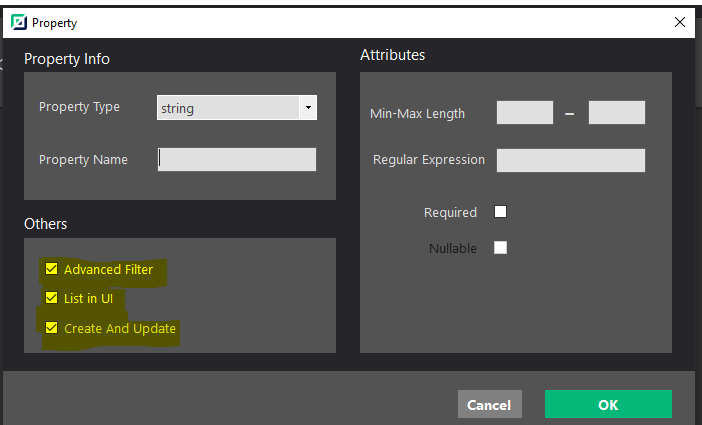
Add the features present in AspNetZero RadTool to Abp Suite as the section "Other" where we can set "Advanced Filter", "List in UI" and "Create and Update".
And, if possible, reduce the number of template files used by Abp Suite also giving the possibility to indicate the sub-path where to save the files as it could be done in AspNetZero RadTool.
Thanks,
Robertoyes this is on the roadmap , we'll implement it.
this feature is included in ABP v7.2 release.
The Advanced Filter is still missing on the Blazor Server UI template. Do you plan that as well?
Thank you for your help. This is working :)
Just to clarify, we are not using the DevExtreme FileUploader widget, but the DxUpload component for Blazor UI. We can try the js widget as well but we already tried adding the token to a form field instead of the header in the DxUpload component. The result was the same. So the token gets to the API but then the validation fails.
Thanks for the links, I checked them out. Unfortunately, they only talk about how to send the token, that we have already succeeded, but we get this error: 2023-05-30 16:40:19.206 +02:00 [WRN] The provided antiforgery token was meant for a different claims-based user than the current user.
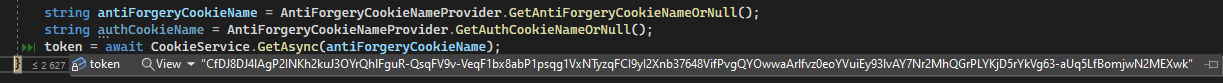
We get the token on the razor page as follows:
string antiForgeryCookieName = AntiForgeryCookieNameProvider.GetAntiForgeryCookieNameOrNull(); var token = await CookieService.GetAsync(antiForgeryCookieName);
Posting the edit form on the same razor page to the ABP application service Create method is working. If we catch this request with an IHttpContextAccessor, we can see the same token inside the request cookies.
What could be the cause of the above error?
Hi,
In our ABP Commercial (Blazor Server UI) project, we are testing the DevExpress DxUpload component for file upload. This calls an endpoint created in an API controller to handle the upload process. The problem is that by default we get the following error: 2023-05-30 16:28:59.734 +02:00 [WRN] The required antiforgery request token was not provided in either form field "__RequestVerificationToken" or header value "RequestVerificationToken".
So we retrieved the required token as follows:
string antiForgeryCookieName = AntiForgeryCookieNameProvider.GetAntiForgeryCookieNameOrNull(); var token = await CookieService.GetAsync(antiForgeryCookieName);
We added this token to the request header with the RequestVerificationToken key. However, we received the following error message: 2023-05-30 16:40:19.206 +02:00 [WRN] The provided antiforgery token was meant for a different claims-based user than the current user.
How can we send the proper token?
Thanks, Peter