Hello,
Our project underwent a penetration test. In the test result, it is suggested that our project needs to stop responding for tokens without an encryption algorithm. Which means that, it should not allow access for the tokens that have "alg": "none" in their headers.
How can we implement this in our project? Will it break anything related to ABP framework, authentication, authorization etc.?
Thanks!
6 Answer(s)
-
0
To deny access for JWT tokens with
"alg": "none"in their headers, you should rely on the default behavior of the JWT Bearer authentication middleware used by ABP (which is based on ASP.NET Core and Microsoft.IdentityModel). By default, the middleware will reject tokens with"alg": "none"and will not treat them as valid, as this is a well-known security risk.No additional configuration is required in ABP or ASP.NET Core to block
"alg": "none"tokens, unless you have custom code that overrides the default token validation behavior. As long as you use the standardAddJwtBearerorAddAbpJwtBearersetup, tokens with"alg": "none"will be denied.Example configuration (default, secure):
context.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme) .AddJwtBearer(options => { options.Authority = "https://your-auth-server"; options.Audience = "YourAudience"; // No need to add custom logic for "alg": "none" });If you have not customized the token validation pipeline to allow
"alg": "none", your application is already protected. Allowing"alg": "none"would require explicit, insecure customization, which is not present in ABP's default templates.This will not break any ABP authentication or authorization features, as rejecting
"alg": "none"is the secure and expected behavior.Sources:
- https://abp.io/community/articles/4u3wrbs5
- https://learn.microsoft.com/en-us/aspnet/core/security/authentication/configure-jwt-bearer-authentication
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
We do not have the code block that is given by the AI-Bot. Moreover, I have created a new project and it does not have this block neither.
-
0
Hi, you can ignore the response of the AI bot.
If you open your
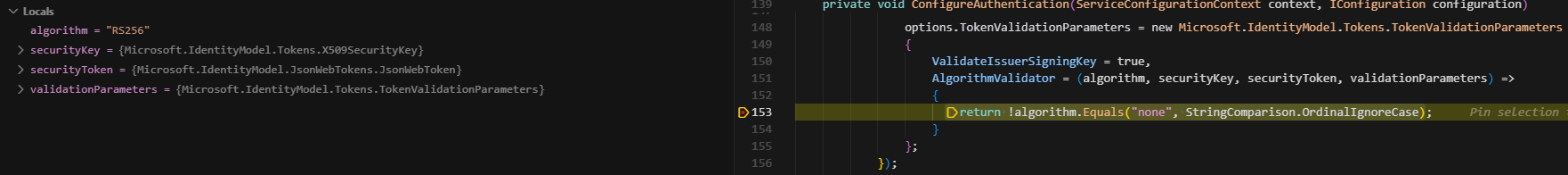
*HttpApi.Hostproject and search for theConfigureAuthenticationmethod, then you'll notice there is a configuration as follows:private void ConfigureAuthentication(ServiceConfigurationContext context, IConfiguration configuration) { context.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme) .AddAbpJwtBearer(options => { options.Authority = configuration["AuthServer:Authority"]; options.RequireHttpsMetadata = configuration.GetValue<bool>("AuthServer:RequireHttpsMetadata"); options.Audience = "<your-project-name>"; //WRITE THE BELOW CODE HERE!!! }); context.Services.Configure<AbpClaimsPrincipalFactoryOptions>(options => { options.IsDynamicClaimsEnabled = true; }); }Here, you can configure
TokenValidationParametersand make the relevant validations for the token. In your case, a code like this should work:options.TokenValidationParameters = new Microsoft.IdentityModel.Tokens.TokenValidationParameters { ValidateIssuerSigningKey = true, AlgorithmValidator = (algorithm, securityKey, securityToken, validationParameters) => { return !algorithm.Equals("none", StringComparison.OrdinalIgnoreCase); } };AlgorithmValidatorchecks if the alg header is as expected with the specified algorithm or not. -
0
Hi EngincanV,
The code that you provided for the method is not like this in my project and the new project that is created with the version 9.3.5 recently. The following is how the particular method is created:
private void ConfigureAuthentication(ServiceConfigurationContext context) { context.Services.ForwardIdentityAuthenticationForBearer( OpenIddictValidationAspNetCoreDefaults.AuthenticationScheme ); context.Services.Configure<AbpClaimsPrincipalFactoryOptions>(options => { options.IsDynamicClaimsEnabled = true; }); } -
0
[kkmy] said: Hi EngincanV,
The code that you provided for the method is not like this in my project and the new project that is created with the version 9.3.5 recently. The following is how the particular method is created:
private void ConfigureAuthentication(ServiceConfigurationContext context) { context.Services.ForwardIdentityAuthenticationForBearer( OpenIddictValidationAspNetCoreDefaults.AuthenticationScheme ); context.Services.Configure<AbpClaimsPrincipalFactoryOptions>(options => { options.IsDynamicClaimsEnabled = true; }); }It appears that you do not have a separate authentication server application. My previous code example assumed the existence of both the
AuthServerproject and theHttpApiHostproject as separate components. However, it appears that only theHttpApiHostproject is present, likely in a unified configuration.In that case, you may use the following code in your application:
Configure<JwtBearerOptions>(options => { options.TokenValidationParameters = new Microsoft.IdentityModel.Tokens.TokenValidationParameters { ValidateIssuerSigningKey = true, AlgorithmValidator = (algorithm, securityKey, securityToken, validationParameters) => { return !algorithm.Equals("none", StringComparison.OrdinalIgnoreCase); } }; });This code should be placed prior to invoking the
ConfigureAuthenticationmethod. Doing so should ensure proper functionality. -
0
Thanks!