Please provide "detailed documentation" on using an OpenId connect identity provider like Okta or Auth0 for login into an ABP app for login. I can't find any documentation on this on ABP site.
12 Answer(s)
-
0
To integrate an OpenID Connect identity provider such as Okta or Auth0 for login in an ABP application, you can use the standard OpenIdConnect authentication middleware. ABP supports external authentication providers via OpenIdConnect, and the process is similar for any provider that implements the OpenID Connect protocol.
Here is a step-by-step guide:
Register Your Application with the Identity Provider
- Go to your provider's dashboard (e.g., Okta, Auth0).
- Register a new application.
- Set the redirect URI to match your ABP application's callback endpoint (e.g.,
https://localhost:44300/signin-oidc).
Configure appsettings.json Add a section for your OpenID Connect provider:
"OpenIdConnect": { "Authority": "https://YOUR_PROVIDER_DOMAIN/", "ClientId": "YOUR_CLIENT_ID", "ClientSecret": "YOUR_CLIENT_SECRET", "CallbackPath": "/signin-oidc" }Configure OpenIdConnect in ABP Module In your
HttpApi.Host(or.Webfor MVC) project, update the authentication configuration:public override void ConfigureServices(ServiceConfigurationContext context) { var configuration = context.Services.GetConfiguration(); context.Services.AddAuthentication() .AddOpenIdConnect("Oidc", "OpenID Connect", options => { options.Authority = configuration["OpenIdConnect:Authority"]; options.ClientId = configuration["OpenIdConnect:ClientId"]; options.ClientSecret = configuration["OpenIdConnect:ClientSecret"]; options.ResponseType = OpenIdConnectResponseType.CodeIdToken; options.CallbackPath = configuration["OpenIdConnect:CallbackPath"]; options.RequireHttpsMetadata = true; options.SaveTokens = true; options.GetClaimsFromUserInfoEndpoint = true; options.Scope.Add("email"); options.ClaimActions.MapJsonKey(System.Security.Claims.ClaimTypes.NameIdentifier, "sub"); }); }Update Redirect URI in Provider Dashboard
- Ensure the redirect URI in your provider's dashboard matches the
CallbackPathand your application's base URL.
- Ensure the redirect URI in your provider's dashboard matches the
Test the Integration
- Run your ABP application.
- Click the login button; you should be redirected to your OpenID Connect provider for authentication.
User Registration and Claims
- ABP will use the external login information to register or authenticate users.
- Make sure the provider returns the required claims (e.g.,
email,sub).
This approach works for any OpenID Connect-compliant provider, including Okta and Auth0. You only need to adjust the
Authority,ClientId, andClientSecretaccording to your provider's settings.Sources:
- How to Setup Azure Active Directory and Integrate ABP Angular Application (applies to any OpenID Connect provider)
- How to Use the Azure Active Directory Authentication for MVC / Razor Page Applications (applies to any OpenID Connect provider)
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
Thanks. This works for OIDC login. But, how do I set up the ABP app so that OpenId connect provider (Okta or Auth0) is the primary or main login?
-
0
Hello Jesse 👋,
I hope your trial license is going well ☺️
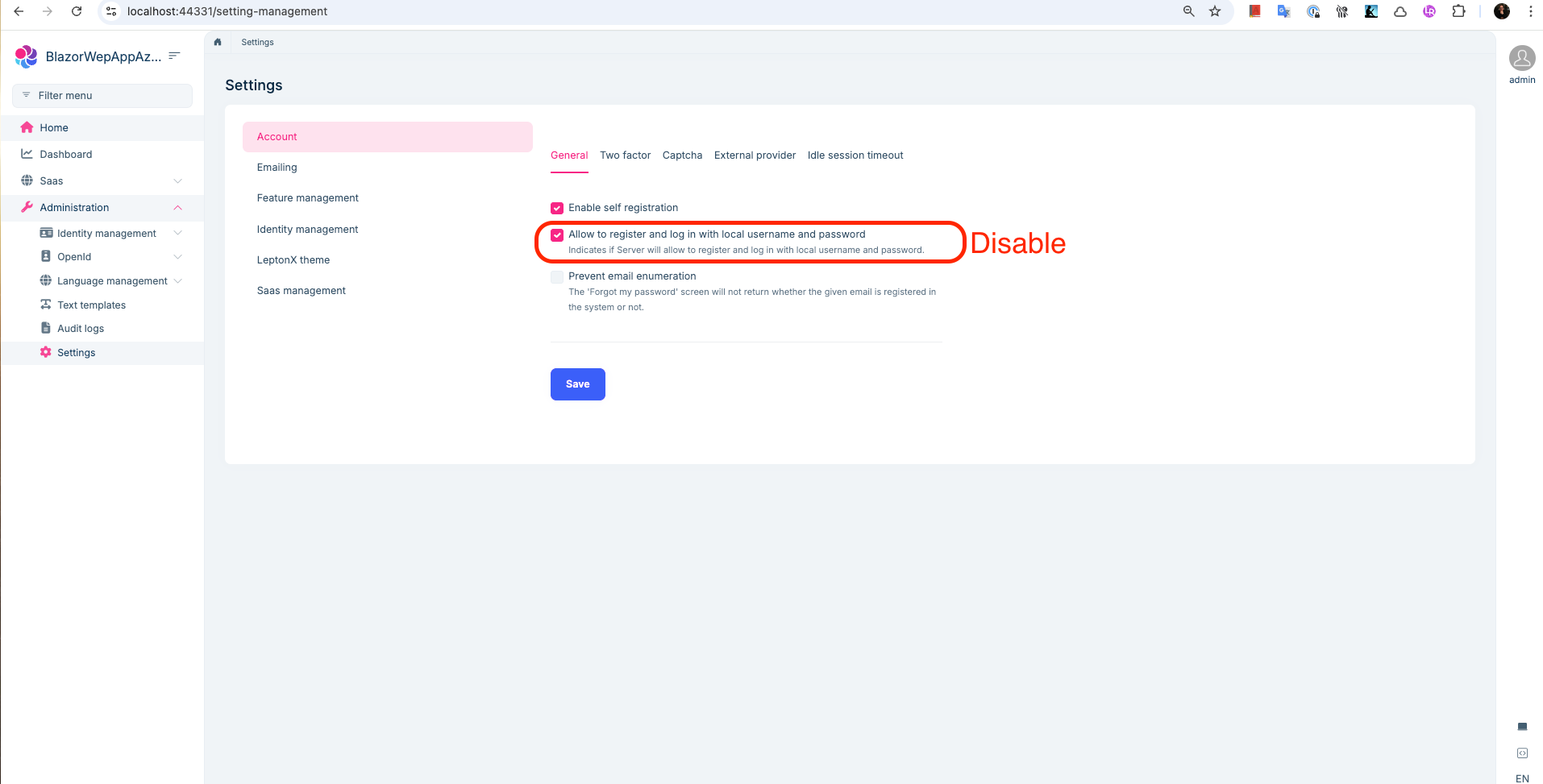
To resolve this, please disable the setting highlighted in the screenshot below. Once disabled, the OpenID Connect provider you have configured will be used automatically.
Best regards,
Berkan Şaşmaz
Developer Advocate https://www.berkansasmaz.com -
0
Hi, Thanks but I'm not able to get to that page because I setup OIDC ID provider as main login and since I can't get ABP to recognize the user after successful login with OIDC ID provider then I can't get to that page to disable option.
Just to clarify. I want to use an external OIDC ID provider as the main login to my app. I do not want to use or maintain Auth server. Is this possible with ABP?
Thanks, Jesse
-
0
Hi Jesse 👋,
Yes, it's possible to use an external OIDC identity provider as the main login without using the ABP AuthServer.
To do this:
- Do not create a tiered solution when generating your app.
- Configure the external OIDC provider (like Azure Entra ID or Auth0) directly in your main app (e.g., MVC or Blazor UI), as explained in the AI-generated answer.
- After successful login, make sure to disable the
"Allow to register and log in with local username and password"setting, as mentioned in the answer, so ABP doesn’t redirect to the AuthServer anymore.
In the GIF below, I demonstrated this with Azure Entra ID, but you can apply the same approach with Auth0 — there's no limitation.
⚠️ Important: Once you disable local login, you won’t be able to sign in with the default admin user anymore. So before logging out, assign the admin role to the user who logs in through Auth0. Otherwise, you’ll lose access to full permissions unless you manually update the database.
Let me know if you need help with the configuration.
-
0
[berkansasmaz] said: Hi Jesse 👋,
Yes, it's possible to use an external OIDC identity provider as the main login without using the ABP AuthServer.
To do this:
- Do not create a tiered solution when generating your app.
Hi berkansasmaz, I'm following this thread because I have a similar setup to do and I have the same configuration issues.
I will open a ticket about it soon, but I'll take this opportunity to better understand your suggestion. From your Gif it seems that in addition to the Account module you also installed the OpenIddict UI module. Creating a non-tiered solution means using OpenIddict included in ABP, right?
If I were to have multiple instances of my backend application this scenario would not work.
Also jesse.torres said: "Just to clarify. I want to use an external OIDC ID provider as the main login to my app. I do not want to use or maintain Auth server. Is this possible with ABP?"
Sorry to butt in, but I think this is an interesting topic for everyone.
Thank you for your understanding and availability
-
0
Hi 👋,
From your Gif it seems that in addition to the Account module you also installed the OpenIddict UI module. Creating a non-tiered solution means using OpenIddict included in ABP, right?
Yes, that's correct. When you create a non-tiered solution, OpenIddict is included via ABP modules. However, since it’s encapsulated within a module, you don’t need to manage or deploy it separately. The inclusion of the OpenIddict UI module should not be seen as a drawback—it simply gives you flexibility if you ever decide to customize authentication flows in the future.
As for Jesse’s point:
"Just to clarify. I want to use an external OIDC ID provider as the main login to my app. I do not want to use or maintain Auth server. Is this possible with ABP?"
Yes, this is absolutely possible. I believe what Jesse meant is that he does not want to maintain a separate AuthServer project. In a non-tiered solution, everything is hosted in a single application, and ABP takes care of the underlying OpenIddict setup through module references. So you're not responsible for deploying or maintaining a separate authorization server—it’s just a package dependency managed by the ABP team.
If I were to have multiple instances of my backend application this scenario would not work.
ABP is designed to support scalable, multi-instance deployments. There’s no technical limitation preventing you from running multiple instances of your backend in this scenario. If you face any specific issues with this, I recommend opening a separate issue so we can help investigate further.
Thanks for bringing up this topic—definitely valuable for many of us working with ABP.
-
0
Hi berkansasmaz and thanks for the response. But we were planning to use modular monolith solution. I guess this means we have to maintain an auth server?
-
0
Hi,
No, it doesn’t mean that you have to maintain a separate Auth Server. In a modular monolith setup, your final application, which hosts all the modules, does not need to be tiered.
If you haven’t already completed it, I recommend going through this tutorial to better understand how to build a modular monolith application and the benefits of this architecture.
To sum up, using a modular monolith architecture does not require you to host a separate Auth Server or maintain an Auth Server. If you'd like, I can show you a quick demo during our meeting on Thursday to clarify this further.
-
0
Thanks berkansasmaz,
I look forward to our meeting.
-Jesse
-
0
See you soon 👋
-
0
As a result of our meeting, I am sharing the code blocks you requested below:
OpenIdConnect Configuration:
context.Services.AddAuthentication().AddOpenIdConnect(); context.Services.Configure<OpenIdConnectOptions>(OpenIdConnectDefaults.AuthenticationScheme, options => { options.Authority = configuration["AzureAd:Instance"]; options.ClientId = configuration["AzureAd:ClientId"]; options.ResponseType = OpenIdConnectResponseType.CodeIdToken; options.CallbackPath = configuration["AzureAd:CallbackPath"]; options.ClientSecret = configuration["AzureAd:ClientSecret"]; options.RequireHttpsMetadata = false; options.SaveTokens = true; options.GetClaimsFromUserInfoEndpoint = true; options.SignInScheme = IdentityConstants.ExternalScheme; options.Events = new OpenIdConnectEvents { OnRedirectToIdentityProvider = redirectContext => { redirectContext.ProtocolMessage.Prompt = "login"; return Task.CompletedTask; } }; options.Scope.Add("email"); options.Scope.Add("openid"); options.Scope.Add("offline_access"); options.Scope.Add("profile"); options.ClaimActions.MapJsonKey(ClaimTypes.NameIdentifier, "sub"); });Custom register model to create user automatically:
[ExposeServices(typeof(RegisterModel))] public class MyRegisterModel : RegisterModel { public MyRegisterModel(IAuthenticationSchemeProvider schemeProvider, IOptions<AbpAccountOptions> accountOptions, IAccountExternalProviderAppService accountExternalProviderAppService, ICurrentPrincipalAccessor currentPrincipalAccessor, IHttpClientFactory httpClientFactory) : base(schemeProvider, accountOptions, accountExternalProviderAppService, currentPrincipalAccessor, httpClientFactory) { } public override async Task<IActionResult> OnGetAsync() { ExternalProviders = await GetExternalProviders(); if (!await CheckSelfRegistrationAsync()) { if (IsExternalLoginOnly) { return await OnPostExternalLogin(ExternalLoginScheme); } Alerts.Warning(L["SelfRegistrationDisabledMessage"]); return Page(); } if (IsExternalLogin) { var externalLoginInfo = await SignInManager.GetExternalLoginInfoAsync(); if (externalLoginInfo == null) { Logger.LogWarning("External login info is not available"); return RedirectToPage("./Login"); } var identity = externalLoginInfo.Principal.Identities.First(); var emailClaim = identity.FindFirst(AbpClaimTypes.Email) ?? identity.FindFirst(ClaimTypes.Email); if (emailClaim == null) { throw new AbpException("Could not find an email address for the user from the external login info!"); } var userName = await UserManager.GetUserNameFromEmailAsync(emailClaim.Value); var user = await RegisterExternalUserAsync(externalLoginInfo,userName, emailClaim.Value); await SignInManager.SignInAsync(user, isPersistent: true, authenticationMethod: ExternalLoginScheme); // Clear the dynamic claims cache. await IdentityDynamicClaimsPrincipalContributorCache.ClearAsync(user.Id, user.TenantId); return Redirect(ReturnUrl ?? "/"); } Alerts.Warning(L["SelfRegistrationDisabledMessage"]); return Page(); } }Disable local login in appsettings.json:
"Settings": { "Abp.Account.EnableLocalLogin":false }Note: After adding this setting, if it does not appear as false when you start the application, it is because the value stored in the database overrides the one in the appsettings. If you create a new database from scratch, the value in the appsettings will be used since there will be no conflicting setting in the database.
If you have no further questions on the subject, can I close the ticket?