- ABP Framework version: v9.0.2
- UI Type: MVC
- Database System: EF Core (SQL Server)
- **Tiered (for MVC) or Auth Server Separated: yes
- Exception message and full stack trace: I am back and forward on redirect URL after authenticating with Microsoft Azure AD
- Steps to reproduce the issue: I have added my configuration for OpenIdConnect and after that I am facing that issue. Also I am attaching video for reference as well. Video https://jmp.sh/jrphAyUq
These are the logs
2025-01-31 16:46:27.271 +05:30 [INF] Request starting HTTP/2 GET https://localhost:44362/Identity/OrganizationUnits - null null 2025-01-31 16:46:27.274 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. 2025-01-31 16:46:27.275 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri. 2025-01-31 16:46:27.275 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType. 2025-01-31 16:46:27.275 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType. 2025-01-31 16:46:27.275 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement. 2025-01-31 16:46:27.275 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader. 2025-01-31 16:46:27.287 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ValidateHostHeader. 2025-01-31 16:46:27.287 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateValidatedTokens. 2025-01-31 16:46:27.288 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromAuthorizationHeader. 2025-01-31 16:46:27.288 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromBodyForm. 2025-01-31 16:46:27.288 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromQueryString. 2025-01-31 16:46:27.288 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens. 2025-01-31 16:46:27.288 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was marked as rejected by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens. 2025-01-31 16:46:27.288 +05:30 [DBG] AuthenticationScheme: OpenIddict.Validation.AspNetCore was not authenticated. 2025-01-31 16:46:27.295 +05:30 [INF] Authorization failed. These requirements were not met: PermissionRequirement: AbpIdentity.OrganizationUnits 2025-01-31 16:46:27.296 +05:30 [INF] AuthenticationScheme: OpenIdConnect was challenged. 2025-01-31 16:46:27.300 +05:30 [INF] Request finished HTTP/2 GET https://localhost:44362/Identity/OrganizationUnits - 302 null null 29.4896ms
115 Answer(s)
-
0
Thanks. If your project is complicated, you can test your code in a template project and share the template source code.
-
0
Thanks. If your project is complicated, you can test your code in a template project and share the template source code.
I purchased the mvc project from the ABP.IO.
-
0
Ok, waiting for your project. Thanks
-
0
Ok I have sent you an email with project. As project size was larger after compress so you will get google drive link for download in the email.
-
0
-
0
but why it is not showing to me? Is it available only for Host?
-
0
Also what are the changes you applied?
-
0
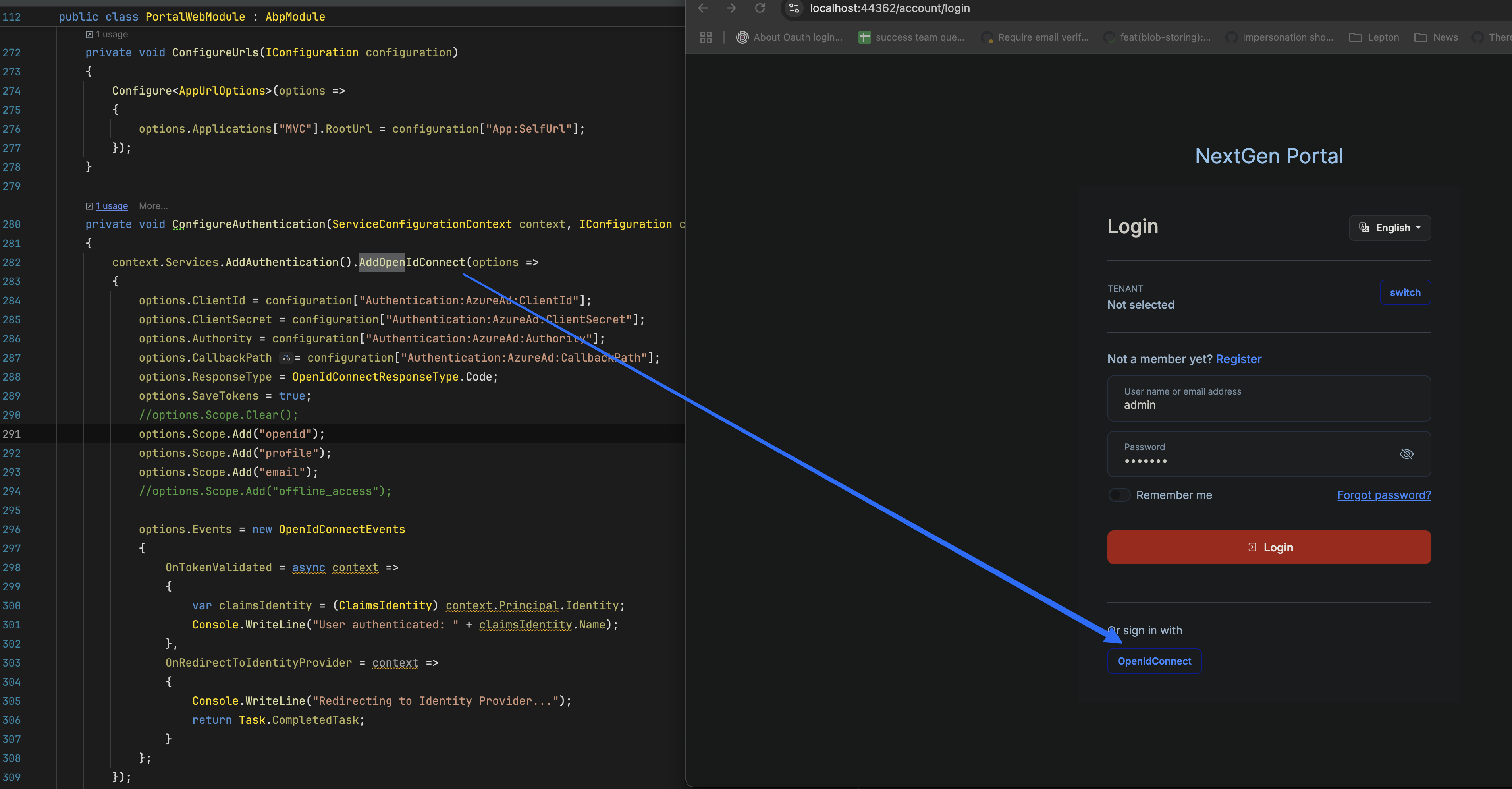
The code of
ConfigureAuthenticationprivate void ConfigureAuthentication(ServiceConfigurationContext context, IConfiguration configuration) { context.Services.AddAuthentication().AddOpenIdConnect(options => { options.ClientId = configuration["Authentication:AzureAd:ClientId"]; options.ClientSecret = configuration["Authentication:AzureAd:ClientSecret"]; options.Authority = configuration["Authentication:AzureAd:Authority"]; options.CallbackPath = configuration["Authentication:AzureAd:CallbackPath"]; options.ResponseType = OpenIdConnectResponseType.Code; options.SaveTokens = true; //options.Scope.Clear(); options.Scope.Add("openid"); options.Scope.Add("profile"); options.Scope.Add("email"); //options.Scope.Add("offline_access"); options.Events = new OpenIdConnectEvents { OnTokenValidated = async context => { var claimsIdentity = (ClaimsIdentity) context.Principal.Identity; Console.WriteLine("User authenticated: " + claimsIdentity.Name); }, OnRedirectToIdentityProvider = context => { Console.WriteLine("Redirecting to Identity Provider..."); return Task.CompletedTask; } }; }); // Add authentication using Azure AD //context.Services.AddAuthentication(options => //{ // options.DefaultScheme = CookieAuthenticationDefaults.AuthenticationScheme; // options.DefaultChallengeScheme = OpenIdConnectDefaults.AuthenticationScheme; //}) //.AddOpenIdConnect(options => //{ // options.ClientId = configuration["Authentication:AzureAd:ClientId"]; // options.ClientSecret = configuration["Authentication:AzureAd:ClientSecret"]; // options.Authority = configuration["Authentication:AzureAd:Authority"]; // options.CallbackPath = configuration["Authentication:AzureAd:CallbackPath"]; // options.ResponseType = OpenIdConnectResponseType.Code; // options.SaveTokens = true; // //options.Scope.Clear(); // options.Scope.Add("openid"); // options.Scope.Add("profile"); // options.Scope.Add("email"); // //options.Scope.Add("offline_access"); // options.Events = new OpenIdConnectEvents // { // OnTokenValidated = async context => // { // var claimsIdentity = (ClaimsIdentity)context.Principal.Identity; // Console.WriteLine("User authenticated: " + claimsIdentity.Name); // }, // OnRedirectToIdentityProvider = context => // { // Console.WriteLine("Redirecting to Identity Provider..."); // return Task.CompletedTask; // } // }; //}) //.AddCookie(CookieAuthenticationDefaults.AuthenticationScheme, options => //{ // options.Cookie.HttpOnly = true; // options.Cookie.SameSite = SameSiteMode.Strict; // Adjust based on your requirements // options.Events = new CookieAuthenticationEvents // { // OnSigningIn = context => // { // Console.WriteLine("Signing in user..."); // return Task.CompletedTask; // }, // OnSignedIn = context => // { // Console.WriteLine("User signed in: " + context.Principal.Identity.Name); // return Task.CompletedTask; // }, // OnSigningOut = context => // { // Console.WriteLine("Signing out user..."); // return Task.CompletedTask; // } // }; //}); context.Services.ForwardIdentityAuthenticationForBearer(OpenIddictValidationAspNetCoreDefaults.AuthenticationScheme); context.Services.Configure<AbpClaimsPrincipalFactoryOptions>(options => { options.IsDynamicClaimsEnabled = true; }); } -
0
Ok let me try with the code you provided.
-
0
-
0
Please share a test user of https://login.microsoftonline.com/
-
0
Please share a test user of https://login.microsoftonline.com/ Username : sharma.atul19@outlook.com Password : atul8outlook
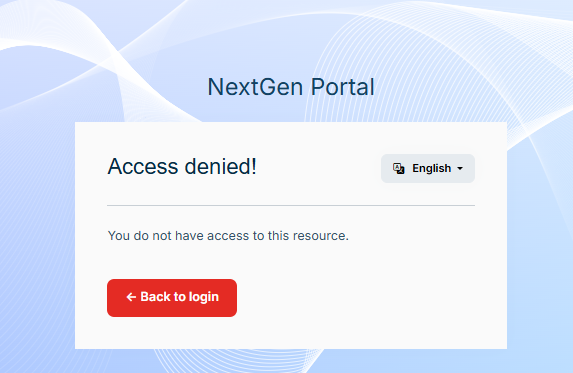
Also when I got the access denied page and click on the Back to login then host selection will be hidden.
-
0
On your mobile device, approve request CBOC1
Please create a new test user.
Thanks.
-
0
Are you getting any error with the user provided?
-
0
no. I'm trying to log in by Microsoft account, Please create a new test user.
I will test your account with your app tomorrow
Thanks.
-
0
Ok I will share the details and Also If I register a user with OpenIdConnect then what will be the default role?
Also, how to set default role to the user?
-
0
If the role is set as default. The new user will have all of default roles.
Please share your test user with liming.ma@volosoft.com
-
0
Hi, I have added a user in our AD with the email liming.ma@volosoft.com, kindly check and confirm if you have received the invitation.
-
0
hi
See the video: https://streamable.com/6uxolk
I can sign in by microsoft account and get username and email then register a new user.
-
0
If you want to change the default user roles.
You can change the code of
RegisterExternalUserAsyncmethod ofmodules/Volo.Abp.Account.Pro/src/Volo.Abp.Account.Pro.Public.Web/Pages/Account/Register.cshtml.cs -
0
Ok I will check and let you know.
Thanks.
-
0
ok
-
0
Ok it is working now for me.
Also, Instead of going to login page, select tenant and click on openIdConnect, I want to directly open the Microsoft login screen and how we will use tenant selection screen?
-
0
hi
Replace
MyTenantwith your tenant name.__tenant=MyTenantpublic async Task<IActionResult> OnGetAsync() { if (!CurrentUser.IsAuthenticated) { var provider = "OpenIdConnect"; var redirectUrl = "/Account/Login?handler=ExternalLoginCallback&__tenant=MyTenant"; var properties = SignInManager.ConfigureExternalAuthenticationProperties(provider, redirectUrl); properties.Items["scheme"] = provider; return Challenge(properties, provider); } return Page(); } -
0
Hi I want to connect tenant specific active directory, So how do i do that?
Can you please suggest any solution about it?