Hi,
i have to add Microsoft Web Identity as External Login Provider but i'm not able to understand where to customize the code. Do you have an example?
10 Answer(s)
-
0
To add Microsoft as an external login provider in your ABP Blazor Web App (v9.2.1), you need to configure the authentication in your AuthServer project and optionally customize the UI if needed. Here’s a step-by-step guide:
Install Required NuGet Package
- Ensure your AuthServer project references
Microsoft.AspNetCore.Authentication.MicrosoftAccount.
- Ensure your AuthServer project references
Configure Microsoft Authentication in AuthServer
- In your
AuthServerproject, update the authentication configuration (usually inStartup.csorProgram.cs):
context.Services.AddAuthentication() .AddMicrosoftAccount(options => { options.ClientId = configuration["Authentication:Microsoft:ClientId"]; options.ClientSecret = configuration["Authentication:Microsoft:ClientSecret"]; options.SaveTokens = true; options.Scope.Add("email"); });- Add the following to your
appsettings.json:
"Authentication": { "Microsoft": { "ClientId": "YOUR_MICROSOFT_CLIENT_ID", "ClientSecret": "YOUR_MICROSOFT_CLIENT_SECRET" } }- In your
Configure Redirect URI in Azure Portal
- In the Azure portal, set the Redirect URI to:
https://<your-auth-server-domain>/signin-microsoft
- In the Azure portal, set the Redirect URI to:
Enable Microsoft Login in the UI
- The ABP Account module will automatically show the Microsoft login button if the provider is configured.
- If you want to customize the login page, you can override the Account module’s login page in your Blazor project.
Multi-Tenancy (if needed)
- For multi-tenant scenarios, you can use ABP’s dynamic external provider configuration. See the official documentation for details.
Test the Integration
- Run your application, navigate to the login page, and you should see the Microsoft login option.
Example Reference:
- The official documentation provides a detailed guide and sample code for social/external logins, including Microsoft:
- https://abp.io/docs/commercial/latest/modules/account#social-external-logins
- https://abp.io/community/articles/4603b9cf
Customization:
- If you need to customize the login UI, you can override the login page as described here:
- https://abp.io/en/abp/latest/Modules/Account
Sources:
- https://abp.io/docs/commercial/latest/modules/account#social-external-logins
- https://abp.io/community/articles/4603b9cf
- https://abp.io/en/abp/latest/Modules/Account
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
I have to use Microsoft.Web.Identity as method of atuhentication
-
0
Hi,
Thank you for your question! I’m assuming you’re referring to integrating Microsoft’s authentication (likely via Microsoft Entra ID) as an external login provider using the Microsoft.Identity.Web library in your ABP Framework application. If you meant something else by "Microsoft Web Identity," could you please clarify? For now, I’ll provide some useful resource for Microsoft' s authentication:
- https://abp.io/community/articles/how-to-use-the-azure-active-directory-authentication-for-mvc-razor-page-applications-4603b9cf#gsc.tab=0
- https://abp.io/community/articles/how-to-setup-azure-active-directory-and-integrate-abp-angular-application-lyk87w5l
- https://abp.io/support/questions/7501/Problems-with-integration-of-Entra-External-ID
- https://abp.io/support/questions/8941/Switch-Azure-ADEntra-user-rather-than-pick-an-account-to-sign-out-of#answer-3a1897bc-1e1b-cc7a-726d-59cdb2761e65
The first resource I recommend is described using the Microsoft.Identity.Web NuGet package.
-
0
Hi Berkansasmaz,
i have already test the four resource with no success.
If i use AddOpenIdConnect it work but i have to use AddMicrosoftIdentityWebApp
This is my code:
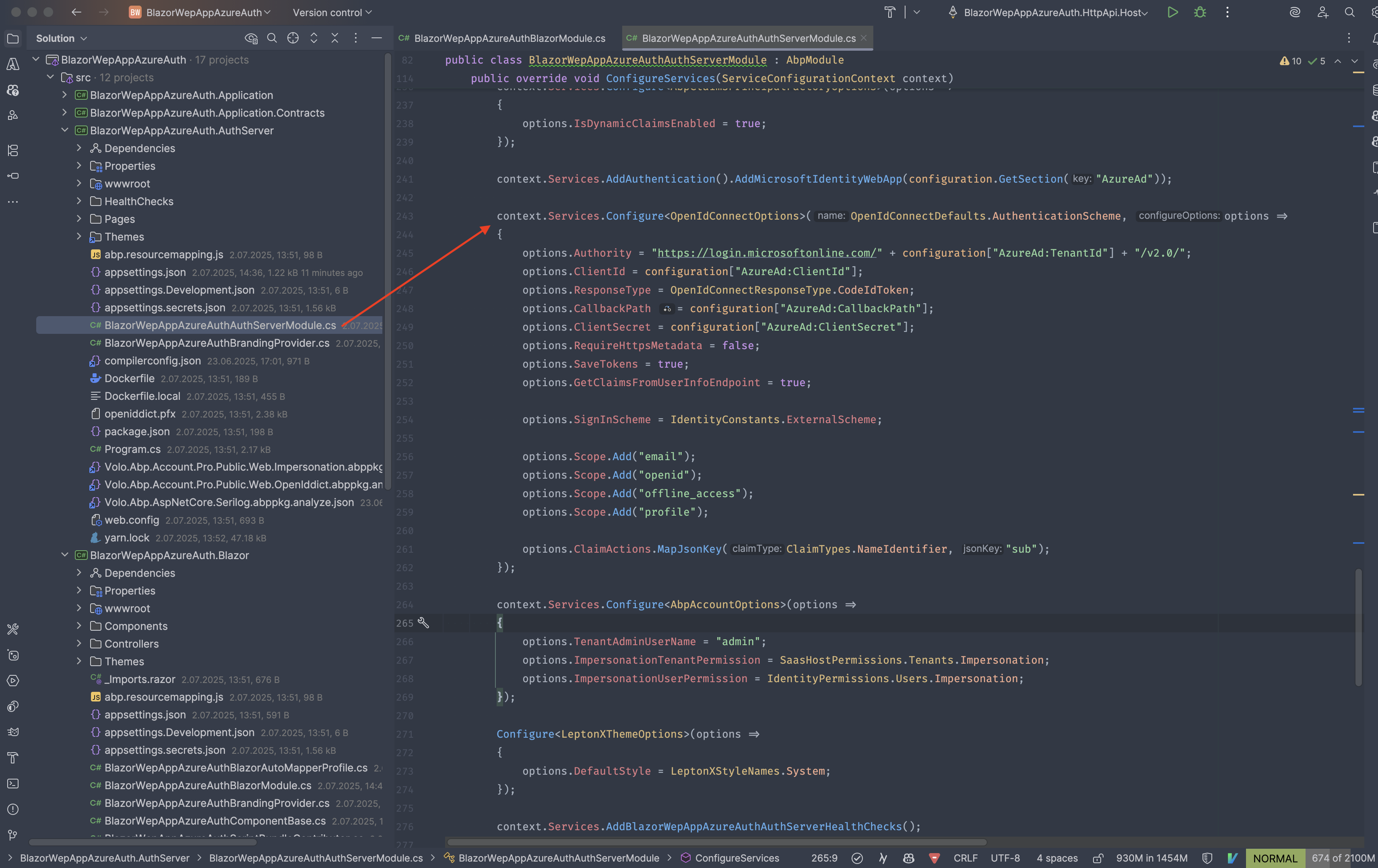
context.Services.AddAuthentication().AddMicrosoftIdentityWebApp(options => { options.Instance = "https://login.microsoftonline.com/"; options.TenantId = configuration["AzureAd:TenantId"]; options.ClientId = configuration["AzureAd:ClientId"]; options.ClientSecret = configuration["AzureAd:ClientSecret"]; //options.CallbackPath = configuration["AzureAd:CallbackPath"]; //options.ResponseType = OpenIdConnectResponseType.CodeIdToken; options.ResponseType = "code"; options.RequireHttpsMetadata = true; options.SaveTokens = true; options.GetClaimsFromUserInfoEndpoint = true; options.Scope.Add("email"); options.Scope.Add("openid"); options.Scope.Add("offline_access"); options.Scope.Add("profile"); //options.Scope.Add("https://analysis.windows.net/powerbi/api/Dataset.ReadWrite.All"); //options.Scope.Add("https://analysis.windows.net/powerbi/api/Workspace.Read.All"); options.SignInScheme = IdentityConstants.ExternalScheme; options.ClaimActions.MapJsonKey(ClaimTypes.NameIdentifier, "sub"); options.Events = new OpenIdConnectEvents { OnTokenValidated = context => { // Log token claims var claims = context.Principal.Claims; foreach (var claim in claims) { Console.WriteLine($"{claim.Type}: {claim.Value}"); } return Task.CompletedTask; }, OnAuthenticationFailed = context => { Console.WriteLine($"Authentication failed: {context.Exception.Message}"); return Task.CompletedTask; } }; });When i login i get the following error:
2025-06-26 21:32:53.327 +02:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. 2025-06-26 21:32:53.327 +02:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri. 2025-06-26 21:32:53.327 +02:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType. 2025-06-26 21:32:53.327 +02:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType. 2025-06-26 21:32:53.327 +02:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement. 2025-06-26 21:32:53.327 +02:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader. 2025-06-26 21:32:53.328 +02:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ValidateHostHeader. 2025-06-26 21:32:53.328 +02:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateValidatedTokens. 2025-06-26 21:32:53.328 +02:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromAuthorizationHeader. 2025-06-26 21:32:53.328 +02:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromBodyForm. 2025-06-26 21:32:53.328 +02:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromQueryString. 2025-06-26 21:32:53.328 +02:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens. 2025-06-26 21:32:53.328 +02:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was marked as rejected by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens. 2025-06-26 21:32:53.328 +02:00 [DBG] AuthenticationScheme: OpenIddict.Validation.AspNetCore was not authenticated.
-
0
Hello, sorry for the late reply. I will try your code during the day.
-
0
Hi berkansasmaz, i solved the issue,
I have only one problem. I need to save and store the AD access_token but is always blank. How i have to do and where? In the AuthServer or in the Host?
I need to use use it in the Blazora Page.
-
0
Hi Fabio.Zinesi,
Do you need it on client(Wasm) side or server side? Also, can you share the working version of
AddMicrosoftIdentityWebApp's configuration? -
0
this is the code in AuthServerModule.cs in ConfigureServices(context)
....
context.Services.AddAuthentication().AddMicrosoftIdentityWebApp(configuration.GetSection("AzureAd")); context.Services.Configure<OpenIdConnectOptions>(OpenIdConnectDefaults.AuthenticationScheme, options => { options.Authority = "https://login.microsoftonline.com/" + configuration["AzureAd:TenantId"] + "/v2.0/"; options.ClientId = configuration["AzureAd:ClientId"]; options.ResponseType = OpenIdConnectResponseType.CodeIdToken; options.CallbackPath = configuration["AzureAd:CallbackPath"]; options.ClientSecret = configuration["AzureAd:ClientSecret"]; options.RequireHttpsMetadata = false; options.SaveTokens = true; options.GetClaimsFromUserInfoEndpoint = true; options.SignInScheme = IdentityConstants.ExternalScheme; options.Scope.Add("email"); options.Scope.Add("openid"); options.Scope.Add("offline_access"); options.Scope.Add("profile"); options.ClaimActions.MapJsonKey(ClaimTypes.NameIdentifier, "sub"); });....
My application is Blazor Web App.
I need to use the token also in the API controllers and in the front end.
Probably i need to store the received token but i can't understand how to do it.
-
0
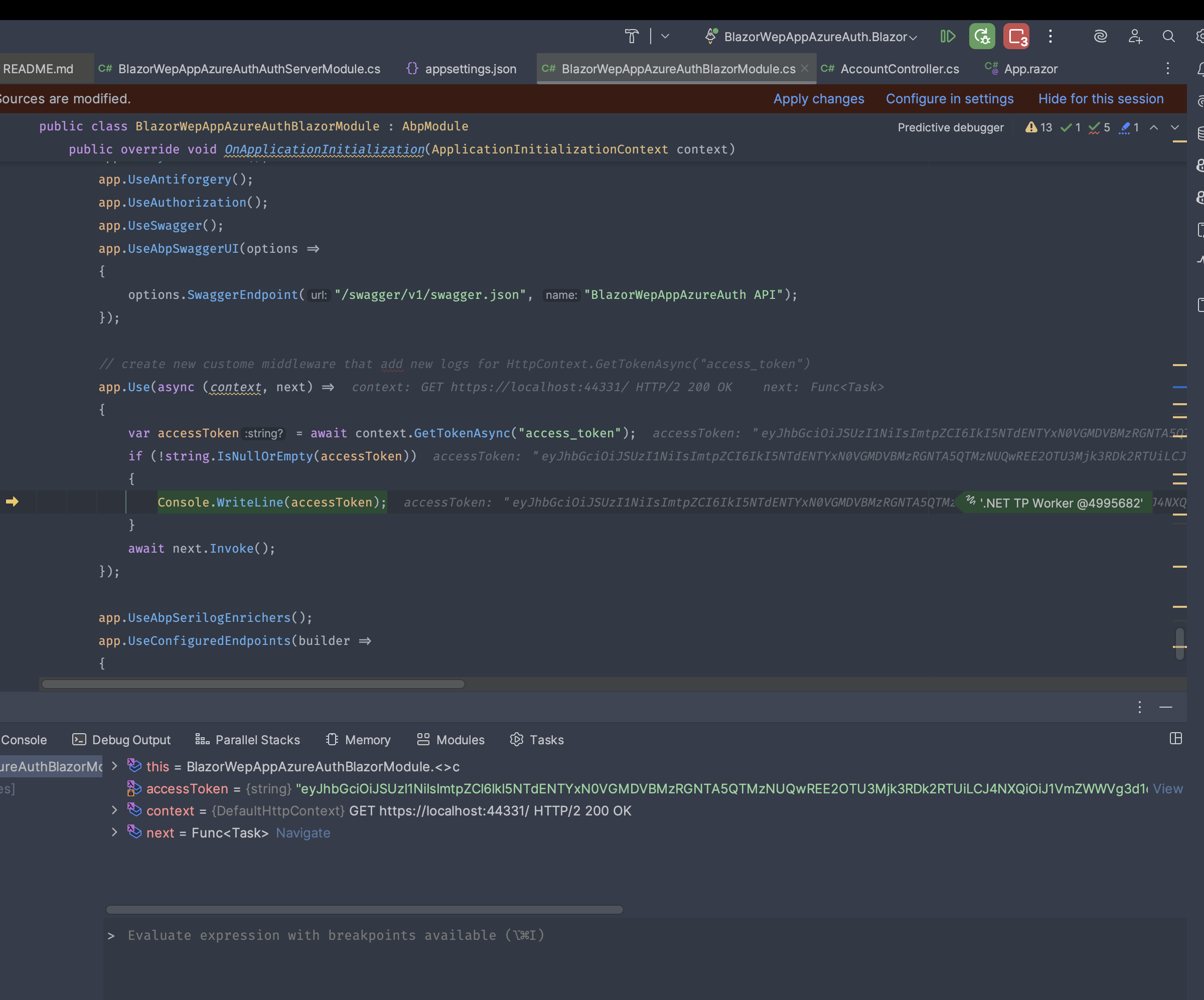
Hello, I used the information you provided to reproduce the problem. As a result, I added a middleware to the Blazor application as shown below. As you can see, I am able to access the access token, and the current user information is populated correctly. Could you clarify exactly where you are experiencing the issue?
OpenIdConnectOptions:
-
0
i'll check it