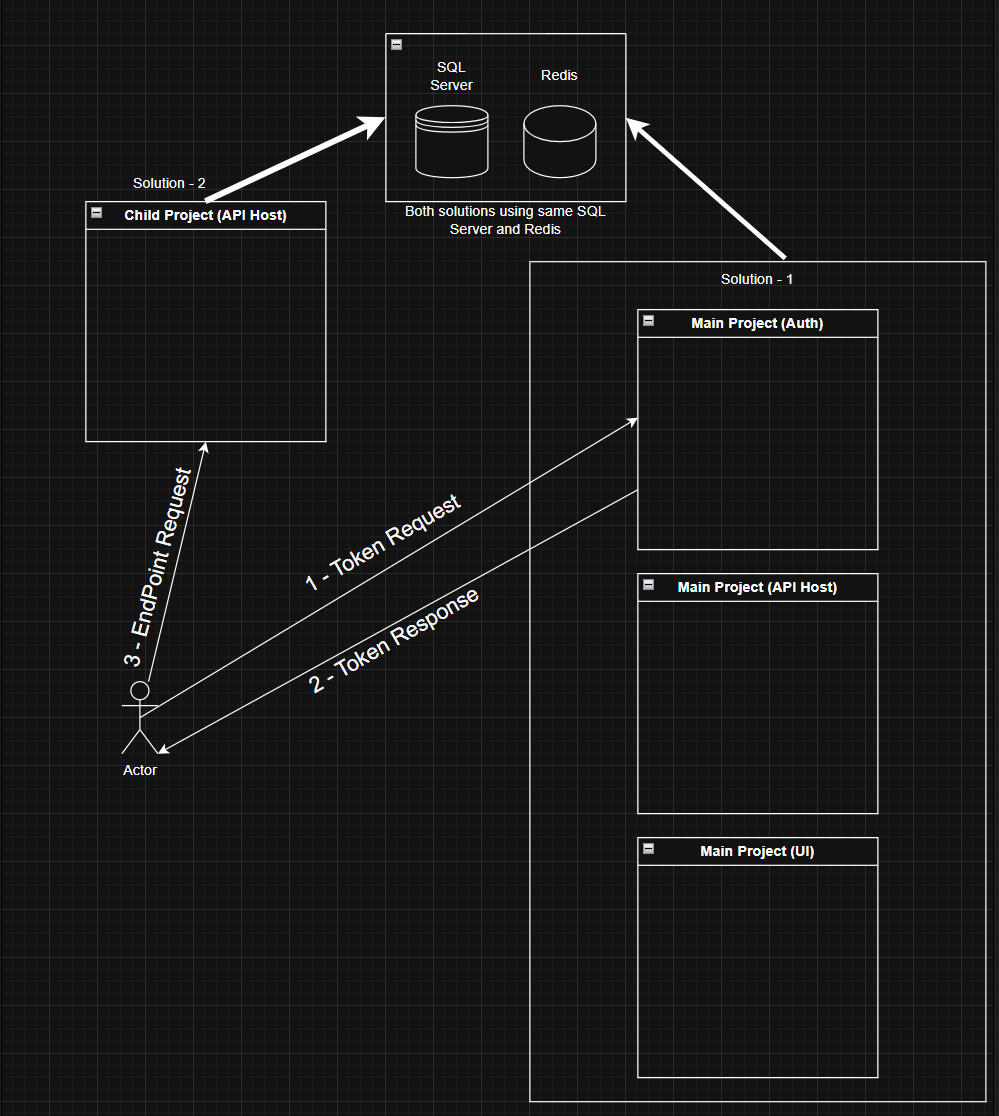
Hi, I have N-Tiered project which have UI, API Host and Auth (MainProject). So I have a another N-Tiered project just has Api Host there isn't UI and Auth(ChildProject). I configured appsettings of ChildProject for Auth into MainProject. I use Authorized attribute with Policy not role or scheme name. I Authorized via swagger or postman and I request an endpoint of ChildProject with got token. But I get 401 error in everytime. I tried show my projects relations like follow image.
I want to authorized via MainProject Auth Server and want to use Policy like [Authorize(xxxWebAPIPermissions.WCFService.Default)] in ChildProject endpoints. Can I do that?
NOTE: I authorized with admin user so it has all permissions include that use in end points of Childproject policy permission.
9 Answer(s)
-
0
- Yes, you can do this
You can absolutely have:
- One Auth Server (MainProject)
- Multiple API Hosts (MainProject API Host + ChildProject API Host)
- Use
[Authorize(ChildProjectPermissions.Something)]on ChildProject endpoints
…as long as both API hosts validate the same access token correctly and the permissions are defined/seeded consistently.
Your 401 means the ChildProject is not accepting the token (authentication fails) before it even reaches the ABP permission system.
- Configure ChildProject to trust MainProject Auth Server
In
ChildProject.HttpApi.Host:appsettings.json
"AuthServer": { "Authority": "https://MAIN-PROJECT-AUTH-URL", // MainProject Auth server URL "RequireHttpsMetadata": "false", // true in production with HTTPS "SwaggerClientId": "ChildProject_Swagger" // optional, for swagger auth }, "Jwt": { "Authority": "https://MAIN-PROJECT-AUTH-URL", "Audience": "ChildProject" // see step 3 }(or follow the same
AuthServersection structure you already use in MainProject HttpApi.Host, just changing theAudienceif needed.)HttpApiHostModule – ConfigureServices
public override void ConfigureServices(ServiceConfigurationContext context) { var configuration = context.Services.GetRequiredService<IConfiguration>(); ConfigureAuthentication(context, configuration); } private void ConfigureAuthentication(ServiceConfigurationContext context, IConfiguration configuration) { context.Services.AddAuthentication("Bearer") .AddJwtBearer("Bearer", options => { options.Authority = configuration["AuthServer:Authority"]; options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]); options.Audience = "ChildProject"; // must match the audience of the token // (temporarily you can disable audience validation to test) // options.TokenValidationParameters.ValidateAudience = false; }); }Startup pipeline (OnApplicationInitialization)
Make sure the middleware order includes both authentication and authorization:
public override void OnApplicationInitialization(ApplicationInitializationContext context) { var app = context.GetApplicationBuilder(); app.UseCorrelationId(); app.UseRouting(); app.UseCors(); app.UseAuthentication(); // BEFORE multi-tenancy & authorization app.UseAbpRequestLocalization(); app.UseMultiTenancy(); app.UseAuthorization(); app.UseSwagger(); app.UseAbpSwaggerUI(options => { ... }); app.UseAuditing(); app.UseConfiguredEndpoints(); }If
UseAuthentication()is missing or in wrong order, you will also constantly get 401.
- Make sure the token is valid for ChildProject
The token you get from MainProject must be accepted by ChildProject:
In MainProject Auth Server (OpenIddict data seed / identity seed contributor), you must define an API scope / resource that represents ChildProject, for example
"ChildProject".Add that scope to the client that obtains the token (Angular, Swagger, Postman client, etc.).
When you request a token, request that scope:
- For Swagger/OpenID: include
ChildProjectin the scopes. - For Postman:
scope=... ChildProject.
- For Swagger/OpenID: include
The resulting token must either:
- Contain
aud="ChildProject", and you setoptions.Audience = "ChildProject", or - You set
ValidateAudience = false(for testing only) so that any token from the same authority is accepted.
- Contain
If the
audin the token doesn’t match what ChildProject expects, you will see 401 from the JWT middleware, even though the same token works on the MainProject API Host.
- Share permission definitions between Main and Child projects
To be able to use:
[Authorize(xxxWebAPIPermissions.WCFService.Default)] public class MyChildController : AbpController { ... }do the following:
Permission definition provider
Put yourxxxWebAPIPermissionsand the correspondingPermissionDefinitionProviderin a shared application contracts project that is referenced by:- MainProject Auth Server (so permissions can be assigned to roles/users)
- MainProject API Host
- ChildProject API Host
Module dependency
In
ChildProjectApplicationContractsModule(or HttpApi module), depend on the module that contains the permission provider:
[DependsOn( typeof(AbpAuthorizationAbstractionsModule), typeof(MySharedPermissionsModule) // where your PermissionDefinitionProvider lives )] public class ChildProjectApplicationContractsModule : AbpModule { }- Seed permissions in MainProject (as you already do).
As long as the user has that permission (directly or via role), ABP’s permission checker in ChildProject will read it (claims + database) and authorize the policy.
If authentication is correct and the user really has the permission, then failing
[Authorize(…)]would give 403 Forbidden, not 401.
Since you get 401, it’s almost certainly token validation (authentication) in ChildProject, not the permission policy itself.
- Quick checklist
On ChildProject HttpApi.Host:
- [ ]
UseAuthentication()is present and beforeUseAuthorization(). - [ ]
AddAuthentication().AddJwtBearer()is configured to use MainProject AuthServerAuthority. - [ ]
Audienceand token’saud(orValidateAudience = false) are aligned. - [ ] Tokens requested include the ChildProject scope/audience.
- [ ] Permission definitions project is shared and referenced.
- [ ] Same database (you already have) so user, role, permission data are visible.
Once these are done, you can:
- Get token from MainProject Auth Server.
- Call ChildProject endpoints with
Authorization: Bearer <token>. [Authorize(xxxWebAPIPermissions.WCFService.Default)]will work as expected.
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
- Yes, you can do this
-
0
Above answer isn't enough for me and it doesn't solve my problem. Please redirect a person.
-
0
-
0
hi, I shared my ChilProject Log that my catched.
2025-12-26 09:19:17.788 +03:00 [INF] Request starting HTTP/1.1 POST https://localhost:48995/api/app/xxxx-xxxxx/aaaa-bbbb-ccccc?marketCode=1 - application/json 12 2025-12-26 09:19:17.795 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. 2025-12-26 09:19:17.795 +03:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri. 2025-12-26 09:19:17.795 +03:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType. 2025-12-26 09:19:17.795 +03:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement. 2025-12-26 09:19:17.795 +03:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader. 2025-12-26 09:19:17.796 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ValidateHostHeader. 2025-12-26 09:19:17.796 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateValidatedTokens. 2025-12-26 09:19:17.796 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromAuthorizationHeader. 2025-12-26 09:19:17.796 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromBodyForm. 2025-12-26 09:19:17.796 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromQueryString. 2025-12-26 09:19:17.796 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens. 2025-12-26 09:19:17.798 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ResolveServerConfiguration. 2025-12-26 09:19:17.798 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ResolveIntrospectionEndpoint. 2025-12-26 09:19:17.799 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateIntrospectionRequest. 2025-12-26 09:19:22.740 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandler
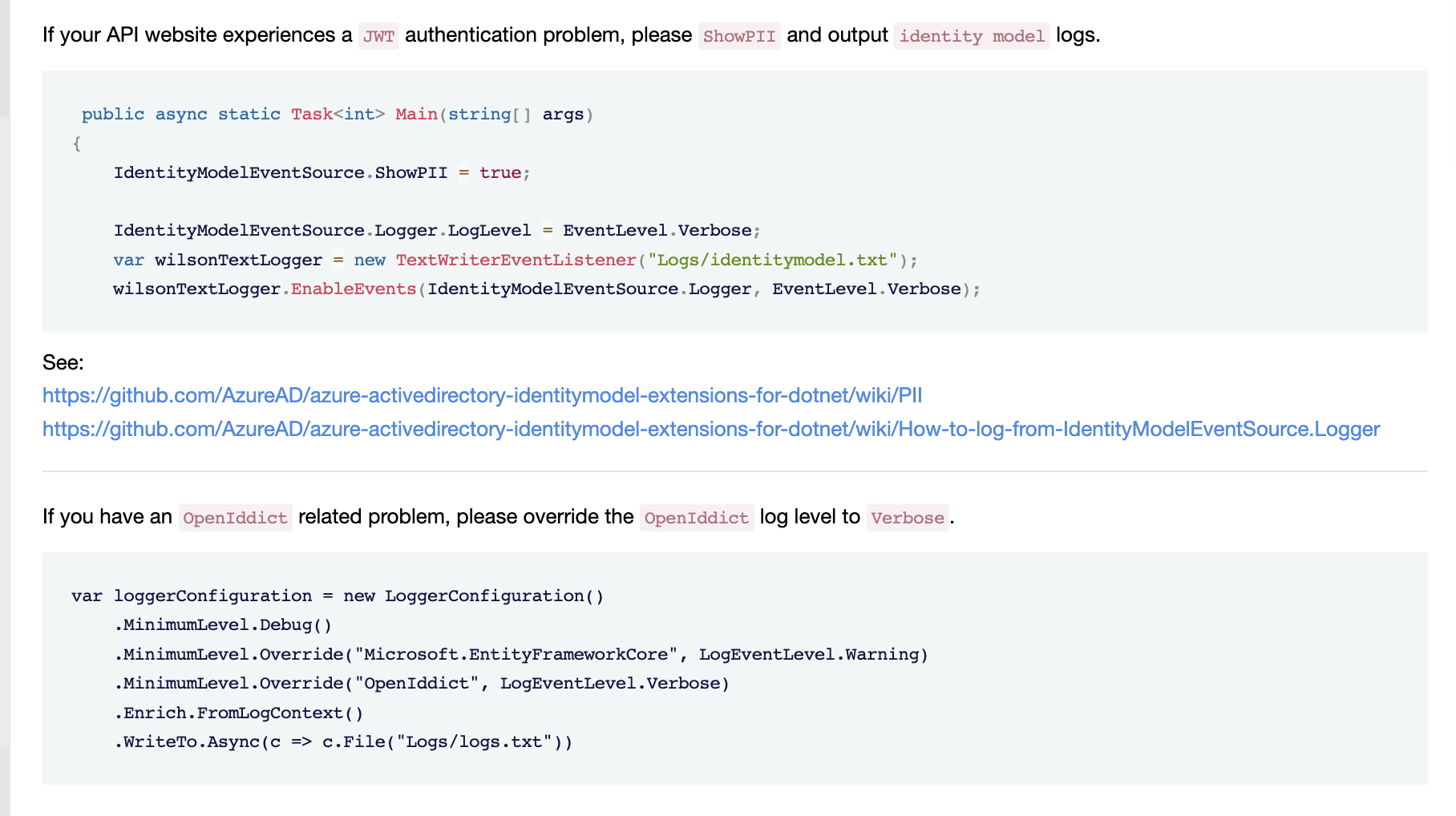
1[[OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext, OpenIddict.Validation, Version=5.8.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2025-12-26 09:19:22.740 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext was marked as handled by OpenIddict.Validation.OpenIddictValidationHandler1[[OpenIddict.Validation.OpenIddictValidationEvents+ValidateTokenContext, OpenIddict.Validation, Version=5.8.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2025-12-26 09:19:22.740 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateAccessToken. 2025-12-26 09:19:22.740 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was marked as handled by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateAccessToken. 2025-12-26 09:19:22.740 +03:00 [DBG] AuthenticationScheme: OpenIddict.Validation.AspNetCore was not authenticated. 2025-12-26 09:19:22.740 +03:00 [DBG] AuthenticationScheme: OpenIddict.Validation.AspNetCore was not authenticated. 2025-12-26 09:19:22.896 +03:00 [INF] Authorization failed. These requirements were not met: PermissionRequirement: xxxxxxAPI.Default 2025-12-26 09:19:22.900 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessChallengeContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveHostChallengeProperties. 2025-12-26 09:19:22.903 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessChallengeContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+AttachHostChallengeError. 2025-12-26 09:19:22.905 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessChallengeContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+AttachDefaultChallengeError. 2025-12-26 09:19:22.906 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessChallengeContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+AttachCustomChallengeParameters. 2025-12-26 09:19:22.907 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessChallengeContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+AttachHttpResponseCode1[[OpenIddict.Validation.OpenIddictValidationEvents+ProcessChallengeContext, OpenIddict.Validation, Version=5.8.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2025-12-26 09:19:22.907 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessChallengeContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+AttachCacheControlHeader1[[OpenIddict.Validation.OpenIddictValidationEvents+ProcessChallengeContext, OpenIddict.Validation, Version=5.8.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2025-12-26 09:19:22.910 +03:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessChallengeContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+AttachWwwAuthenticateHeader`1[[OpenIddict.Validation.OpenIddictValidationEvents+ProcessChallengeContext, OpenIddict.Validation, Version=5.8.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2025-12-26 09:19:22.913 +03:00 [INF] The response was successfully returned as a challenge response: { "error": "insufficient_access", "error_description": "The user represented by the token is not allowed to perform the requested action.", "error_uri": "https://documentation.openiddict.com/errors/ID2095" }.I use admin user to get token and admin user has all permissions and we check out in DB PermissionGrants table. NOTE:Identitymodel log was empty even I added ShowPII=true.
-
0
hi
Can you share the module code of Child Project (API Host)?
And the debug logs of your Main Project (Auth).
Thanks.
-
0
Hi,
I shared module code and main auth log section via email(musa@fintechyazilim.com).
Thanks.
-
0
hi
Why is the
TakasBankWebAPIHttpApiHostModulealso an authserver project?When you use the token obtained from
Main Project (Auth)to call the api fromChild Project (API Host). The token was checked byChild Project (API Host), which is why it failed.Thanks.
-
0
I created N-Tiered project and I removed Auth and UI layer because it makes speed project template.
Yes I know check Token in Child Project. So I can't use Policies in Authorize in Child Project. Do I? As well as If I put ChildProject into MainProject solution then Does check token MainProject and can i use policiy (Permissions in Applicaiton.Contract)?
Thanks.
-
0
hi
Will you use
OpenIddictinChild Project (API Host)project?If not. You can remove all OpenIddict from it and use
Main Project (Auth)as the authentication server. And add a JWT Bearer toChild Project (API Host)After that:
You can get a token from
Main Project (Auth)and pasing it toChild Project (API Host)Thanks.