Hello,
I have a Blazor WASM + Maui Blazor project + API project in which I have implemented the login through a Microsoft account. I also use OpenIDDict
The logout process is done by calling the following code:
MAUI Blazor:
NavigationManager.NavigateToLogout("/account/logout");
Blazor Web App:
NavigationManager.NavigateToLogout("/authentication/logout");
In both cases, it logs me out of my application, but it does not log me out of Microsoft Entra. This means that when the users tries to log in again through Microsoft Entra, they're automatically logged back in with the same account.
Should the logout process of Abp.IO also send a logout request to my Microsoft Entra account, or do I need to do some extra steps?
Thanks!
12 Answer(s)
-
0
- Solution
What happens by default:
- NavigationManager.NavigateToLogout(...) signs the user out from your ABP/OpenIddict server and clears the local app session (Blazor WASM/MAUI). It does not automatically sign out from Microsoft Entra ID. After logout, when users start login again, Entra can silently re-authenticate using its active session, so they get back in without picking an account.
Why: OIDC single logout is a separate step. To sign out of the external Identity Provider (Microsoft Entra), the client must call the Entra “end session” (sign-out) endpoint with appropriate parameters. ABP/OpenIddict doesn’t automatically perform an upstream IdP logout. Some IdPs also restrict third-party initiated sign-outs.
What to do:
If you want to also sign out from Microsoft Entra:
- Redirect the user to Entra’s sign-out URL after your app logout completes. Microsoft Entra supports front-channel sign-out via its OIDC end-session request.
- The typical URL pattern (see Microsoft docs) is: https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout?post_logout_redirect_uri={url-encoded-callback}
- Steps:
- Complete app logout first (NavigateToLogout).
- On the logout callback (Blazor WASM’s /authentication/logout-callback page), navigate to the Entra logout URL above, passing post_logout_redirect_uri back to your app’s public URL (e.g., https://yourapp/authentication/login or a public landing page).
- After Entra clears the session, user is redirected to your post_logout_redirect_uri. Make sure that URI is registered as a logout redirect in your Entra app registration.
- Note: If you use multiple tenants or the common endpoint, adjust {tenant} accordingly.
Example (Blazor WASM override of the Authentication page):
// MyAuthentication.razor @using Microsoft.AspNetCore.Components.WebAssembly.Authentication @using Volo.Abp.DependencyInjection @inherits Volo.Abp.AspNetCore.Components.WebAssembly.LeptonXTheme.Pages.Authentication @attribute [ExposeServices(typeof(Volo.Abp.AspNetCore.Components.WebAssembly.LeptonXTheme.Pages.Authentication))] @attribute [Dependency(ReplaceServices = true)] <RemoteAuthenticatorView Action="@Action" /> // MyAuthentication.razor.cs public partial class MyAuthentication { protected override void OnInitialized() { if (Action == "logout-callback") { // 1) After app logout completes, sign out from Entra too: var postLogout = Uri.EscapeDataString(NavigationManager.BaseUri.TrimEnd('/')); // e.g. https://yourapp/ var tenant = "your-tenant-id-or-common"; var entraLogout = $"https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout?post_logout_redirect_uri={postLogout}"; NavigationManager.NavigateTo(entraLogout, forceLoad: true); return; } } }Important: - Ensure post_logout_redirect_uri is configured in your Entra app registration. - Use a fully qualified HTTPS URL. - If you want to send users back to login immediately, set post_logout_redirect_uri to your app root (which is [Authorize] protected) or to /authentication/login.- If you cannot or do not want to sign out from Entra (e.g., organizational policy):
- Force account selection on next login by adding prompt=select_account to the authorization request so users can choose a different Entra account even if a session exists.
- In Blazor WASM AddOidcAuthentication, you can append query parameters to the authorization endpoint via ProviderOptions.AdditionalProviderParameters:
builder.Services.AddOidcAuthentication(options => { builder.Configuration.Bind("AuthServer", options.ProviderOptions); options.ProviderOptions.AdditionalProviderParameters.Add("prompt", "select_account"); });- This does not sign out Entra but prevents silent re-login.- For MAUI (if using an embedded OIDC client like IdentityModel.OidcClient):
- After your app logout, also navigate to the Entra logout URL using a browser (via WebAuthenticator or Launcher) with post_logout_redirect_uri back to your custom scheme (if applicable), or a neutral page.
- Ensure your redirect URI/scheme is registered in Entra and in your platform handlers.
- Known ABP notes:
- ABP/OpenIddict handles app-side logout (/account/logout or /authentication/logout and callback) but doesn’t automatically trigger upstream IdP logout. This behavior is consistent with OIDC norms and prior ABP support answers.
- Sources
- Microsoft Entra ID sign-out flow (OpenID Connect):
- https://learn.microsoft.com/en-us/entra/identity-platform/v2-protocols-oidc
- https://learn.microsoft.com/en-us/entra/identity-platform/v2-protocols-oidc#send-a-sign-out-request
- ABP Support references about external provider logout behavior and Blazor WASM logout customization (indirectly relevant, confirming ABP doesn’t remove the provider’s session automatically):
- https://abp.io/support/questions/2283
- https://abp.io/support/questions/3071
- https://abp.io/support/questions/5976
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
hi
Is your Auth Server/OpenID website also logged out?
Can you share the code for the
Microsoft Entra integrationauthentication?eg
context.Services.AddAuthentication().MicrosoftEntra()Can you also share the
harfile of the logout process?https://abp.io/support/questions/8622/How-to-enable-Debug-logs-for-troubleshoot-problems#answer-3a1a1c4b-691e-3403-98b9-5f23fa024759
Thanks.
-
0
Hi,
Yes, it is logged out of the application.
Here's the Microsoft Entra Configuration. Please note that I'm using two different Microsoft Entra accounts
var authBuilder = context.Services.AddAuthentication(); if (!string.IsNullOrEmpty(configuration["AzureEntraMembers:ClientId"]) && !string.IsNullOrEmpty(configuration["AzureEntraMembers:ClientSecret"]) && !string.IsNullOrEmpty(configuration["AzureEntraMembers:MicrosoftLoginUrl"])) { var tenantUrl = configuration["AzureEntraMembers:MicrosoftLoginUrl"]; tenantUrl = tenantUrl.TrimEnd('/'); authBuilder.AddMicrosoftAccount(PSACAuthenticationSchemes.MembersEntra, options => { options.ClientId = configuration["AzureEntraMembers:ClientId"]!; options.ClientSecret = configuration["AzureEntraMembers:ClientSecret"]!; options.AuthorizationEndpoint = $"{tenantUrl}/oauth2/v2.0/authorize"; options.TokenEndpoint = $"{tenantUrl}/oauth2/v2.0/token"; options.ClaimActions.MapCustomJson("picture", _ => "[https://graph.microsoft.com/v1.0/me/photo/$value");](https://graph.microsoft.com/v1.0/me/photo/$value");) options.SaveTokens = true; }); } if (!string.IsNullOrEmpty(configuration["AzureEntraWorkforce:ClientId"]) && !string.IsNullOrEmpty(configuration["AzureEntraWorkforce:ClientSecret"]) && !string.IsNullOrEmpty(configuration["AzureEntraWorkforce:MicrosoftLoginUrl"])) { var staffTenantUrl = configuration["AzureEntraWorkforce:MicrosoftLoginUrl"]; staffTenantUrl = staffTenantUrl.TrimEnd('/'); authBuilder.AddMicrosoftAccount(PSACAuthenticationSchemes.WorkforceEntra, options => { options.ClientId = configuration["AzureEntraWorkforce:ClientId"]!; options.ClientSecret = configuration["AzureEntraWorkforce:ClientSecret"]!; options.CallbackPath = "/signin-microsoft-workforce"; if (!string.IsNullOrEmpty(staffTenantUrl)) { options.AuthorizationEndpoint = $"{staffTenantUrl}/oauth2/v2.0/authorize"; options.TokenEndpoint = $"{staffTenantUrl}/oauth2/v2.0/token"; } options.SaveTokens = true; }); }I also have generated the har file while doing the logout, how do I share it with you? (It's 16 MB)
-
0
hi
I also have generated the har file while doing the logout, how do I share it with you? (It's 16 MB)
liming.ma@volosoft.com
If Microsoft has a signout endpoint, you can add a
<iframe class="d-none" src="@ms_signout_Uri"></iframe>toLogout.cshtmlto sign out of it.Thanks.
-
0
I'm not sure about the iframe solution, as we submit the MAUI Blazor App to the app stores, and the app stores will often reject apps that have iframes
-
0
hi
The
<iframe src="@ms_signout_Uri"></iframe>will add to the auth server website when you log out from your app.Thanks.
-
0
Upon further investigation, the signout url provided by Microsoft which is https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout requires an interaction with the user, so I don't think the iframe is the desired solution here
-
0
hi
requires an interaction with the user,
https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout?post_logout_redirect_uri={callback_uri}
Can you share a GIF of this logout endpoint?
If users need to click a button to complete the logout process, that's the only way we can do it. Not all external logins support sign-out.
Thanks.
-
0
Here's what the login endpoint looks like, it requires me to click on the account that I'm using to logout.
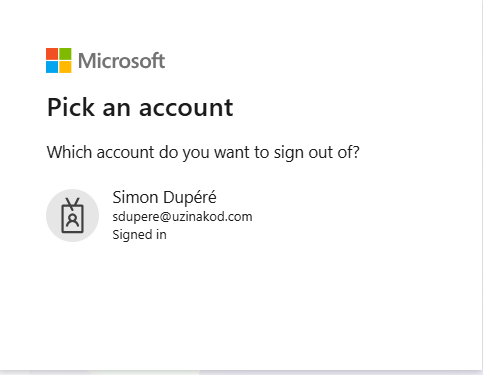 So I'm trying another approach. I saw that I can supply my url https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout?post_logout_redirect_uri={callback_uri} with a callback uri. So I'm thinking that maybe I can have a logout url that points to my app's logout.I have tried different url but I can't get it to work, For exemple if I set my callback url to https://localhost:44372/authentication/logout (where localhost:44372 is my blazor WASM front-end), then I get the following result.
So I'm trying another approach. I saw that I can supply my url https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout?post_logout_redirect_uri={callback_uri} with a callback uri. So I'm thinking that maybe I can have a logout url that points to my app's logout.I have tried different url but I can't get it to work, For exemple if I set my callback url to https://localhost:44372/authentication/logout (where localhost:44372 is my blazor WASM front-end), then I get the following result.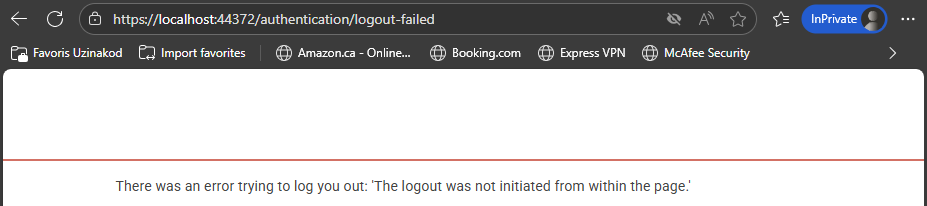 Is there any other endpoint that I could use as a callback url that will succesffuly log me out?
Is there any other endpoint that I could use as a callback url that will succesffuly log me out? -
0
hi
Can you try that? Doesn't need to
/authentication/logouthttps://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout?post_logout_redirect_uri= https://localhost:44372 Thanks.
-
0
I'm not sure I follow. Calling the Microsoft Logout https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout logs me out of Microsoft Entra, but I still need to call Abp's Logout Endpoint somehow, so I don't see how using post_logout_redirect_uri= https://localhost:44372 would accomplish that.
-
0
hi
Your application will first log out. After that, you can redirect to Microsoft's website to log out. And Microsoft redirects you back to your website.
- https://localhost:44372/Account/Logout
- Redirect to https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout?post_logout_redirect_uri=https://localhost:44372
- Microsoft Logout and redirect to
post_logout_redirect_urihttps://localhost:44372
Thanks.





























































