11 Answer(s)
-
0
- Solution
Root cause
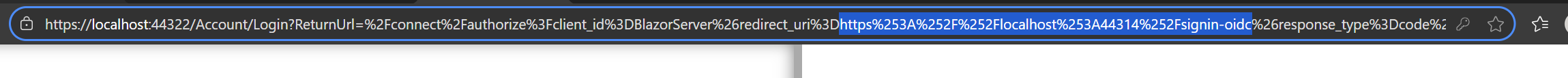
- Double-encoding of redirect_uri (e.g., https%253A%252F%252F...) typically happens when the ReturnUrl you pass to the Account/Login endpoint is already URL-encoded and then encoded again by the login page/pipeline.
- In ABP’s OpenIddict flow, the ReturnUrl (which wraps the original /connect/authorize request) must be a plain string. ABP/ASP.NET Core will encode it when constructing links.
What to check and fix
Ensure you don’t pre-encode ReturnUrl
- When redirecting to the Auth Server login page, pass the ReturnUrl value as-is, not encoded.
- Examples of correct and incorrect use:
- Correct: https://<auth-server>/Account/Login?ReturnUrl=/connect/authorize?client_id=BlazorServer&redirect_uri=https://localhost:44314/signin-oidc&response_type=code&scope=openid%20profile
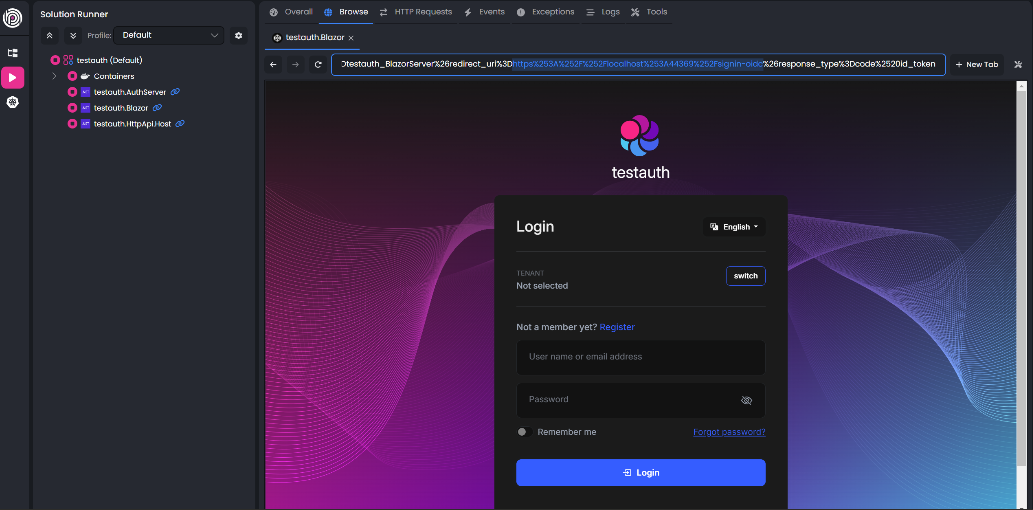
- Incorrect (double-encoded redirect_uri inside ReturnUrl): https://<auth-server>/Account/Login?ReturnUrl=%2Fconnect%2Fauthorize%3Fclient_id%3DBlazorServer%26redirect_uri%3Dhttps%253A%252F%252Flocalhost%253A44314%252Fsignin-oidc...
- If you build this URL in your client, remove manual encoding for the entire ReturnUrl. Only the inner query string should be raw; ASP.NET Core will properly encode it on redirect.
Don’t re-wrap or re-encode in custom middleware
- If you added middleware or custom logic that captures ReturnUrl and re-encodes it, remove that step. Only forward the original ReturnUrl string.
Validate RedirectAllowedUrls on the Auth Server
- In the Auth Server’s appsettings.json, set App:RedirectAllowedUrls to include your client URLs (Blazor Server, etc.). This prevents OpenIddict from rejecting valid redirects and avoids custom workarounds that often cause double encoding: { "App": { "RedirectAllowedUrls": "https://localhost:44314,https://yourclient.example.com" } }
- Restart after changes.
Verify client OpenIddict/OIDC handler configuration
- For Blazor Server (or MVC) clients using Microsoft.AspNetCore.Authentication.OpenIdConnect, do not manually encode redirect_uri. The handler will send it correctly.
- Ensure CallbackPath/signin-oidc matches the redirect URI registered in the OpenIddict client application.
Quick detection pattern
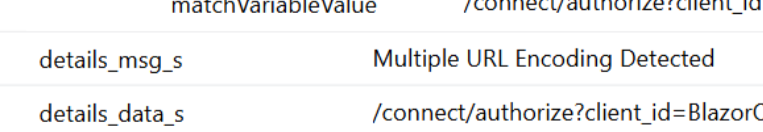
- If you see https%253A within the redirect_uri (note “%25” which is the percent sign encoded), your code has encoded an already encoded URL. Fix by removing your first encoding step.
Optional safeguard (only if you can’t quickly remove pre-encoding at source)
- As a temporary mitigation in your Auth Server login action, you could detect and decode once if the redirect_uri contains “%253A”, but this is not recommended as a long-term fix. The correct solution is to stop pre-encoding on the caller side.
- Sources
- ABP OpenIddict deployment note (RedirectAllowedUrls) — validated:
- https://abp.io/docs/latest/solution-templates/layered-web-application/deployment/openiddict-deployment
- ABP Framework GitHub (reference for module/flow behavior):
- https://github.com/abpframework/abp
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
We have not encoded it in our code. It is getting encoded from the package.
-
0
hi
How can I reproduce it in a new template project?
Can you share the
harfile of all requests?https://abp.io/support/questions/8622/How-to-enable-Debug-logs-for-troubleshoot-problems#answer-3a1a1c4b-691e-3403-98b9-5f23fa024759
liming.ma@volosoft.com
Thanks,.
-
0
hi
The request in the
harfile seems to have no problem.How can I reproduce it in a new template project?
Thanks.
-
0
-
0
hi
Can Blazor server log in successfully via the auth server website?
If not what is the error screenshot?
Thanks.
-
0
-
0
Thanks, I will check this case.
-
0
-
0
Hi, We currently don’t have access to the environment and are awaiting their response on whether it can be excluded.
-
0
Thanks. 👍