- ABP Framework version: v9.0.2
- UI Type: MVC
- Database System: EF Core (SQL Server)
- **Tiered (for MVC) or Auth Server Separated: yes
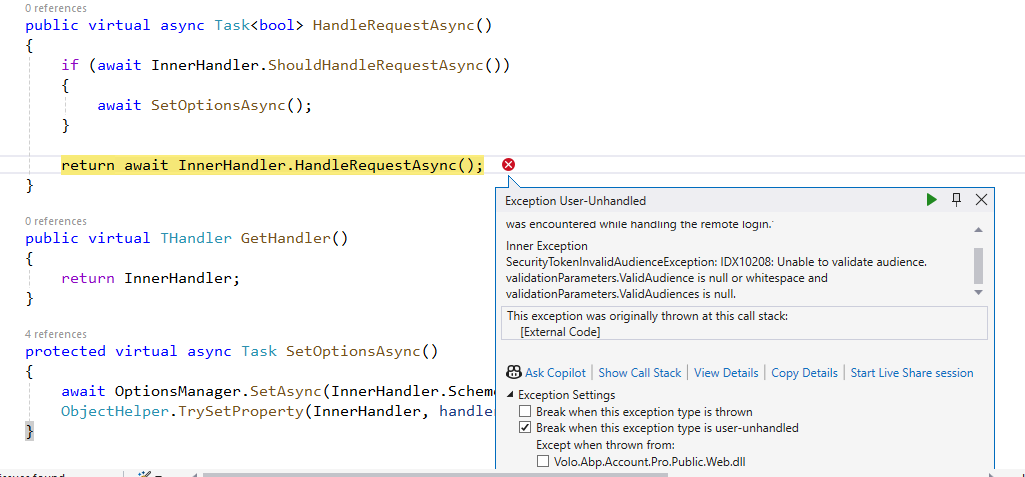
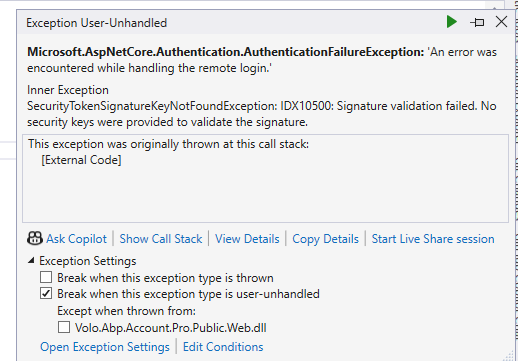
- Exception message and full stack trace: I am back and forward on redirect URL after authenticating with Microsoft Azure AD
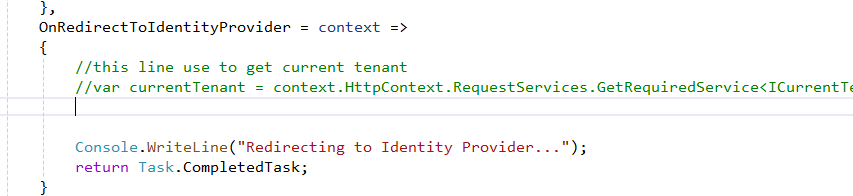
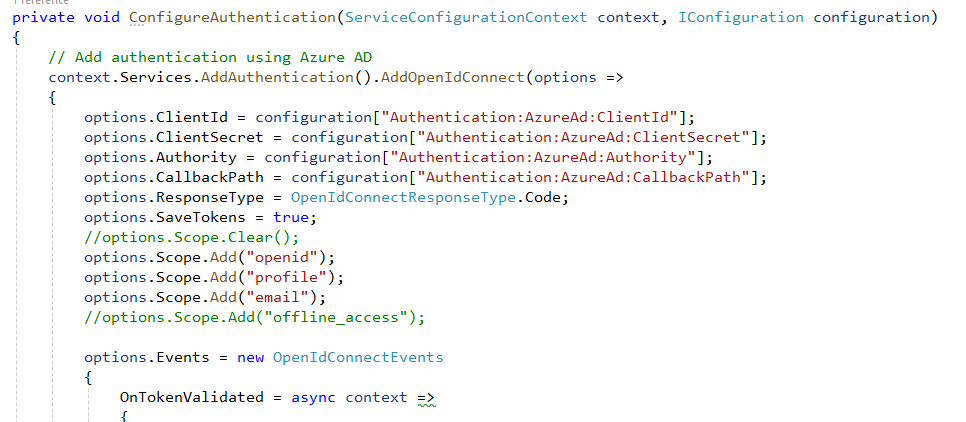
- Steps to reproduce the issue: I have added my configuration for OpenIdConnect and after that I am facing that issue. Also I am attaching video for reference as well. Video https://jmp.sh/jrphAyUq
These are the logs
2025-01-31 16:46:27.271 +05:30 [INF] Request starting HTTP/2 GET https://localhost:44362/Identity/OrganizationUnits - null null 2025-01-31 16:46:27.274 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. 2025-01-31 16:46:27.275 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri. 2025-01-31 16:46:27.275 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType. 2025-01-31 16:46:27.275 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType. 2025-01-31 16:46:27.275 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement. 2025-01-31 16:46:27.275 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader. 2025-01-31 16:46:27.287 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ValidateHostHeader. 2025-01-31 16:46:27.287 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateValidatedTokens. 2025-01-31 16:46:27.288 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromAuthorizationHeader. 2025-01-31 16:46:27.288 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromBodyForm. 2025-01-31 16:46:27.288 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromQueryString. 2025-01-31 16:46:27.288 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens. 2025-01-31 16:46:27.288 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was marked as rejected by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens. 2025-01-31 16:46:27.288 +05:30 [DBG] AuthenticationScheme: OpenIddict.Validation.AspNetCore was not authenticated. 2025-01-31 16:46:27.295 +05:30 [INF] Authorization failed. These requirements were not met: PermissionRequirement: AbpIdentity.OrganizationUnits 2025-01-31 16:46:27.296 +05:30 [INF] AuthenticationScheme: OpenIdConnect was challenged. 2025-01-31 16:46:27.300 +05:30 [INF] Request finished HTTP/2 GET https://localhost:44362/Identity/OrganizationUnits - 302 null null 29.4896ms
115 Answer(s)
-
0
hi
I dont get it. Can you explain it more?
-
0
-
0
hi
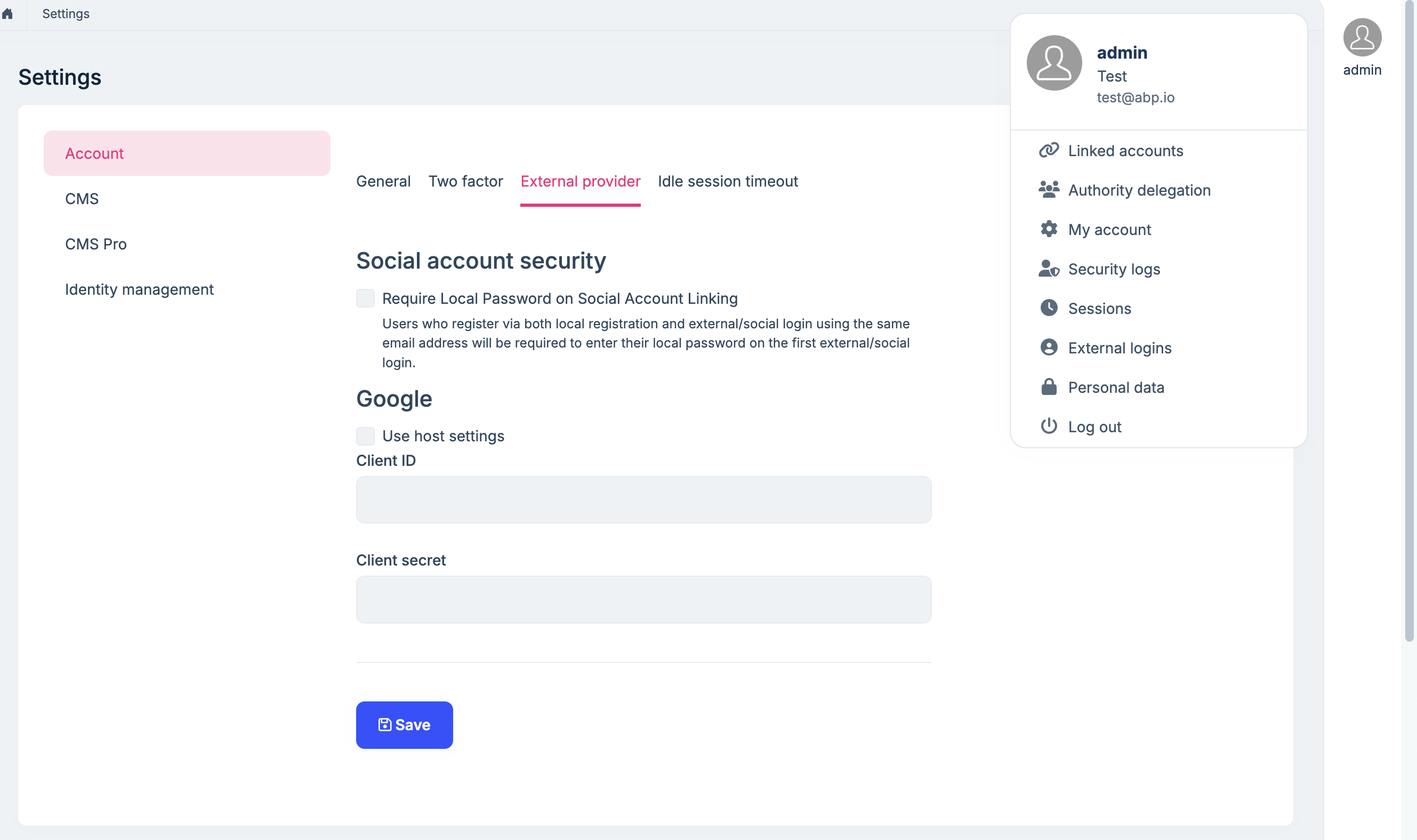
Add a new
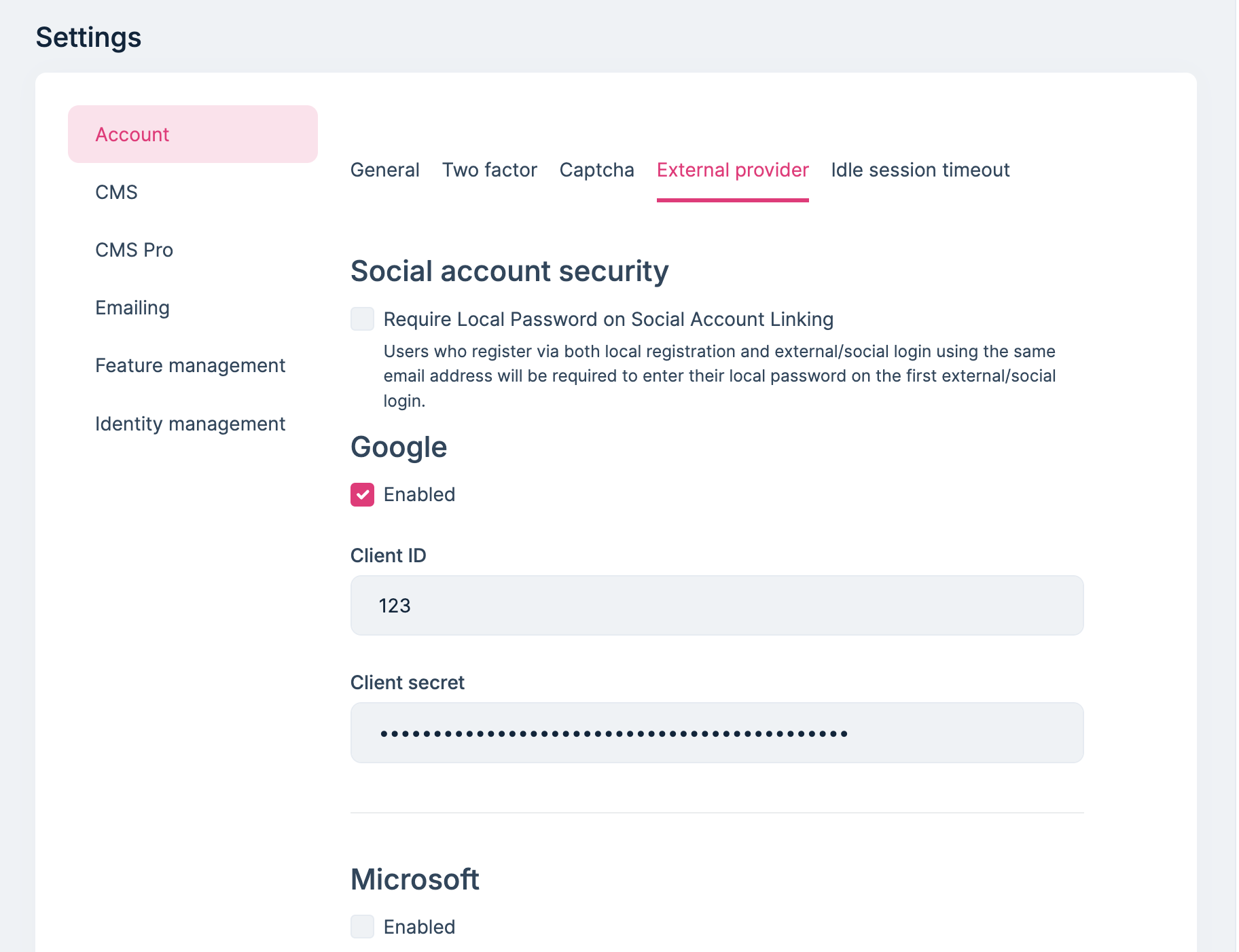
External Loginand change theAuthority, ClientId, ClientSecretetc., in the host and tenants.The social/External login system is compatible with the multi-tenancy. Each tenant can configure their own provider settings if your application is multi-tenant.
https://abp.io/docs/latest/modules/account-pro#install-a-new-external-login
-
0
-
0
It doesn’t support change client id at runtime,that’s why we add the https://abp.io/docs/latest/modules/account-pro#install-a-new-external-login feature.
-
0
how can i add and enable the OpenIdConnect as ExternalLogin?
-
0
-
0
-
0
-
0
hi
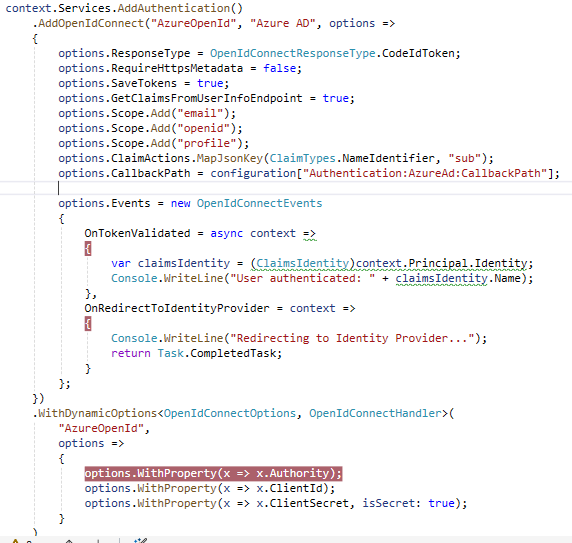
If you changed the
AuthorityYou can use a wildcard domain asIssuer{0}can be any tenant name.https://github.com/abpframework/abp-samples/blob/f46dabd078361ebb564708cce28fe8a8b7a60494/DomainTenantResolver/OpenIddict/MVC-TIERED/src/Acme.BookStore.Web/BookStoreWebModule.cs#L179-L184
https://github.com/maliming//Owl.TokenWildcardIssuerValidator
-
0
As you know we are setting authority from the tenant external provider. So How do i set it?
I can not do the hardcode values as we have dynamic paramaters.
Please suggest solution accordingly.
-
0
Do i need to set my local url in ValidIssuers?
-
0
hi
I can not do the hardcode values as we have dynamic parameters.
The
OpenIdConnectOptionsoption isIOptionsMonitor<OpenIdConnectOptions>You can add a custom implementation to get value from the database. Read the value of the tenant.
or you can set
TokenValidationParameters.ValidateIssuertofalsehttps://learn.microsoft.com/en-us/dotnet/api/microsoft.identitymodel.tokens.tokenvalidationparameters.validateissuer?view=msal-web-dotnet-latest
-
0
-
0
Also set
public bool ValidateAudience { get; set; }to false -
0
-
0
-
0
Can you please try at your end with ExternalProvider and if it is working then share your code here?
-
0
hi
Can you share your test project?
liming.ma@volosoft.com
I will download and check it. Thanks.
-
0
I already shared with you, Please check your email.
-
0
hi
I have the NextGenPortal project.
Please share two configurations for the
External provider. Host and tenantThanks.
-
0
I have just enabled the Azure Open Id configuration from host and override in Tenant Tenant Configurations Authority : https://login.microsoftonline.com/b9eb6473-28b2-46c1-9f80-c90c9298253b ClientId : aa3735b8-1b81-43b4-a38c-7b454ae4bb87 ClientSecret : wvG8Q~le8BW0EX-FdHsaGtUQ7ZHPxJBkMdAgva9s
If you need then you can use same credentials for host as well.
-
0
hi
I can log in successfully by microsoft in host and tenant with the below configuration
Authority : https://login.microsoftonline.com/b9eb6473-28b2-46c1-9f80-c90c9298253b ClientId : aa3735b8-1b81-43b4-a38c-7b454ae4bb87 ClientSecret : wvG8Q~le8BW0EX-FdHsaGtUQ7ZHPxJBkMdAgva9sWhat is your GitHub username? I will invite you to test the project repos.
https://github.com/maliming/NextGenPortal
-
0
My github account is https://github.com/alpeshkalena
Also do we need to set same credentials for Host and Tenant?
-
0
hi
https://github.com/maliming/NextGenPortal/invitations
Also do we need to set same credentials for Host and Tenant?
You can set different azure openid configuration for Host and Tenant