8 Answer(s)
-
0
To address the issue of large cookie sizes when implementing refresh tokens in Blazor Server with ABP, consider the following best practices:
Avoid Storing Tokens in Cookies:
- By default, Blazor Server uses cookie authentication, and storing large tokens (like refresh tokens or JWTs) directly in cookies can easily exceed browser or gateway limits.
- Instead, rely on server-side session management. Store only a session identifier in the cookie, and keep tokens on the server side (e.g., in a distributed cache or database).
Use Reference Tokens:
- Configure your IdentityServer/OpenIddict to issue reference tokens instead of self-contained JWTs. Reference tokens are short identifiers, and the actual token data is stored server-side, reducing cookie size.
Adjust Cookie Authentication Options:
- Set the cookie expiration to match your desired session lifetime and avoid persisting refresh tokens in the cookie.
- Example:
context.Services.ConfigureApplicationCookie(options => { options.ExpireTimeSpan = TimeSpan.FromMinutes(60); // Set as needed options.SlidingExpiration = true; });
Use the "offline_access" Scope Only When Needed:
- Only request the "offline_access" scope (which enables refresh tokens) if your application truly requires it. For Blazor Server, you may not need refresh tokens if you can manage user sessions with cookies.
Consider Server-Side Token Storage:
- If you must use refresh tokens, store them securely on the server (e.g., using distributed cache keyed by user/session) and only keep a session identifier in the cookie.
Review Official Guidance:
- The ABP documentation for OpenIddict and refresh tokens provides further details and recommendations:
By following these practices, you can avoid large cookies and ensure compatibility with application gateways and browsers.
Sources:
- ABP OpenIddict Module: Refresh Token
- ABP OpenIddict Pro: Refresh Token
- Refresh token mechanism in Blazor Server (ABP Support)
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
How is this handled in abp generated projects? Is it better to issue reference token or store the token in cache? We also have the issue of menu items getting cleared when token expires when the application is idle for some time and user returns.
-
0
hi
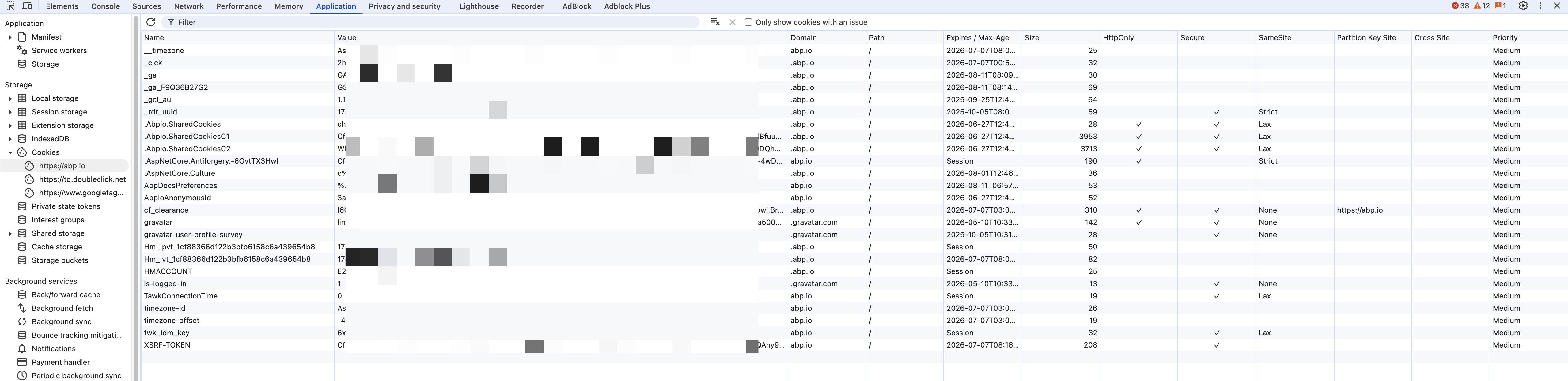
But this is resulting in cookie size to be huge and is blocked by the app gateway.
Can you share the error message?
How can I reproduce the error?
Thanks.
-
0
-
0
hi
Can you share the logs from the current website and the gateway?
Thanks.
-
0
Hi, We don't have access to Azure Application gateway logs, it's in client environment, we are not getting any logs in blazor server application, it's not even reaching blazor server application.
-
0
-
0
You can consider storing tokens in Redis.
The cache key can be
userid+BrowserInfoSimilar with https://abp.io/community/articles/switching-between-organization-units-i5tokpzt#gsc.tab=0
Thanks.