Thank you for following up; this is what I was looking for. I didn't realize some of that data was already exposed to me that way, so I appreciate your patience.
I think I know everything I need to complete this feature.
I still need help with this. I decided to try to implement what was listed by the AI along with your comments. I created a page that allows the user to change their subscription. Here is the on post method:
public async Task<IActionResult> OnPostChangeEditionAsync(Guid editionId)
{
try
{
var result = await _multiTenancyAppService.ChangeEditionAsync(editionId);
if (result.RequiresPayment && result.PaymentRequestId != Guid.Empty)
{
return LocalRedirectPreserveMethod($"/Payment/GatewaySelection?paymentRequestId={result.PaymentRequestId}");
}
Alerts.Success(result.Message ?? "Plan changed successfully!");
return RedirectToPage();
}
catch (UserFriendlyException ex)
{
Alerts.Danger(ex.Message);
return RedirectToPage();
}
}
This line:
var result = await _multiTenancyAppService.ChangeEditionAsync(editionId);
in turn (eventually, after some checks) calls this:
paymentRequestDto = await _subscriptionAppService.CreateSubscriptionAsync(newEditionId, tenantId);
This collects payment and successfully changes the edition of the tenant, but the problem is that the payment isn't prorated, which is what I feared. I went into my sandbox Stripe account, and it showed a transaction for the full amount of the original edition, and then when I switched the edition, it showed the full amount for the new edition. I was hoping this would the amount for the new edition less the original edition (since in this case the new edition was more expensive).
I feel like this type of functionality has to exist in ABP somewhere, but so far, I am striking out.
Please reply soon; I need help with this and I'm disappointed I still haven't received a reply after two months.
That worked! Thanks for your help!
When I call that function, nothing happens, and I get these errors in the browser console:
If I click the appearance modes in the toolbar settings, it still functions correctly, and there are no errors. I'm not sure why it is looking for 'undefined' css files. Do you know what might be causing this?
Thank you for providing some instructions on the source code. I was able to download it and have overridden _Sidebar.cshtml successfully.
Regarding the appearance switching, it is this section here:
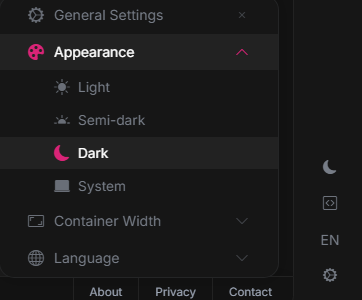 What I want to do is create a rocker/toggle like this:
What I want to do is create a rocker/toggle like this:
that toggles between light and dark mode. But to do that, it seems like I would need to call some function that changes the mode, but I cannot find it. Is there a way to programmatically access the appearance switcher?
I want to change the design a bit on LeptonX since the way it is setup now doesn't suit my use-case. What I am trying to do is to add a light/dark mode toggle and a logout button the footer area of the sidebar and then completely remove the toolbar. I have been able to remove the toolbar successfully, but the other tasks have proven more difficult.
Any help with this? I can start throwing things at the wall and see what sticks, but it would be really helpful to get some guidance on this, especially since I used a support ticket to ask this question. I'm still not sure if I will need to overwrite the SubscriptionCreatedHandler.cs file and it seems like I will need to get a copy from someone to be able to do that.
Please help. Thanks.
Charlie
Hi, hoping to have those questions above answered. I feel like I need a bit more context regarding how ABP handles changing editions, since it will require prorated payment with Stripe. To reiterate, can I simply create a new subscription for the tenant (and have it overwrite the existing subscription), or do I need to somehow trigger a subscription change (with payment proration) with Stripe before changing the edition entity for the tenant?
Any help on this would be greatly appreciated.
Charlie
Thanks for looking into this.
A few questions:

