- ABP Framework version: v5.0.1
- UI type: Angular
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): yes
Hello,
We are using ABP framework with separate identity server. When we run these projects over IIS on local machine the integration between Host and Identity Server work fine. However, when we have dockerized our Host Project, we have faced an authentication problem.(We have tried to run identity server both from docker and over IIS locally. The given error is the same)
Scenario:
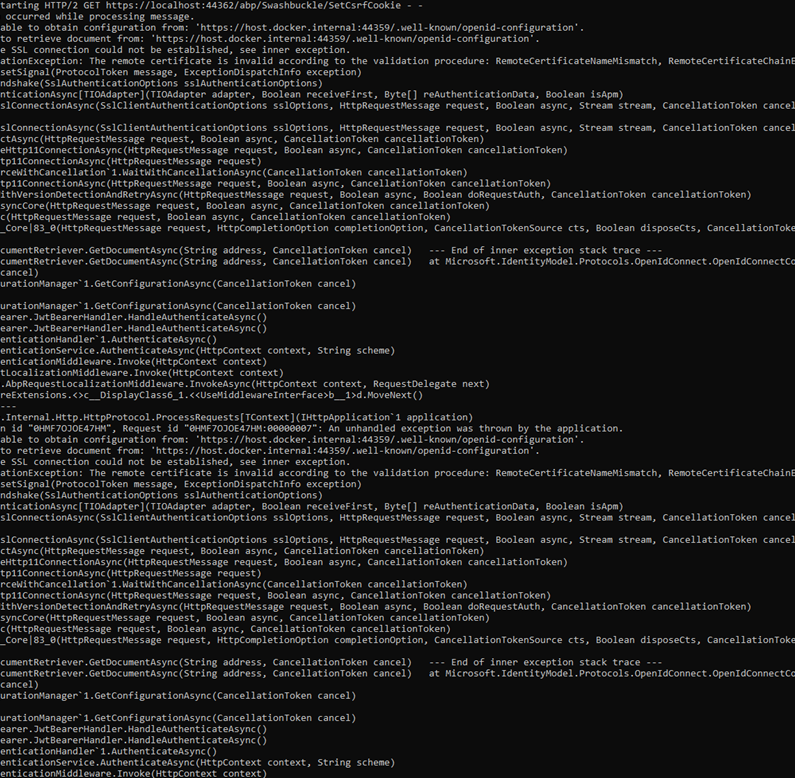
-We can reach the swagger endpoint over https successfully -Swagger authenticates by using identity server(Which is served over https too) and redirects back successfully. -When we send a request over swagger, host project throw the following error.(To get this error we needed to set the ShowPII flag):
Also:
-We are sure that “host.docker.internal “ is reachable from container because we reach the DB and the broker by the same way. -Identity server's url is the same with host server's authority. -Host server's url is defined in CORS urls of identity server. -Key persistency is set to file system.
`var keysFolder = Path.Combine(_environment.ContentRootPath, "Keys");
services.AddDataProtection().PersistKeysToFileSystem(new DirectoryInfo(keysFolder));`
-Cookie policy is set in both project's application builder.
`app.UseCookiePolicy(new CookiePolicyOptions
{
MinimumSameSitePolicy = SameSiteMode.None,
Secure = CookieSecurePolicy.Always
});`
Tried Alternatives:
-Creating certificates in different ways didn’t help. We have tried to generate .pfx certificate both by using ssl and “dotnet dev-certs”, the result is the same.
-Pfx certificate is tried to be created during the image building by the dockerfile instead of defining volume to the self-signed certificate of host machine. Both gave the same result.
-Inside the container, certificate is cleaned up and re-trusted by dotnet dev-certs https -ep /https/cert.pfx --trust -p password
-We have also tried to run these two projects with the same key and with different keys, the result didn't change.
-Configuring Kestrel options of host project's web builder for certificate instead of defining it while running the container doesn't change the error .
Thank you
1 Answer(s)
-
0
-We are sure that “host.docker.internal “ is reachable from container because we reach the DB and the broker by the same way.
You want tokens to be validated by the connections in between docker network since it doesn't make sense otherwise. However,
https://host.docker.internal/.well-known/openid-configurationendpoint must be reachable from outside (www).So it needs to be a valid domain that can be reached from anywhere since it is an openid provider (just like https://accounts.google.com/.well-known/openid-configuration).
Also please check identityserver deployment guide, it may help.