LDAP External login Provider
Introduction
The Identity PRO module has built-in LdapExternalLoginProvider and OpenLdapManager services. It implements LDAP authentication and gets user info for external login.
The cross platform LdapForNet library is used for Windows LDAP authentication. See LdapForNet GitHub repository for more information.
How to enable LDAP external login?
Youu need to enable the LDAP login feature and configure related settings.
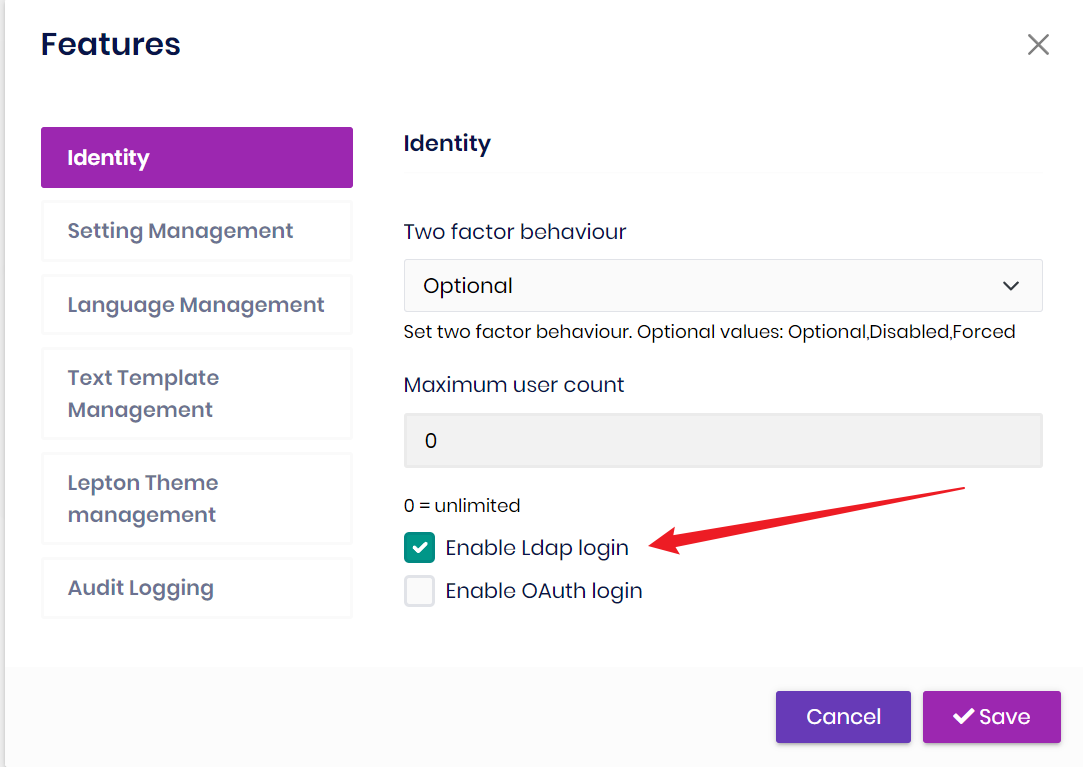
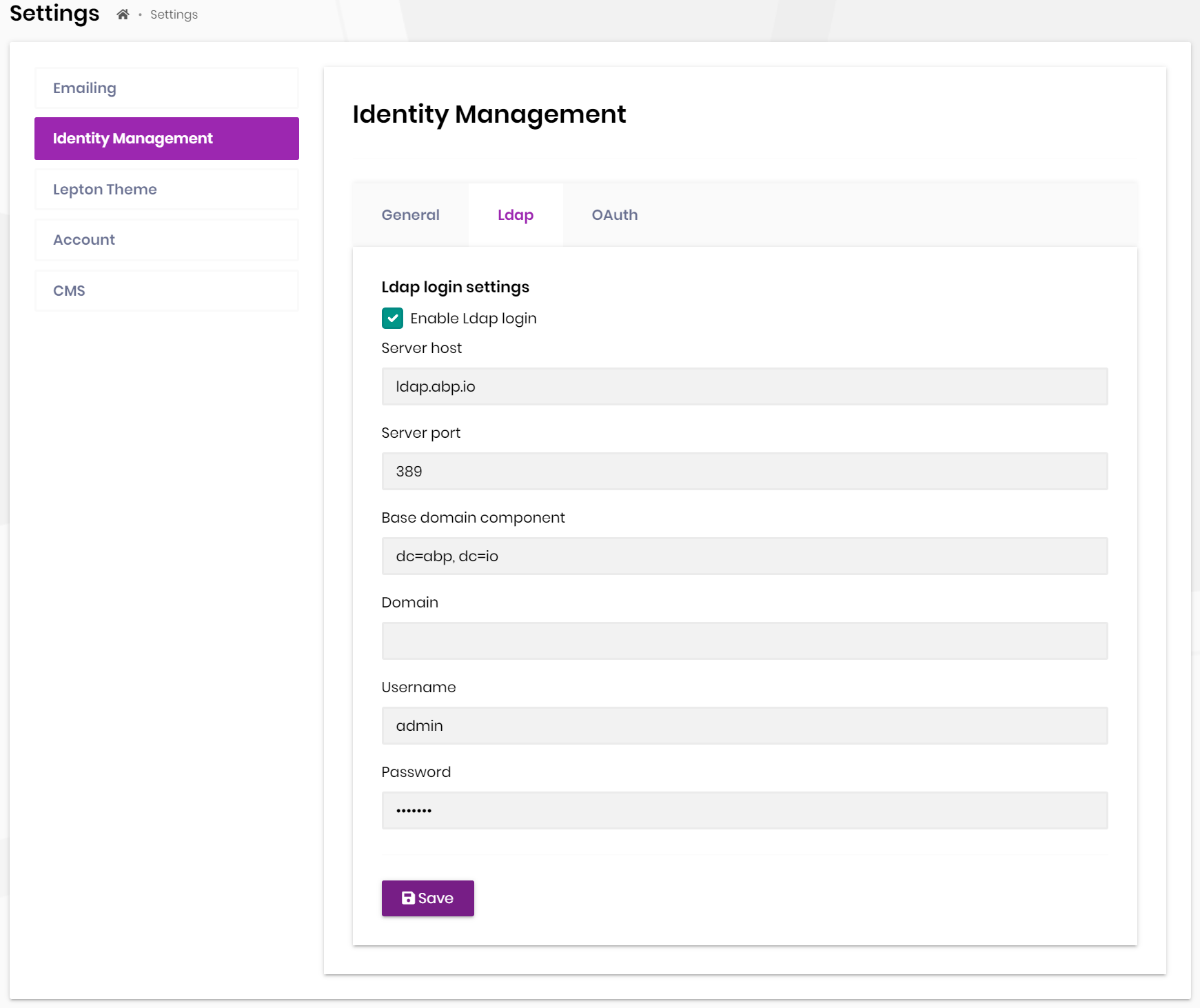
Then you can enter the LDAP user name and password on the login page for external login.
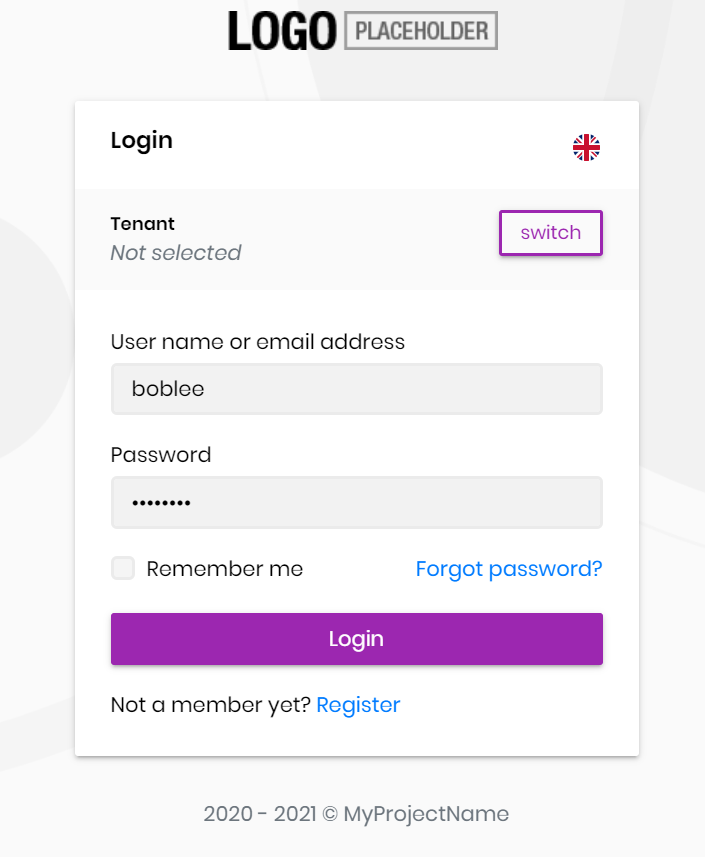
Customize built-in services
The default OpenLdapManager service uses $"cn={userName},{BaseDc}" to normalize user name, and use $"(&(uid={userName}))" to search for users, use mail as attribute name to get email.
The value of
BaseDcis the setting of theBase domain component.
If your username has a prefix or a specific format, you can override the NormalizeUserNameAsync method of OpenLdapManager to handle it. You can also customize the GetUserFilterAsync and GetUserEmailAsync methods at the same time.
[Dependency(ReplaceServices = true)]
[ExposeServices(typeof(OpenLdapManager), typeof(ILdapManager), typeof(LdapManager))]
public class VoloOpenLdapManager : OpenLdapManager
{
public VoloOpenLdapManager(ILdapSettingProvider ldapSettingProvider)
: base(ldapSettingProvider)
{
}
protected override async Task<string> NormalizeUserNameAsync(string userName)
{
// or "userName@domain
// await LdapSettingProvider.GetDomainAsync()
return Task.FromResult($"Volo\\{userName}");
}
protected override Task<string> GetUserFilterAsync(string userName)
{
// Default is $"cn={userName},{LdapOptions.BaseDc}"
return return Task.FromResult($"(&(objectClass=user)(sAMAccountName={userName}))");
}
protected override Task<string> GetUserEmailAsync(LdapEntry ldapEntry)
{
return Task.FromResult(ldapEntry.ToDirectoryEntry().GetAttribute("mail")?.GetValue<string>());
}
}
Besides, $"uid={userName}, {BaseDc}" is used in the built-in LdapExternalLoginProvider service to normalize the username, you have to change it together.
public class VoloLdapExternalLoginProvider : LdapExternalLoginProvider
{
public VoloLdapExternalLoginProvider(
IGuidGenerator guidGenerator,
ICurrentTenant currentTenant,
IdentityUserManager userManager,
IIdentityUserRepository identityUserRepository,
OpenLdapManager ldapManager,
ILdapSettingProvider ldapSettingProvider,
IFeatureChecker featureChecker,
ISettingProvider settingProvider,
IOptions<IdentityOptions> identityOptions)
: base(guidGenerator,
currentTenant,
userManager,
identityUserRepository,
ldapManager,
ldapSettingProvider,
featureChecker,
settingProvider,
identityOptions)
{
}
protected override async Task<string> NormalizeUserNameAsync(string userName)
{
// Default is $"uid={userName}, {BaseDc}"
// or "userName@domain
// await LdapSettingProvider.GetDomainAsync()
return Task.FromResult($"Volo\\{userName}");
}
}
Replace the default implementation with VoloLdapExternalLoginProvider.
public override void ConfigureServices(ServiceConfigurationContext context)
{
//...
Configure<AbpIdentityOptions>(options =>
{
options.ExternalLoginProviders.Remove(LdapExternalLoginProvider.Name);
options.ExternalLoginProviders.Add<VoloLdapExternalLoginProvider>(LdapExternalLoginProvider.Name);
});
//...
}
Test application
Testing the LDAP configuration using your application might be complicated. Therefore you can use our test application. The following dotnet console app is for testing your LDAP configuration. Before using the configuration, test in this app and see if it works.






























































