- Exception message and full stack trace:
- Steps to reproduce the issue:
Blazor Server
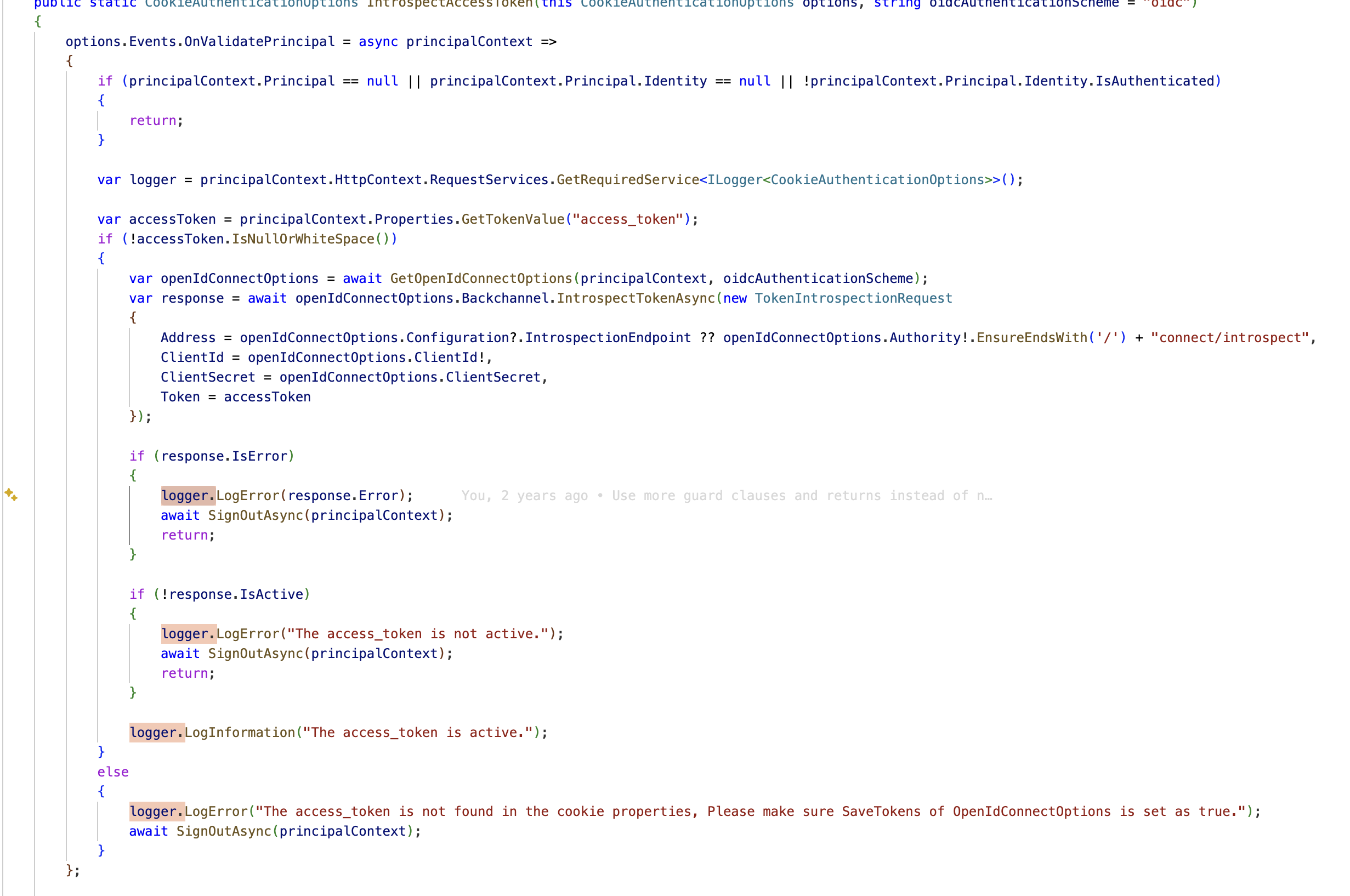
v7.2.2 project template ,use \framework\src\Volo.Abp.AspNetCore\Microsoft\Extensions\DependencyInjection\CookieAuthenticationOptionsExtensions.cs
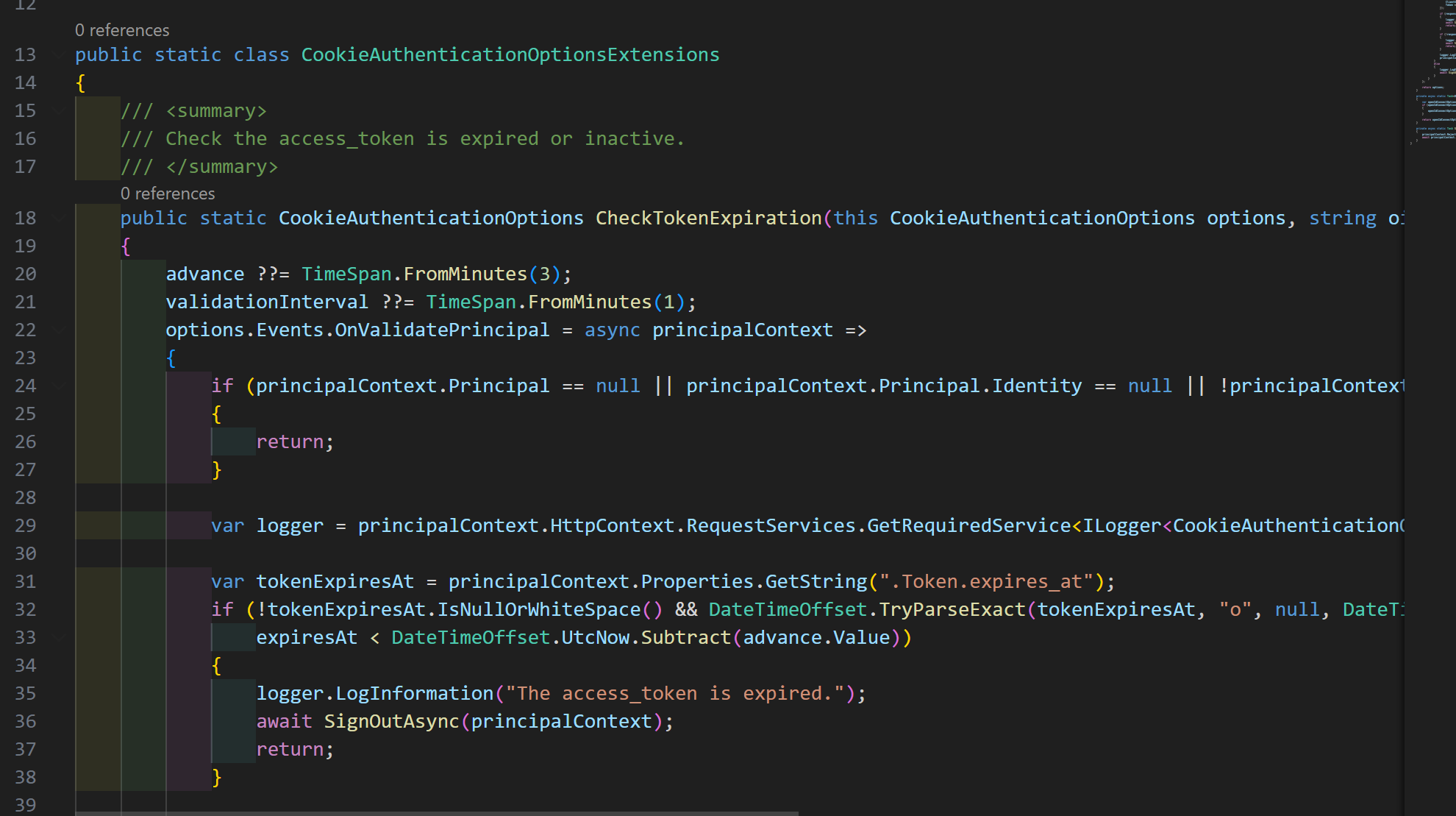 v8.3.4 project template ,use \framework\src\Volo.Abp.AspNetCore.Components.Server\Microsoft\AspNetCore\Authentication\Cookies\CookieAuthenticationOptionsExtensions.cs
v8.3.4 project template ,use \framework\src\Volo.Abp.AspNetCore.Components.Server\Microsoft\AspNetCore\Authentication\Cookies\CookieAuthenticationOptionsExtensions.cs

16 Answer(s)
-
0
- Solution
What they do
- CheckTokenExpiration (used in older templates, e.g., ABP 7.x Blazor Server):
- Reads the access token expiration time stored in the auth cookie properties (typically .Token.expires_at).
- On each cookie validation (OnValidatePrincipal), it compares the stored expiration against current time (with an optional advance window) and signs the user out if the token is expired or about to expire.
- It is a local check only. It does not contact the Authorization Server. If the access token was revoked early (before its exp claim), this method won’t detect it.
- IntrospectAccessToken (used in newer templates, e.g., ABP 8.x Blazor Server):
- On each cookie validation (OnValidatePrincipal), it fetches the access_token from the cookie properties and calls the OIDC/OAuth2 token introspection endpoint via the OpenIdConnect backchannel using TokenIntrospectionRequest.
- If the response indicates the token is inactive/expired, it signs the user out.
- This is a server-side, authoritative check. It detects early revocation or other invalidation even if the token’s exp hasn’t passed.
- CheckTokenExpiration (used in older templates, e.g., ABP 7.x Blazor Server):
Why ABP moved from CheckTokenExpiration to IntrospectAccessToken for Blazor Server templates
- To prevent “desynchronization” scenarios where the UI still considers the user authenticated while the token used to call downstream services is already invalid or has been revoked.
- Introspection ensures the cookie session always reflects the current validity status of the access token on the Auth Server/OpenIddict.
When to use which
- Use IntrospectAccessToken if your Auth Server supports RFC 7662 token introspection (OpenIddict/Auth Server in ABP does) and you need immediate revocation/blacklist awareness or multi-module/microservice consistency.
- Use CheckTokenExpiration only if you can’t use introspection. It’s lighter but only checks the client-stored expiration timestamp and can miss revocations.
How to configure in Blazor Server (ABP 8.x)
public override void ConfigureServices(ServiceConfigurationContext context) { Configure<CookieAuthenticationOptions>(IdentityConstants.ApplicationScheme, options => { // Preferred in v8.x: options.IntrospectAccessToken(oidcAuthenticationScheme: OpenIdConnectDefaults.AuthenticationScheme); // If you cannot introspect, fallback: // options.CheckTokenExpiration(); // optional: pass advance/validationInterval }); }- Sources
- https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.AspNetCore/Microsoft/Extensions/DependencyInjection/CookieAuthenticationOptionsExtensions.cs
- https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.AspNetCore.Components.Server/Microsoft/AspNetCore/Authentication/Cookies/CookieAuthenticationOptionsExtensions.cs
- https://abp.io/support/questions/5071
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
access_token not expired check
-
0
hi
Which version works for you?
MVC or BLazor Server
Thanks.
-
0
v8.3.4 Blazor Server ,use IntrospectAccessToken ,menu is disable
-
0
What are the output logs of
IntrospectAccessToken? -
0
我们有时还会遇到菜单丢失的问题
-
0
-
0
没有。Error 如下 [2025-12-23 09:50:29.234 +00:00] [ERR] [Volo.Abp.AspNetCore.Mvc.ExceptionHandling.AbpExceptionFilter] A task was canceled. System.Threading.Tasks.TaskCanceledException: A task was canceled. at Volo.Abp.Threading.SemaphoreSlimExtensions.LockAsync(SemaphoreSlim semaphoreSlim, CancellationToken cancellationToken) at Volo.Abp.Caching.DistributedCache
2.GetOrAddAsync(TCacheKey key, Func1 factory, Func1 optionsFactory, Nullable1 hideErrors, Boolean considerUow, CancellationToken token) at Volo.Abp.Identity.IdentityDynamicClaimsPrincipalContributorCache.GetAsync(Guid userId, Nullable1 tenantId) at Volo.Abp.Identity.IdentityDynamicClaimsPrincipalContributor.ContributeAsync(AbpClaimsPrincipalContributorContext context) at Volo.Abp.Security.Claims.AbpClaimsPrincipalFactory.InternalCreateAsync(AbpClaimsPrincipalFactoryOptions options, ClaimsPrincipal existsClaimsPrincipal, Boolean isDynamic) at Volo.Abp.Security.Claims.AbpClaimsPrincipalFactory.CreateDynamicAsync(ClaimsPrincipal existsClaimsPrincipal) at Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync() at Microsoft.AspNetCore.Mvc.Infrastructure.ActionMethodExecutor.TaskOfIActionResultExecutor.Execute(ActionContext actionContext, IActionResultTypeMapper mapper, ObjectMethodExecutor executor, Object controller, Object[] arguments) at Microsoft.AspNetCore.Mvc.Infrastructure.ControllerActionInvoker.<InvokeActionMethodAsync>g__Awaited|12_0(ControllerActionInvoker invoker, ValueTask1 actionResultValueTask) at Microsoft.AspNetCore.Mvc.Infrastructure.ControllerActionInvoker.<InvokeNextActionFilterAsync>g__Awaited|10_0(ControllerActionInvoker invoker, Task lastTask, State next, Scope scope, Object state, Boolean isCompleted) at Microsoft.AspNetCore.Mvc.Infrastructure.ControllerActionInvoker.Rethrow(ActionExecutedContextSealed context) at Microsoft.AspNetCore.Mvc.Infrastructure.ControllerActionInvoker.Next(State& next, Scope& scope, Object& state, Boolean& isCompleted) at Microsoft.AspNetCore.Mvc.Infrastructure.ControllerActionInvoker.InvokeInnerFilterAsync() --- End of stack trace from previous location --- at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.<InvokeNextExceptionFilterAsync>g__Awaited|26_0(ResourceInvoker invoker, Task lastTask, State next, Scope scope, Object state, Boolean isCompleted) at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.Rethrow(ExceptionContextSealed context) at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.Next(State& next, Scope& scope, Object& state, Boolean& isCompleted) at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.InvokeNextResourceFilter() --- End of stack trace from previous location --- at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.Rethrow(ResourceExecutedContextSealed context) at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.Next(State& next, Scope& scope, Object& state, Boolean& isCompleted) at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.InvokeFilterPipelineAsync() --- End of stack trace from previous location --- -
0
如何在一个新的Blazor Server app 项目模版中复现问题? 步骤是?
-
0
-
0
[ERR] [Microsoft.AspNetCore.Antiforgery.DefaultAntiforgery] An exception was thrown while deserializing the token. Microsoft.AspNetCore.Antiforgery.AntiforgeryValidationException: The antiforgery token could not be decrypted. ---> System.Security.Cryptography.CryptographicException: The key {3d2570ea-25e7-4481-b585-2e976de1fd5f} was not found in the key ring. For more information go to https://aka.ms/aspnet/dataprotectionwarning at Microsoft.AspNetCore.DataProtection.KeyManagement.KeyRingBasedDataProtector.UnprotectCore(Byte[] protectedData, Boolean allowOperationsOnRevokedKeys, UnprotectStatus& status) at Microsoft.AspNetCore.Antiforgery.DefaultAntiforgeryTokenSerializer.Deserialize(String serializedToken) --- End of inner exception stack trace --- at Microsoft.AspNetCore.Antiforgery.DefaultAntiforgeryTokenSerializer.Deserialize(String serializedToken) at Microsoft.AspNetCore.Antiforgery.DefaultAntiforgery.GetCookieTokenDoesNotThrow(HttpContext httpContext) [2025-12-24 08:08:42.202 +00:00] [ERR] [Microsoft.EntityFrameworkCore.Database.Transaction] An error occurred using a transaction.
-
0
详细的步骤是?
- 运行一个blazor server app tiered
之后呢?
谢谢
-
0
问下,什么情况下会触发找个错误,是AspNetCoreAbpAntiForgeryManager 的SetCookie 么 [ERR] [Microsoft.AspNetCore.Antiforgery.DefaultAntiforgery] An exception was thrown while deserializing the token. Microsoft.AspNetCore.Antiforgery.AntiforgeryValidationException: The antiforgery token could not be decrypted. ---> System.Security.Cryptography.CryptographicException: The key {3d2570ea-25e7-4481-b585-2e976de1fd5f} was not found in the key ring. For more information go to https://aka.ms/aspnet/dataprotectionwarning at Microsoft.AspNetCore.DataProtection.KeyManagement.KeyRingBasedDataProtector.UnprotectCore(Byte[] protectedData, Boolean allowOperationsOnRevokedKeys, UnprotectStatus& status) at Microsoft.AspNetCore.Antiforgery.DefaultAntiforgeryTokenSerializer.Deserialize(String serializedToken) --- End of inner exception stack trace --- at Microsoft.AspNetCore.Antiforgery.DefaultAntiforgeryTokenSerializer.Deserialize(String serializedToken) at Microsoft.AspNetCore.Antiforgery.DefaultAntiforgery.GetCookieTokenDoesNotThrow(HttpContext httpContext) [2025-12-24 08:08:42.202 +00:00] [ERR] [Microsoft.EntityFrameworkCore.Database.Transaction] An error occurred using a transaction.
-
0
The antiforgery token could not be decrypted.
大概率是你的应用程序没有持久化持DataProtection的加密 Key 每次启动都使用了一个新的key, 导致之前的cookies无法解密.
又或者有其他应用程序也使用了
localhost作为域名, 然后写入了新的cookie. 导致无法解密 -
0
是的,查到了 1 abp AbpApplicationConfigurationController.cs GetAsync AntiForgeryManager.SetCookie(); 2 abp AspNetCoreAbpAntiForgeryManager.cs SetCookie return _antiforgery.GetAndStoreTokens(_httpContextAccessor.HttpContext!).RequestToken!; 3 aspnetcore DefaultAntiforgery.cs GetAndStoreTokens var tokenSet = Serialize(antiforgeryFeature); 4 aspnetcore DefaultAntiforgeryTokenSerializer.cs var unprotectedBytes = _cryptoSystem.Unprotect(tokenBytes); throw new AntiforgeryValidationException(Resources.AntiforgeryToken_DeserializationFailed, innerException);
-
0
恩 你可以忽略这个csrf错误, 看看如何复现上述的菜单消息的问题. 当你测试的时候你可以在多个浏览器或者隐私标签中打开localhost来测试