I'm not sure I follow. Calling the Microsoft Logout https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout logs me out of Microsoft Entra, but I still need to call Abp's Logout Endpoint somehow, so I don't see how using post_logout_redirect_uri= https://localhost:44372 would accomplish that.
Here's what the login endpoint looks like, it requires me to click on the account that I'm using to logout.
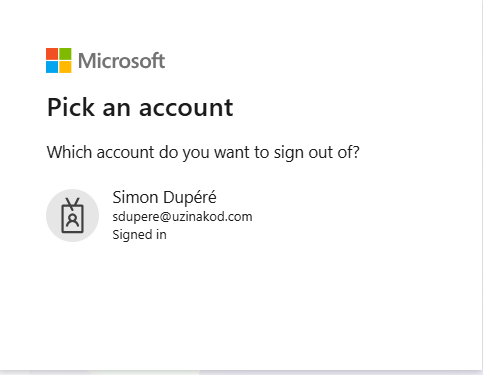 So I'm trying another approach. I saw that I can supply my url https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout?post_logout_redirect_uri={callback_uri} with a callback uri. So I'm thinking that maybe I can have a logout url that points to my app's logout.I have tried different url but I can't get it to work, For exemple if I set my callback url to https://localhost:44372/authentication/logout (where localhost:44372 is my blazor WASM front-end), then I get the following result.
So I'm trying another approach. I saw that I can supply my url https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout?post_logout_redirect_uri={callback_uri} with a callback uri. So I'm thinking that maybe I can have a logout url that points to my app's logout.I have tried different url but I can't get it to work, For exemple if I set my callback url to https://localhost:44372/authentication/logout (where localhost:44372 is my blazor WASM front-end), then I get the following result.
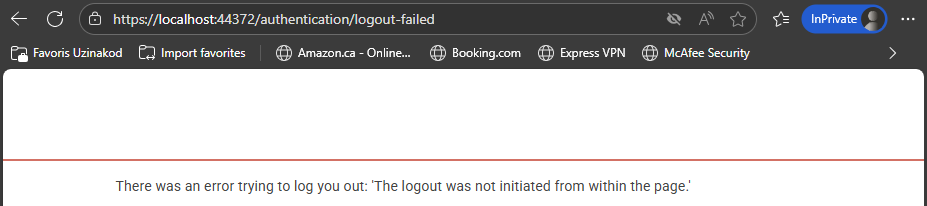 Is there any other endpoint that I could use as a callback url that will succesffuly log me out?
Is there any other endpoint that I could use as a callback url that will succesffuly log me out?
Upon further investigation, the signout url provided by Microsoft which is https://login.microsoftonline.com/{tenant}/oauth2/v2.0/logout requires an interaction with the user, so I don't think the iframe is the desired solution here
I'm not sure about the iframe solution, as we submit the MAUI Blazor App to the app stores, and the app stores will often reject apps that have iframes
Hi,
Yes, it is logged out of the application.
Here's the Microsoft Entra Configuration. Please note that I'm using two different Microsoft Entra accounts
var authBuilder = context.Services.AddAuthentication();
if (!string.IsNullOrEmpty(configuration["AzureEntraMembers:ClientId"]) &&
!string.IsNullOrEmpty(configuration["AzureEntraMembers:ClientSecret"]) &&
!string.IsNullOrEmpty(configuration["AzureEntraMembers:MicrosoftLoginUrl"]))
{
var tenantUrl = configuration["AzureEntraMembers:MicrosoftLoginUrl"];
tenantUrl = tenantUrl.TrimEnd('/');
authBuilder.AddMicrosoftAccount(PSACAuthenticationSchemes.MembersEntra, options =>
{
options.ClientId = configuration["AzureEntraMembers:ClientId"]!;
options.ClientSecret = configuration["AzureEntraMembers:ClientSecret"]!;
options.AuthorizationEndpoint = $"{tenantUrl}/oauth2/v2.0/authorize";
options.TokenEndpoint = $"{tenantUrl}/oauth2/v2.0/token";
options.ClaimActions.MapCustomJson("picture", _ => "[https://graph.microsoft.com/v1.0/me/photo/$value");](https://graph.microsoft.com/v1.0/me/photo/$value");)
options.SaveTokens = true;
});
}
if (!string.IsNullOrEmpty(configuration["AzureEntraWorkforce:ClientId"]) &&
!string.IsNullOrEmpty(configuration["AzureEntraWorkforce:ClientSecret"]) &&
!string.IsNullOrEmpty(configuration["AzureEntraWorkforce:MicrosoftLoginUrl"]))
{
var staffTenantUrl = configuration["AzureEntraWorkforce:MicrosoftLoginUrl"];
staffTenantUrl = staffTenantUrl.TrimEnd('/');
authBuilder.AddMicrosoftAccount(PSACAuthenticationSchemes.WorkforceEntra, options =>
{
options.ClientId = configuration["AzureEntraWorkforce:ClientId"]!;
options.ClientSecret = configuration["AzureEntraWorkforce:ClientSecret"]!;
options.CallbackPath = "/signin-microsoft-workforce";
if (!string.IsNullOrEmpty(staffTenantUrl))
{
options.AuthorizationEndpoint = $"{staffTenantUrl}/oauth2/v2.0/authorize";
options.TokenEndpoint = $"{staffTenantUrl}/oauth2/v2.0/token";
}
options.SaveTokens = true;
});
}
I also have generated the har file while doing the logout, how do I share it with you? (It's 16 MB)
Hello,
I have a Blazor WASM + Maui Blazor project + API project in which I have implemented the login through a Microsoft account. I also use OpenIDDict
The logout process is done by calling the following code:
MAUI Blazor:
NavigationManager.NavigateToLogout("/account/logout");
Blazor Web App:
NavigationManager.NavigateToLogout("/authentication/logout");
In both cases, it logs me out of my application, but it does not log me out of Microsoft Entra. This means that when the users tries to log in again through Microsoft Entra, they're automatically logged back in with the same account.
Should the logout process of Abp.IO also send a logout request to my Microsoft Entra account, or do I need to do some extra steps?
Thanks!
I was also able to get the following error through the Azure event log
EventId: 1 SpanId: c2c679515a9491fd TraceId: 6f1fd8a38b0d964b37ec6b4a8be97680 ParentId: 0000000000000000 RequestId: 400000d8-0000-9800-b63f-84710c7967bb RequestPath: /signin-microsoft-workforce An unhandled exception has occurred while executing the request. Exception: Microsoft.AspNetCore.Authentication.AuthenticationFailureException: An error was encountered while handling the remote login. ---> Microsoft.AspNetCore.Authentication.AuthenticationFailureException: The oauth state was missing or invalid. --- End of inner exception stack trace --- at Microsoft.AspNetCore.Authentication.RemoteAuthenticationHandler`1.HandleRequestAsync() at Microsoft.AspNetCore.Authentication.AuthenticationMiddleware.Invoke(HttpContext context) at Volo.Abp.AspNetCore.Security.AbpSecurityHeadersMiddleware.InvokeAsync(HttpContext context, RequestDelegate next) at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.InterfaceMiddlewareBinder.<>c__DisplayClass2_0.<<CreateMiddleware>b__0>d.MoveNext() --- End of stack trace from previous location --- at Microsoft.AspNetCore.Diagnostics.ExceptionHandlerMiddlewareImpl.<Invoke>g__Awaited|10_0(ExceptionHandlerMiddlewareImpl middleware, HttpContext context, Task task)
[maliming] said: hi
/signin-microsoft-workforce/signin-microsoft-workflowIs there a spelling mistake?
Thanks.
Yes, I apologize, /signin-microsoft-workforce is the callback url that's actually used
Check the docs before asking a question: https://abp.io/docs/latest Check the samples to see the basic tasks: https://abp.io/docs/latest/samples The exact solution to your question may have been answered before, and please first use the search on the homepage.
I am attempting to implement two Microsoft Entra accounts for single-sign in. I am using two calls to AddMicrosoftAccount
var authBuilder = context.Services.AddAuthentication();
var tenantUrl = configuration["AzureEntraMembers:MicrosoftLoginUrl"];
tenantUrl = tenantUrl.TrimEnd('/');
authBuilder.AddMicrosoftAccount(PSACAuthenticationSchemes.MembersEntra, options =>
{
options.ClientId = configuration["AzureEntraMembers:ClientId"]!;
options.ClientSecret = configuration["AzureEntraMembers:ClientSecret"]!;
options.CallbackPath = "/signin-microsoft";
options.AuthorizationEndpoint = $"{tenantUrl}/oauth2/v2.0/authorize";
options.TokenEndpoint = $"{tenantUrl}/oauth2/v2.0/token";
options.ClaimActions.MapCustomJson("picture", _ => "[https://graph.microsoft.com/v1.0/me/photo/$value");](https://graph.microsoft.com/v1.0/me/photo/$value");)
options.SaveTokens = true;
});
var staffTenantUrl = configuration["AzureEntraWorkforce:MicrosoftLoginUrl"];
staffTenantUrl = staffTenantUrl.TrimEnd('/');
authBuilder.AddMicrosoftAccount(PSACAuthenticationSchemes.WorkforceEntra, options =>
{
options.ClientId = configuration["AzureEntraWorkforce:ClientId"]!;
options.ClientSecret = configuration["AzureEntraWorkforce:ClientSecret"]!;
options.CallbackPath = "/signin-microsoft-workforce";
<br>
if (!string.IsNullOrEmpty(staffTenantUrl))
{
options.AuthorizationEndpoint = $"{staffTenantUrl}/oauth2/v2.0/authorize";
options.TokenEndpoint = $"{staffTenantUrl}/oauth2/v2.0/token";
}
options.SaveTokens = true;
});
What happens: it works when I test on localhost, but as soon as I deploy on Azure I get a 404 error when calling /signin-microsoft-workflow. The page displays the error: The resource you are looking for has been removed, had its name changed, or is temporarily unavailable. The weird thing is that my other SSO (callback url: /signin-microsoft) works.
I have verified that my App Registration callbacks are properly configured.
Can you provide me possible causes why I get an error only on /signin-microsoft-workforce callback?

