Potentially sensitive application claims were excluded from the introspection response as the client 'EAP' was not explicitly listed as an audience.
[OpenIddict.Server.OpenIddictServerDispatcher] The response was successfully returned as a JSON document: {
"active": false
}.
The access_token is not active.
 IntrospectAccessToken 在什么情况下使用
IntrospectAccessToken 在什么情况下使用
35 Answer(s)
-
0
- Solution
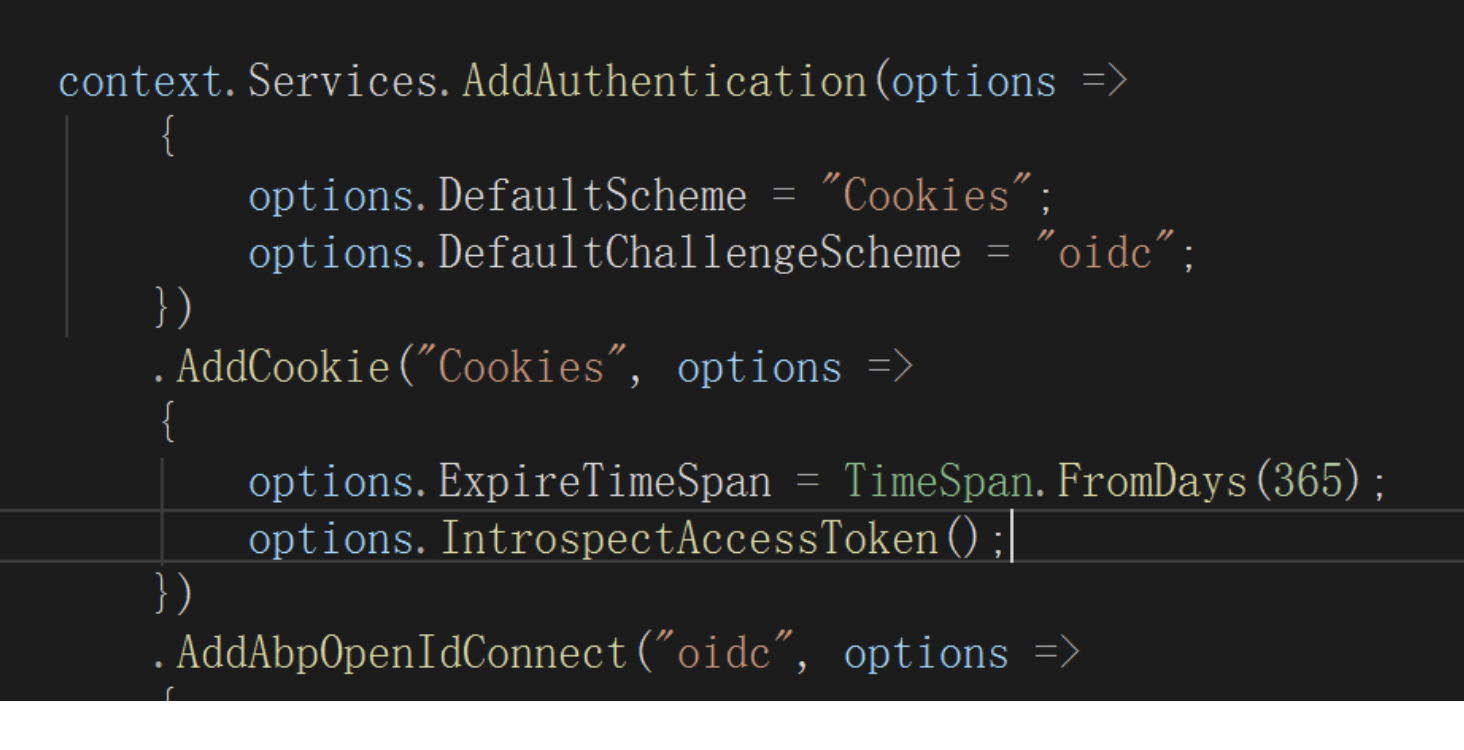
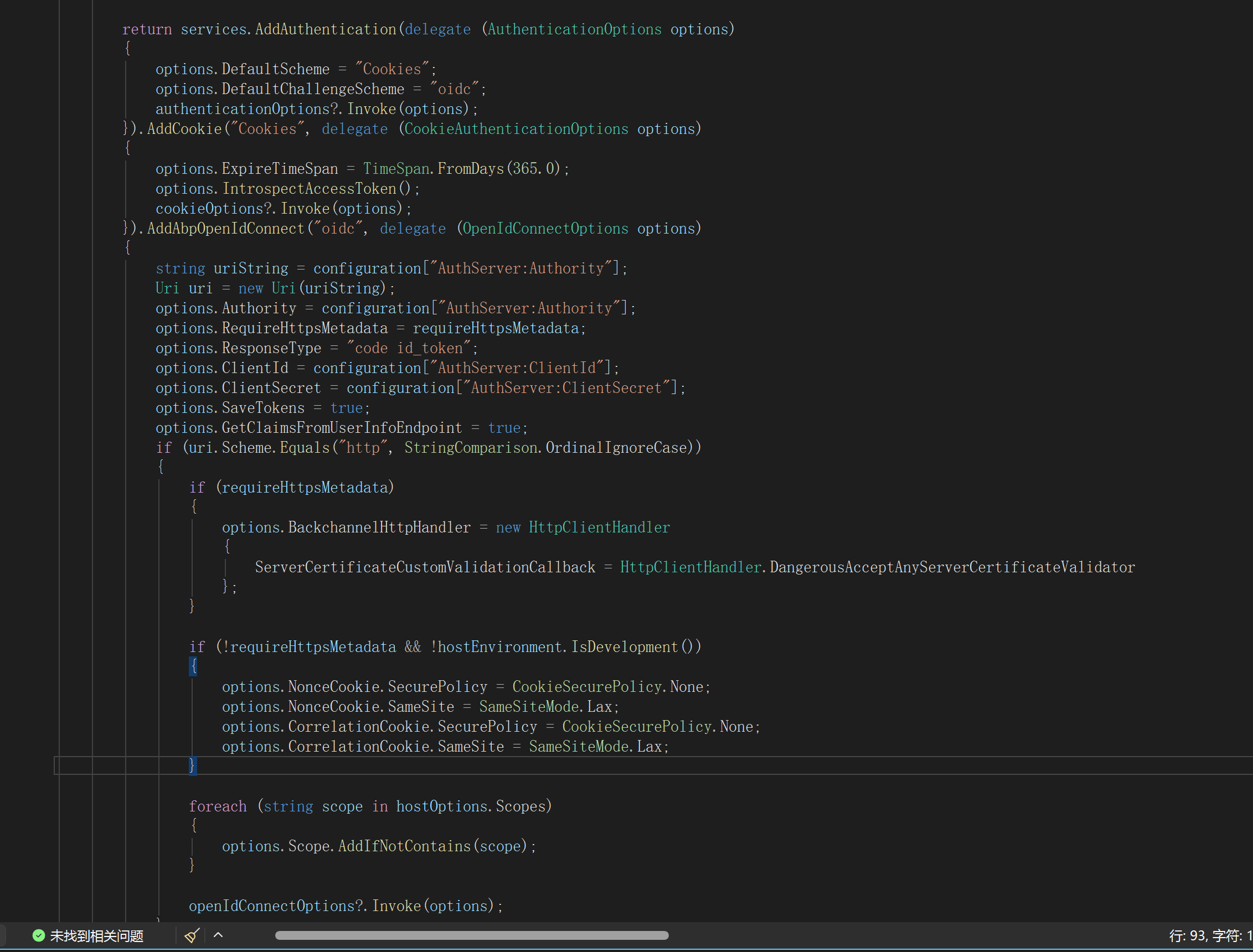
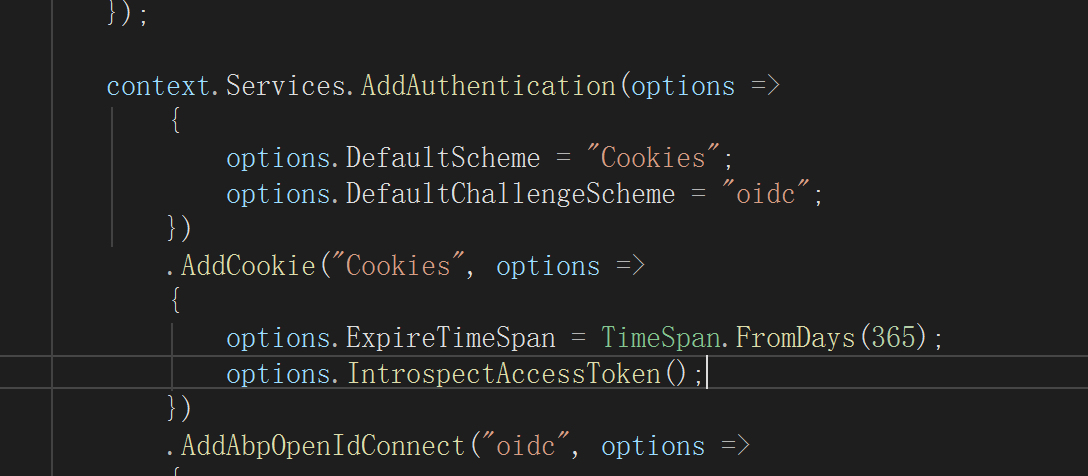
options.IntrospectAccessToken()is an ABP helper extension for cookie authentication:context.Services.AddAuthentication(options => { options.DefaultScheme = "Cookies"; options.DefaultChallengeScheme = "oidc"; }) .AddCookie("Cookies", options => { options.ExpireTimeSpan = TimeSpan.FromDays(365); options.IntrospectAccessToken(); // = old helper }) .AddAbpOpenIdConnect("oidc", options => { // ... });From the ABP source:
/// <summary> /// Check the access_token is expired or inactive. /// </summary> [Obsolete("Use CheckTokenExpiration method instead.")] public static CookieAuthenticationOptions IntrospectAccessToken( this CookieAuthenticationOptions options, string oidcAuthenticationScheme = "oidc") { return options.CheckTokenExpiration(oidcAuthenticationScheme, null, TimeSpan.FromMinutes(1)); }So:
- It hooks into
CookieAuthenticationOptions.Events.OnValidatePrincipal. - Periodically (default ~1 minute) it checks the access_token associated with the cookie:
- If token is expired or inactive (introspection active = false) it rejects the cookie principal (signs the user out).
- It is meant for scenarios where:
- You use OIDC login (
AddAbpOpenIdConnect("oidc", …)). - Cookie lifetime is long (e.g. 365 days).
- You still want the user to be logged out as soon as the access token becomes invalid, not when the cookie expires.
- You use OIDC login (
When the log shows
active: false/ audience not listedYour log:
Potentially sensitive application claims were excluded from the introspection response as the client 'EAP' was not explicitly listed as an audience.
"active": falseThis happens when the extension calls the introspection endpoint of OpenIddict and:
- The access token audience doesn’t include the current client (e.g.
EAP), so OpenIddict:- Removes sensitive claims.
- Returns
active: false.
Common reasons:
- In your OpenIddictDataSeedContributor, the client representing this Blazor Server app:
- Doesn't list the correct API/resource as audience.
- Or the API scope/audience configuration doesn’t match the token you’re sending.
Result: every validation attempt marks the token as not active, so the cookie is invalidated.
What you should do
- Prefer the new API
IntrospectAccessTokenis obsolete. Use:.AddCookie("Cookies", options => { options.ExpireTimeSpan = TimeSpan.FromDays(365); options.CheckTokenExpiration(); // new recommended helper });- Only use it when you really need token‑based sign‑out
Use
CheckTokenExpiration/IntrospectAccessTokenwhen:- The UI (Blazor Server / MVC) logs in via OIDC (
oidcscheme), and - You call protected APIs using the same access token, and
- You want the UI cookie to become invalid as soon as the access token is no longer valid.
If:
- Your UI and backend are the same application, or
- You don’t rely on the access token after login,
then you can simply remove
IntrospectAccessToken()/CheckTokenExpiration()and rely on normal cookie expiration.- If you keep it, fix the OpenIddict client/audience
If you want to keep token introspection:
- In your
OpenIddictDataSeedContributor, ensure the client for this app:- Has the correct scopes (e.g. your API scopes).
- Has the correct audiences to match the APIs the token is issued for.
- Then the introspection endpoint will return
active: truewhile the token is valid and the cookie will not be cleared.
In summary:
IntrospectAccessTokenis used to periodically verify the OIDC access token behind the cookie and log the user out when that token is no longer valid.- It’s now obsolete; use
CheckTokenExpiration(). - Use it only when you need access‑token‑driven logout; otherwise you can safely remove it.
- Your current
active: falseerror is due to OpenIddict audience/scope configuration, not ABP itself.
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
你好
完整的OpenIddict IntrospectAccessToken日志是?
-
0
[2026-01-07 16:51:58.183 +00:00] [INF] [OpenIddict.Server.OpenIddictServerDispatcher] The response was successfully returned as a JSON document: { "active": true, "iss": "http://10.166.0.106:44390/", "sub": "4d75bb07-b3de-0147-7a5c-3a1d3c88d0e8", "jti": "b66835b5-f0ab-45bd-afec-7d85e4b91e81", "token_type": "Bearer", "token_usage": "access_token", "client_id": "EAP", "iat": 1767804690, "nbf": 1767804690, "exp": 1767808290, "aud": "ControlCenter" }. [2026-01-07 16:51:58.184 +00:00] [INF] [Microsoft.AspNetCore.Hosting.Diagnostics] Request finished HTTP/1.1 POST http://10.166.0.106:44390/connect/introspect - 200 327 application/json;charset=UTF-8 18.7682ms [2026-01-07 16:51:59.429 +00:00] [INF] [Microsoft.AspNetCore.Hosting.Diagnostics] Request starting HTTP/1.1 POST http://10.166.0.106:44390/register-health-check - application/json; charset=utf-8 null [2026-01-07 16:51:59.430 +00:00] [INF] [Microsoft.AspNetCore.Hosting.Diagnostics] Request finished HTTP/1.1 POST http://10.166.0.106:44390/register-health-check - 200 0 null 0.7973ms [2026-01-07 16:52:00.706 +00:00] [INF] [Microsoft.AspNetCore.Hosting.Diagnostics] Request starting HTTP/1.1 POST http://10.166.0.106:44390/register-health-check - application/json; charset=utf-8 null [2026-01-07 16:52:00.707 +00:00] [INF] [Microsoft.AspNetCore.Hosting.Diagnostics] Request finished HTTP/1.1 POST http://10.166.0.106:44390/register-health-check - 200 0 null 1.1336ms [2026-01-07 16:52:02.388 +00:00] [INF] [Microsoft.AspNetCore.Hosting.Diagnostics] Request starting HTTP/1.1 POST http://10.166.0.106:44390/register-health-check - application/json; charset=utf-8 null [2026-01-07 16:52:02.389 +00:00] [INF] [Microsoft.AspNetCore.Hosting.Diagnostics] Request finished HTTP/1.1 POST http://10.166.0.106:44390/register-health-check - 200 0 null 0.9464ms [2026-01-07 16:52:02.443 +00:00] [INF] [Microsoft.AspNetCore.Hosting.Diagnostics] Request starting HTTP/1.1 POST http://10.166.0.106:44390/connect/introspect - application/x-www-form-urlencoded 1339 [2026-01-07 16:52:02.444 +00:00] [INF] [OpenIddict.Server.OpenIddictServerDispatcher] The request URI matched a server endpoint: "Introspection". [2026-01-07 16:52:02.444 +00:00] [INF] [OpenIddict.Server.OpenIddictServerDispatcher] The introspection request was successfully extracted: { "token": "[redacted]", "client_id": "EMS", "client_secret": "[redacted]" }. [2026-01-07 16:52:02.465 +00:00] [INF] [OpenIddict.Server.OpenIddictServerDispatcher] The response was successfully returned as a JSON document: { "active": false }.
-
0
[2026-01-07 16:51:58.183 +00:00] [INF] [OpenIddict.Server.OpenIddictServerDispatcher] Potentially sensitive application claims were excluded from the introspection response as the client 'EAP' was not explicitly listed as an audience.
-
0
-
0
-
0
这个错误的原因是access token中Audience不包含
odic的ClientId你是否对OpenIddict做了任何的自定义修改?
如何使用默认的模版项目复现问题?
-
0
[OpenIddict.Server.OpenIddictServerDispatcher] The introspection request was rejected because the access token was issued to a different client or for another resource server.
-
0
你是否对OpenIddict做了任何的自定义修改?
如何使用默认的模版项目复现问题?
-
0
-
0
你可以移除
options.IntrospectAccessToken()将解决这个问题.之后复制这个类的源码到你的项目中
https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.AspNetCore/Microsoft/Extensions/DependencyInjection/CookieAuthenticationOptionsExtensions.cs
67行的ClientId需要来自Access token中而不是每个项目的ClientId.
https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.AspNetCore/Microsoft/Extensions/DependencyInjection/CookieAuthenticationOptionsExtensions.cs#L67
为什么多个APP没有使用相同的ClientId?
-
0
openiddict 多个应用,多个app地址,单点登录 appurl /signin-oidc
-
0
修改CheckTokenExpiration会解决问题
-
0
-
0
- Solution
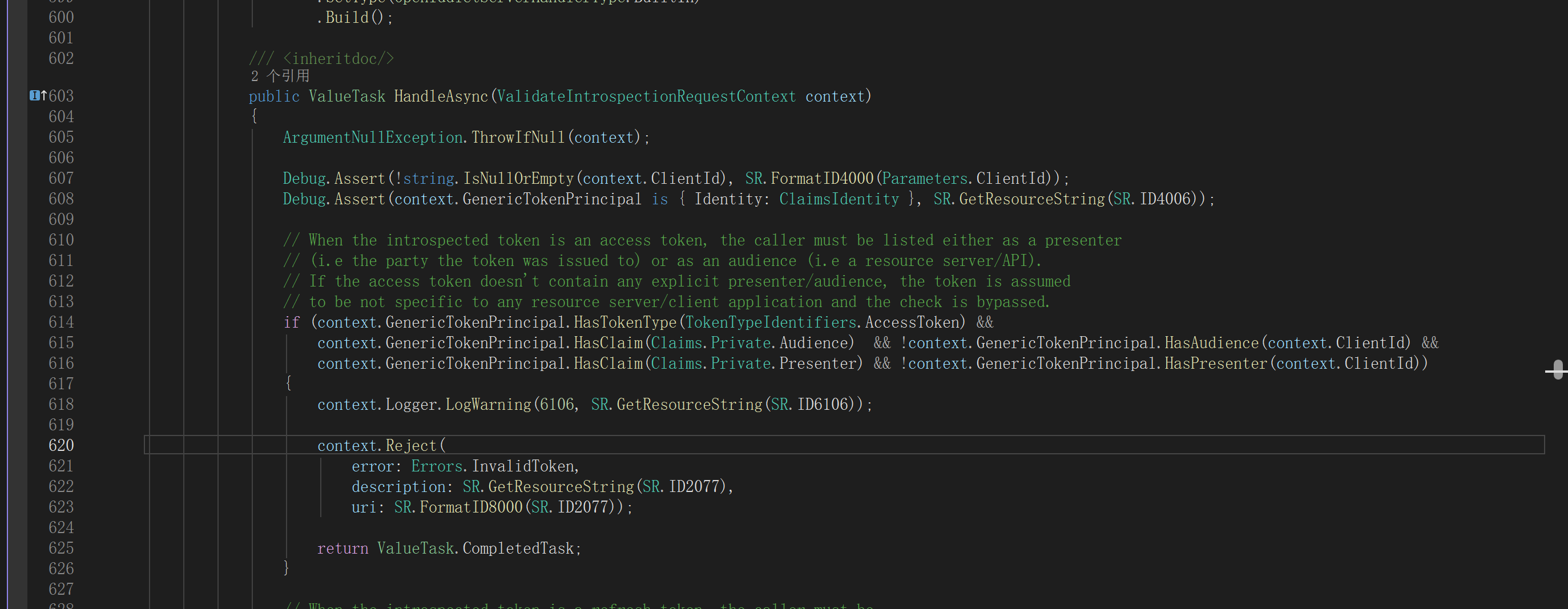
CheckTokenExpiration()andIntrospectAccessToken()are just two different ABP helpers that plug into the cookie authentication pipeline:IntrospectAccessToken()(obsolete)- Uses OpenIddict introspection endpoint and sends the cookie’s access token together with this app’s ClientId.
- OpenIddict then enforces: the caller (client doing introspection) must be in the token’s audience/presenter.
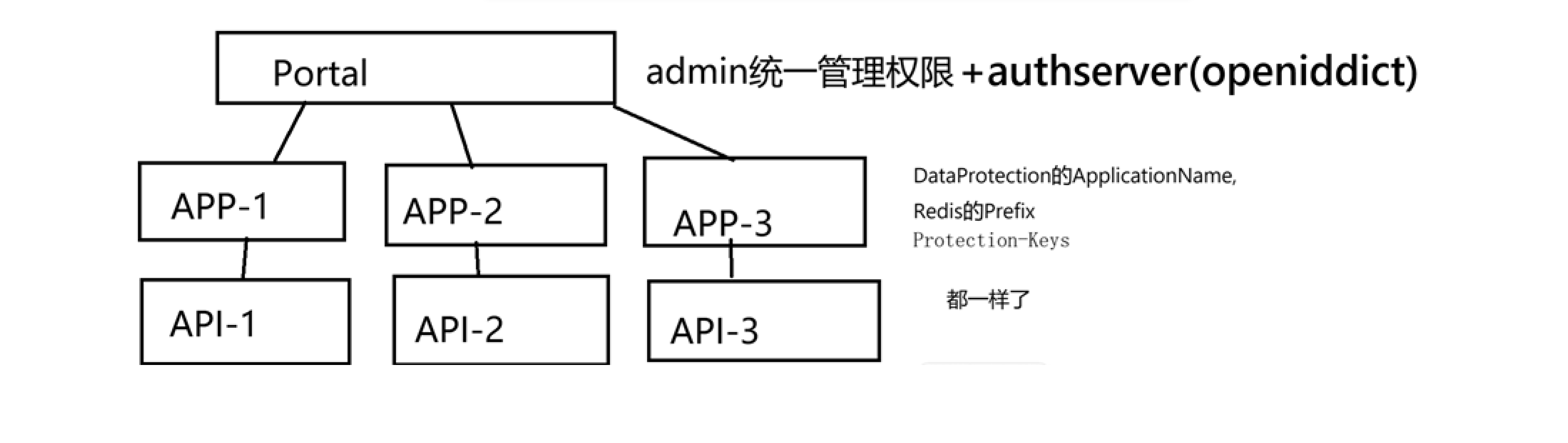
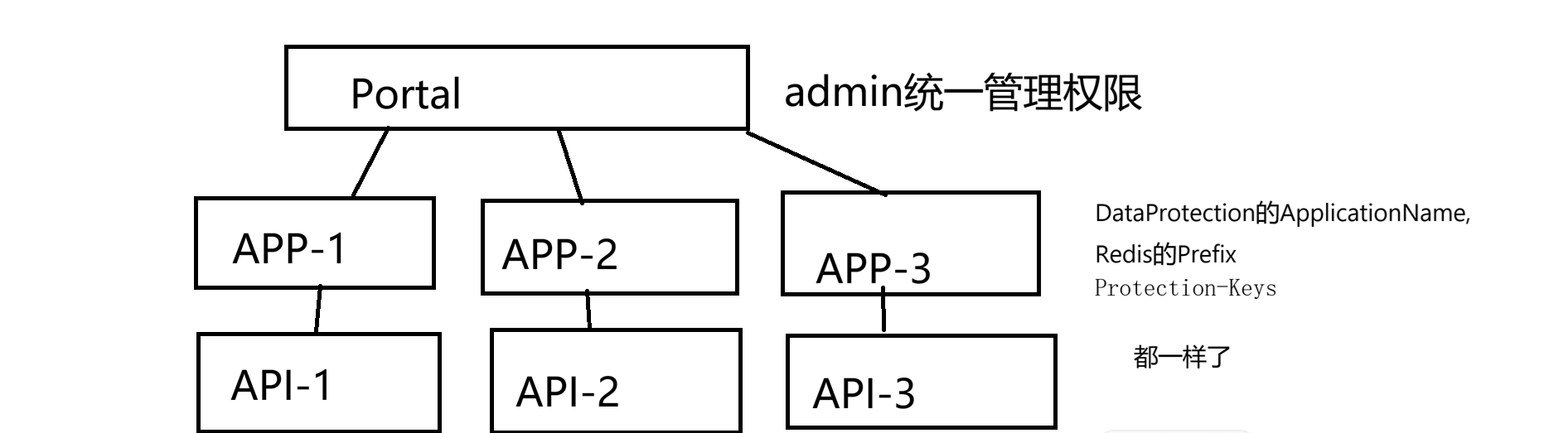
- In your scenario you have multiple apps, each with its own ClientId, but you are sharing one login (SSO).
- The access token may be issued for audience
ControlCenter(or some other client/resource). - When
APP‑2introspects it with its own ClientId, OpenIddict sees that this ClientId is not inaud/azpand rejects the request:- Log:
The introspection request was rejected because the access token was issued to a different client or for another resource server.
- Log:
- The access token may be issued for audience
- This is why some introspection calls return
active: falseeven when the token itself is valid.
CheckTokenExpiration()(new, recommended)- Does not use introspection in this strict way; it mainly checks token expiration and optionally calls user info.
- Therefore it doesn’t hit the audience/presenter restriction that is causing your current error.
Because you have many apps (Portal, APP‑1/2/3) with SSO and different OpenIddict clients,
IntrospectAccessToken()will always be fragile unless all access tokens are issued with all your frontend ClientIds as audiences.The workaround suggested in the support thread is:
- Remove
options.IntrospectAccessToken()from all apps. - Copy and adjust ABP’s implementation to your own project:
- File:
CookieAuthenticationOptionsExtensions.cs - Source:
https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.AspNetCore/Microsoft/Extensions/DependencyInjection/CookieAuthenticationOptionsExtensions.cs
- File:
- In the copied
CheckTokenExpiration/validation logic, change the ClientId used for introspection:- Instead of using each app’s own OIDC
ClientId, take the ClientId (or audience) from the access token being validated, or use a single technical client that is always present inaud. - This bypasses the “token issued to a different client/resource server” condition you saw in OpenIddict’s
ValidateIntrospectionRequesthandler.
- Instead of using each app’s own OIDC
If you do this:
- You keep the behavior you like from
IntrospectAccessToken(user is redirected to login when token is invalid/expired). - You avoid the audience mismatch when the same token is reused across multiple apps with different ClientIds.
Regarding your last comment:
Using
CheckTokenExpirationlets users access internal URLs without logging in, butIntrospectAccessTokendoes not.That difference comes from the exact validation logic inside the ABP extension. Once you copy the extension code and adapt the introspection part (ClientId/audience logic) you can:
- Keep the “force login when no valid token” behavior,
- While still supporting your multi‑client, shared cookie (
ApplicationName, RedisProtection-Keysshared) architecture.
- Sources
- ABP cookie helpers for token checking and introspection (source code):
CookieAuthenticationOptionsExtensions
https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.AspNetCore/Microsoft/Extensions/DependencyInjection/CookieAuthenticationOptionsExtensions.cs
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
hi
复制这个类的源码到你的项目中
https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.AspNetCore/Microsoft/Extensions/DependencyInjection/CookieAuthenticationOptionsExtensions.cs
67行的ClientId需要来自Access token中而不是每个项目的ClientId.
var tokenHandler = new JwtSecurityTokenHandler(); var securityToken = (JwtSecurityToken)tokenHandler.ReadToken(your_access_token); var clientid = securityToken.Claims.FirstOrDefault(c => c.Type == openiddict_client_id_claim_type)?.Value; ClientId = clientidhttps://www.nuget.org/packages/system.identitymodel.tokens.jwt/
-
0
a new way to solve it. See https://github.com/abpframework/abp/pull/24598
-
0
-
0
- Solution
The situation you see is consistent with “user has been signed‑out during the request”:
- The
application-configurationitem in cache has a key that contains the userId (this entry was created earlier, when the user was still authenticated). - When the access token becomes invalid and
IntrospectAccessToken/ your modifiedCheckTokenExpirationlogic runs, the cookie is rejected and the user is signed out. - For the
application-configurationrequest that comes after that, the current HTTP context no longer has an authenticated principal, so:ICurrentUserreturns IsAuthenticated = false andId = null.- Permission providers can’t resolve any user permissions, so
"auth": { "grantedPolicies": {} }.
- The cached item you see in Redis (or memory) is just a previous cache entry that used a key including the old userId.
It doesn’t change retroactively when the user is signed out; it will just not be reused for new anonymous requests (which use a different cache key, typically withuserId = null).
So:
currentUserall null + emptygrantedPoliciesmeans the user is no longer authenticated for that request.- The cache key still showing a userId just means there is (or was) a cached configuration for that user; it doesn’t prove that the current response was generated as that user.
If you want to make the behavior clearer/safer:
- Ensure your custom token‑validation (
CheckTokenExpiration/IntrospectAccessTokencopy) signs the user out before the application‑configuration endpoint runs (which it already appears to do). - Optionally, you can clear per‑user application‑configuration cache when you sign the user out (e.g., by injecting and removing the cache entry in your custom cookie validation logic), but this is not strictly required functionally.
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
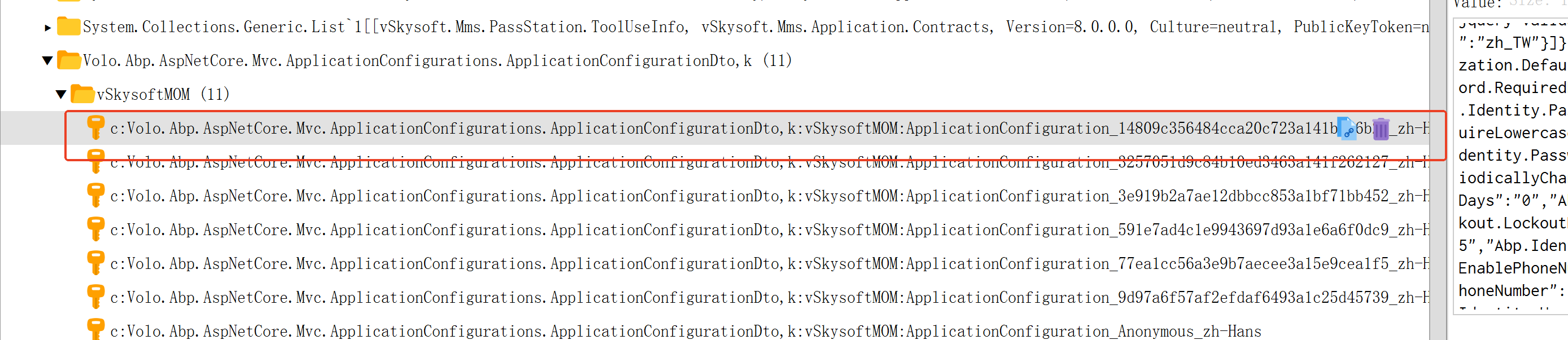
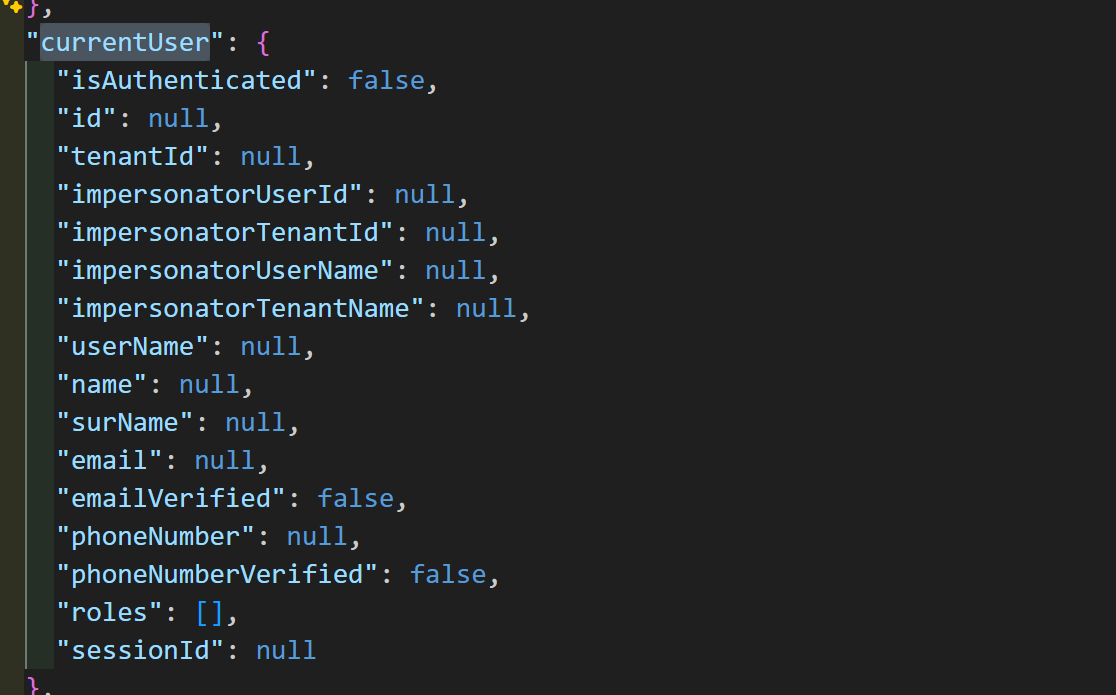
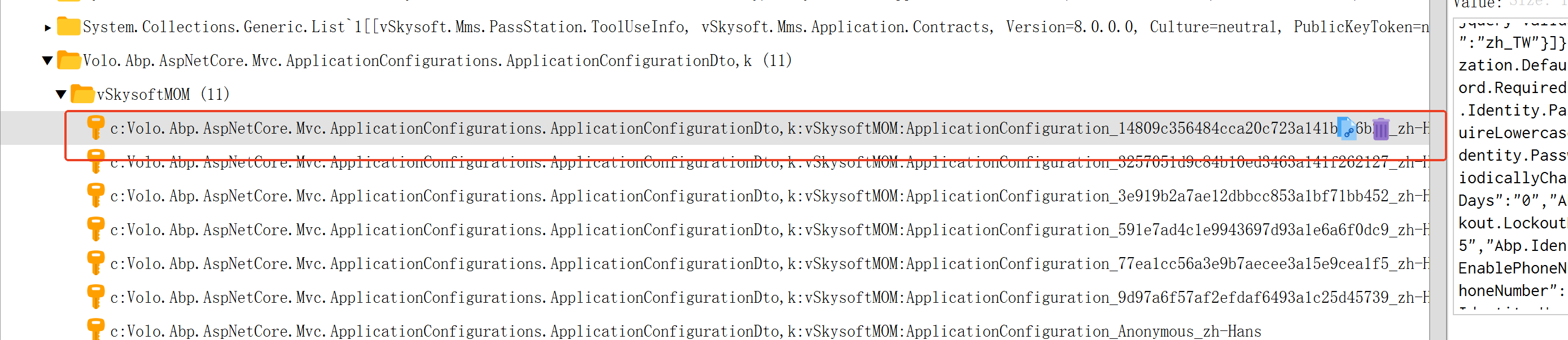
有一个现象,当权限丢失的时候,application-configuration key userid ,但是value 对应的值,currentUser is null, "auth": { "grantedPolicies": {} },
这是否导致任何问题?
-
0
blazorserver 前后端分离blazorHost ApiHost, application-configuration cache 存储请求上下文权限和身份信息。 ` public async Task
if (httpContext != null && httpContext.Items[cacheKey] is ApplicationConfigurationDto configuration) { return configuration; } configuration = (await Cache.GetOrAddAsync( cacheKey, async () => await GetRemoteConfigurationAsync(), () => new DistributedCacheEntryOptions { AbsoluteExpirationRelativeToNow = Options.ApplicationConfigurationDtoCacheAbsoluteExpiration } ))!; if (httpContext != null) { httpContext.Items[cacheKey] = configuration; } return configuration; }` 源码 MvcCachedApplicationConfigurationClient和RemotePermissionChecker
-
0
这个MvcCachedApplicationConfigurationClient缓存问题你可以参考https://github.com/abpframework/abp/pull/24486
-
0
不是一个问题,https://github.com/abpframework/abp/pull/24486 是通过角色和用户赋权之后,权限不刷新的问题(延迟问题), 没有操作用户权限情况下,权限丢失,application-configuration cache 的用户信息和权限信息都不对
-
0
没有操作用户权限情况下,权限丢失,application-configuration cache 的用户信息和权限信息都不对
如何复现问题?
步骤是?
-
0