port with multiple extensions like below
https://localhost:44356/auth -- auth server https://localhost:44356/hostapi - hostapi server https://localhost:44356 - web server
Thank you
-
0
Can you pls send me ABP MVC multi layer sample that can handle above port situation ? We are planning to use one domain and we will use reverse proxy.
https://localhost:44356/auth -- auth server https://localhost:44356/hostapi - hostapi server https://localhost:44356 - web server
Thank you
-
0
[sghorakavi@cpat.com] said: Can you pls send me ABP MVC multi layer sample that can handle above port situation ? We are planning to use one domain and we will use reverse proxy.
https://localhost:44356/auth -- auth server https://localhost:44356/hostapi - hostapi server https://localhost:44356 - web server
Thank you
Hi, actually, this is not fully related to ABP, but it's related to your application and nginx configs. So, you may need to work on that manually. However, I can explain what should be done step by step and clarify some steps for you:
- Call the following middleware before other middlewares in your application (it should already be configured in your auth-server project):
app.UseForwardedHeaders(new ForwardedHeadersOptions { ForwardedHeaders = ForwardedHeaders.XForwardedFor | ForwardedHeaders.XForwardedProto });- You basically need 4 ports: one for nginx (front), web, auth-server and hostapi. (I assume:
44356for nginx-front side, and then44378for web ,44339for auth-server and44342for hostapi). Configure your nginx.config file accordingly:
events {} http { server { listen 44356; location / { proxy_pass http://localhost:44378; } location /auth/ { proxy_pass http://localhost:44339/; } location /hostapi/ { proxy_pass http://localhost:44342/; } } }- Update the relevant
appsettings.jsonfiles for each project:
Web:
{ "App": { "SelfUrl": "https://localhost:44356", //UPDATED "DisablePII": false, "HealthCheckUrl": "/health-status" }, "RemoteServices": { "Default": { "BaseUrl": "https://localhost:44356/hostapi/" //UPDATED }, "AbpAccountPublic": { "BaseUrl": "https://localhost:44356/auth/" //UPDATED } }, "AuthServer": { "Authority": "https://localhost:44356/auth", //UPDATED "RequireHttpsMetadata": true, "ClientId": "AbpNginxDemo_Web", "ClientSecret": "1q2w3e*" }, }Auth-server (optional, and also update cors-origins accordingly):
"App": { "SelfUrl": "https://localhost:44356/auth", //... }, "AuthServer": { "Authority": "https://localhost:44356/auth" }HttpApiHost:
{ "App": { "SelfUrl": "https://localhost:44356/hostapi", //... }, "AuthServer": { "Authority": "https://localhost:44356/auth", "RequireHttpsMetadata": true, "MetaAddress": "https://localhost:44356/auth", //... }, }- Then, if your configurations are correct, it should work as expected.
Also, for this problem, the IIS page means you’re trying to run more than one ASP.NET Core app “in-process” in the same IIS Application Pool, which isn’t supported. You can search for this error on Stack Overflow and see the possible solutions.
Regards.
-
0
[EngincanV] said:
[sghorakavi@cpat.com] said: Can you pls send me ABP MVC multi layer sample that can handle above port situation ? We are planning to use one domain and we will use reverse proxy.
https://localhost:44356/auth -- auth server
https://localhost:44356/hostapi - hostapi server
https://localhost:44356 - web serverThank you
Hi, actually, this is not fully related to ABP, but it's related to your application and nginx configs. So, you may need to work on that manually. However, I can explain what should be done step by step and clarify some steps for you:
- Call the following middleware before other middlewares in your application (it should already be configured in your auth-server project):
app.UseForwardedHeaders(new ForwardedHeadersOptions { ForwardedHeaders = ForwardedHeaders.XForwardedFor | ForwardedHeaders.XForwardedProto });- You basically need 4 ports: one for nginx (front), web, auth-server and hostapi. (I assume:
44356for nginx-front side, and then44378for web ,44339for auth-server and44342for hostapi). Configure your nginx.config file accordingly:
events {} http { server { listen 44356; location / { proxy_pass http://localhost:44378; } location /auth/ { proxy_pass http://localhost:44339/; } location /hostapi/ { proxy_pass http://localhost:44342/; } } }- Update the relevant
appsettings.jsonfiles for each project:
Web:
{ "App": { "SelfUrl": "https://localhost:44356", //UPDATED "DisablePII": false, "HealthCheckUrl": "/health-status" }, "RemoteServices": { "Default": { "BaseUrl": "https://localhost:44356/hostapi/" //UPDATED }, "AbpAccountPublic": { "BaseUrl": "https://localhost:44356/auth/" //UPDATED } }, "AuthServer": { "Authority": "https://localhost:44356/auth", //UPDATED "RequireHttpsMetadata": true, "ClientId": "AbpNginxDemo_Web", "ClientSecret": "1q2w3e*" }, }Auth-server (optional, and also update cors-origins accordingly):
"App": { "SelfUrl": "https://localhost:44356/auth", //... }, "AuthServer": { "Authority": "https://localhost:44356/auth" }HttpApiHost:
{ "App": { "SelfUrl": "https://localhost:44356/hostapi", //... }, "AuthServer": { "Authority": "https://localhost:44356/auth", "RequireHttpsMetadata": true, "MetaAddress": "https://localhost:44356/auth", //... }, }- Then, if your configurations are correct, it should work as expected.
Also, for this problem, the IIS page means you’re trying to run more than one ASP.NET Core app “in-process” in the same IIS Application Pool, which isn’t supported. You can search for this error on Stack Overflow and see the possible solutions.
Regards.
Based on this, I need to have 4 ports. Let me try this. I was attempting to use single port.
Sudha
You basically need 4 ports: one for nginx (front), web, auth-server and hostapi. (I assume: 44356 for nginx-front side, and then 44378 for web , 44339 for auth-server and 44342 for hostapi). Configure your nginx.config file accordingly:
events {}
http { server { listen 44356;
location / { proxy_pass http://localhost:44378; } location /auth/ { proxy_pass http://localhost:44339/; } location /hostapi/ { proxy_pass http://localhost:44342/; } }}
-
0
Yes, you need to have 4 routes. In the front-facing route, nginx should listen and forward to the related underlying service.
-
0
[EngincanV] said: Yes, you need to have 4 routes. In the front-facing route, nginx should listen and forward to the related underlying service.
Can you pls review nginx reverse proxy? It is not working as planned.
#user nobody; worker_processes 1; #error_log logs/error.log; #error_log logs/error.log notice; #error_log logs/error.log info; #pid logs/nginx.pid; events { worker_connections 1024; } http { include mime.types; default_type application/octet-stream; #log_format main '$remote_addr - $remote_user [$time_local] "$request" ' # '$status $body_bytes_sent "$http_referer" ' # '"$http_user_agent" "$http_x_forwarded_for"'; #access_log logs/access.log main; sendfile on; #tcp_nopush on; #keepalive_timeout 0; keepalive_timeout 65; #gzip on; server { listen 44500; server_name localhost; #charset koi8-r; #access_log logs/host.access.log main; location / { root html; index index.html index.htm; proxy_pass https://localhost:44385; proxy_ssl_verify off; } # Reverse proxy to your ABP Host API app location /hostapi/ { proxy_pass https://localhost:44348; proxy_http_version 1.1; proxy_ssl_verify off; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Forwarded-Prefix /hostapi; # WebSocket / Hot Reload support proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } location /auth/ { proxy_pass https://localhost:44394; proxy_http_version 1.1; proxy_ssl_verify off; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Forwarded-Prefix /hostapi; # WebSocket / Hot Reload support proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } #error_page 404 /404.html; # redirect server error pages to the static page /50x.html # error_page 500 502 503 504 /50x.html; location = /50x.html { root html; } } }Added forward header option in host module
I am attempting to invoke: https://localhost:44500 - web https://localhost:44500/hostapi - host api https://localhost:44500/auth - Auth
-
0
[sghorakavi@cpat.com] said:
[EngincanV] said: Yes, you need to have 4 routes. In the front-facing route, nginx should listen and forward to the related underlying service.
Can you pls review nginx reverse proxy? It is not working as planned.
#user nobody; worker_processes 1; #error_log logs/error.log; #error_log logs/error.log notice; #error_log logs/error.log info; #pid logs/nginx.pid; events { worker_connections 1024; } http { include mime.types; default_type application/octet-stream; #log_format main '$remote_addr - $remote_user [$time_local] "$request" ' # '$status $body_bytes_sent "$http_referer" ' # '"$http_user_agent" "$http_x_forwarded_for"'; #access_log logs/access.log main; sendfile on; #tcp_nopush on; #keepalive_timeout 0; keepalive_timeout 65; #gzip on; server { listen 44500; server_name localhost; #charset koi8-r; #access_log logs/host.access.log main; location / { root html; index index.html index.htm; proxy_pass https://localhost:44385; proxy_ssl_verify off; } # Reverse proxy to your ABP Host API app location /hostapi/ { proxy_pass https://localhost:44348; proxy_http_version 1.1; proxy_ssl_verify off; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Forwarded-Prefix /hostapi; # WebSocket / Hot Reload support proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } location /auth/ { proxy_pass https://localhost:44394; proxy_http_version 1.1; proxy_ssl_verify off; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Forwarded-Prefix /hostapi; # WebSocket / Hot Reload support proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } #error_page 404 /404.html; # redirect server error pages to the static page /50x.html # error_page 500 502 503 504 /50x.html; location = /50x.html { root html; } } }Added forward header option in host module
I am attempting to invoke: https://localhost:44500 - web https://localhost:44500/hostapi - host api https://localhost:44500/auth - Auth
Hi, it seems there are a few mistakes in the nginx.config:
- In /auth route forwarding, you have used a line:
proxy_set_header X-Forwarded-Prefix /hostapi, it should beproxy_set_header X-Forwarded-Prefix /auth - You should use a trailing slash at the end of proxy_pass lines:
proxy_pass https://localhost:44348/;
#user nobody; worker_processes 1; #error_log logs/error.log; #error_log logs/error.log notice; #error_log logs/error.log info; #pid logs/nginx.pid; events { worker_connections 1024; } http { include mime.types; default_type application/octet-stream; #log_format main '$remote_addr - $remote_user [$time_local] "$request" ' # '$status $body_bytes_sent "$http_referer" ' # '"$http_user_agent" "$http_x_forwarded_for"'; #access_log logs/access.log main; sendfile on; #tcp_nopush on; #keepalive_timeout 0; keepalive_timeout 65; #gzip on; server { listen 44500; server_name localhost; #charset koi8-r; #access_log logs/host.access.log main; # Redirect no-trailing-slash to with-slash so the /hostapi/ and /auth/ blocks match location = /hostapi { return 301 /hostapi/; } location = /auth { return 301 /auth/; } location / { proxy_pass https://localhost:44385/; proxy_http_version 1.1; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; proxy_ssl_verify off; } # Reverse proxy to your ABP Host API app location /hostapi/ { proxy_pass https://localhost:44348/; proxy_http_version 1.1; proxy_ssl_verify off; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Forwarded-Prefix /hostapi; # WebSocket / Hot Reload support proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } location /auth/ { proxy_pass https://localhost:44394/; proxy_http_version 1.1; proxy_ssl_verify off; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Forwarded-Prefix /auth; # WebSocket / Hot Reload support proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } #error_page 404 /404.html; # redirect server error pages to the static page /50x.html # error_page 500 502 503 504 /50x.html; location = /50x.html { root html; } } }Also, ensure you made the correct configs in the appsettings.json files for your projects.
- In /auth route forwarding, you have used a line: