32 Answer(s)
-
0
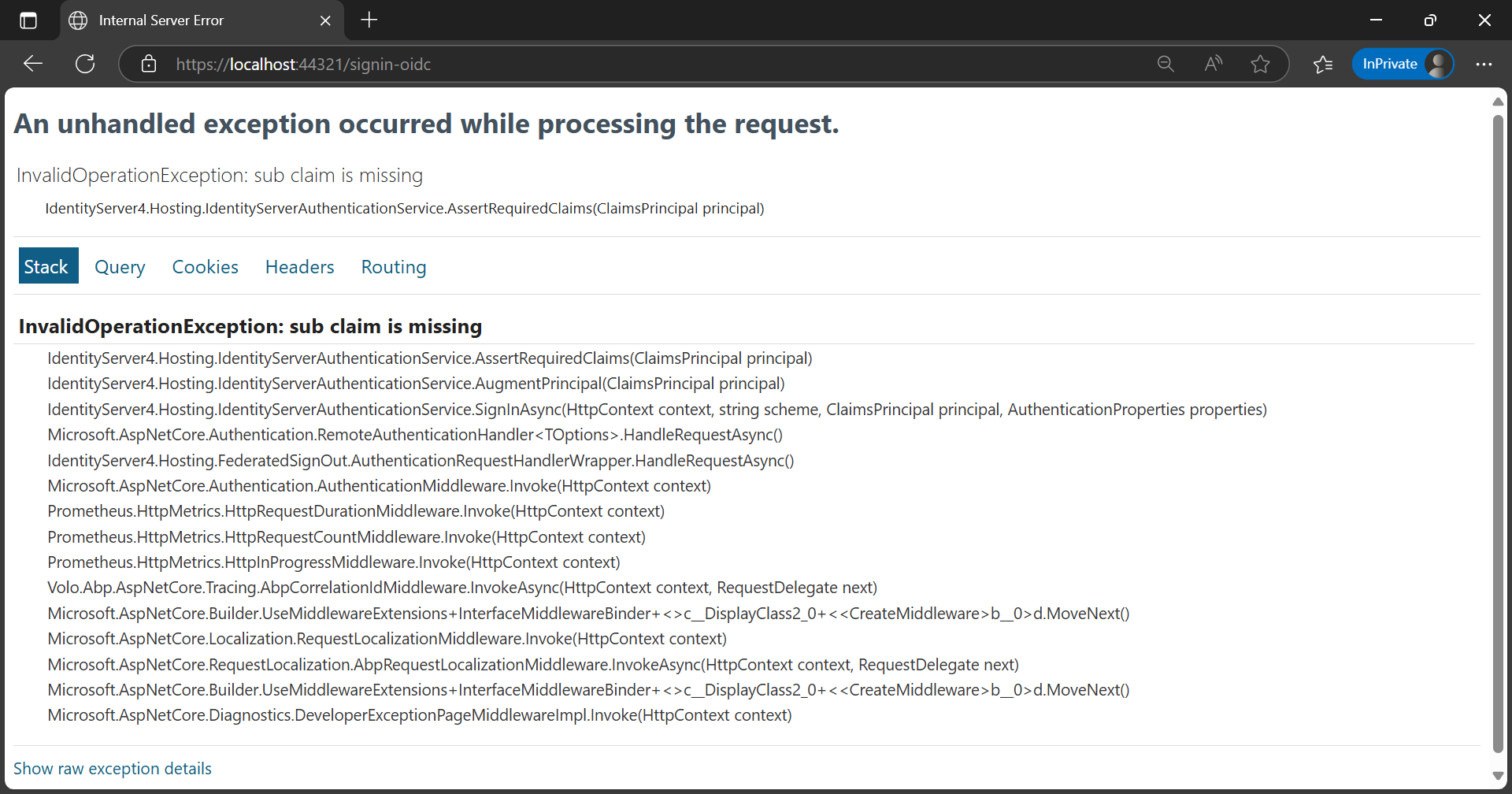
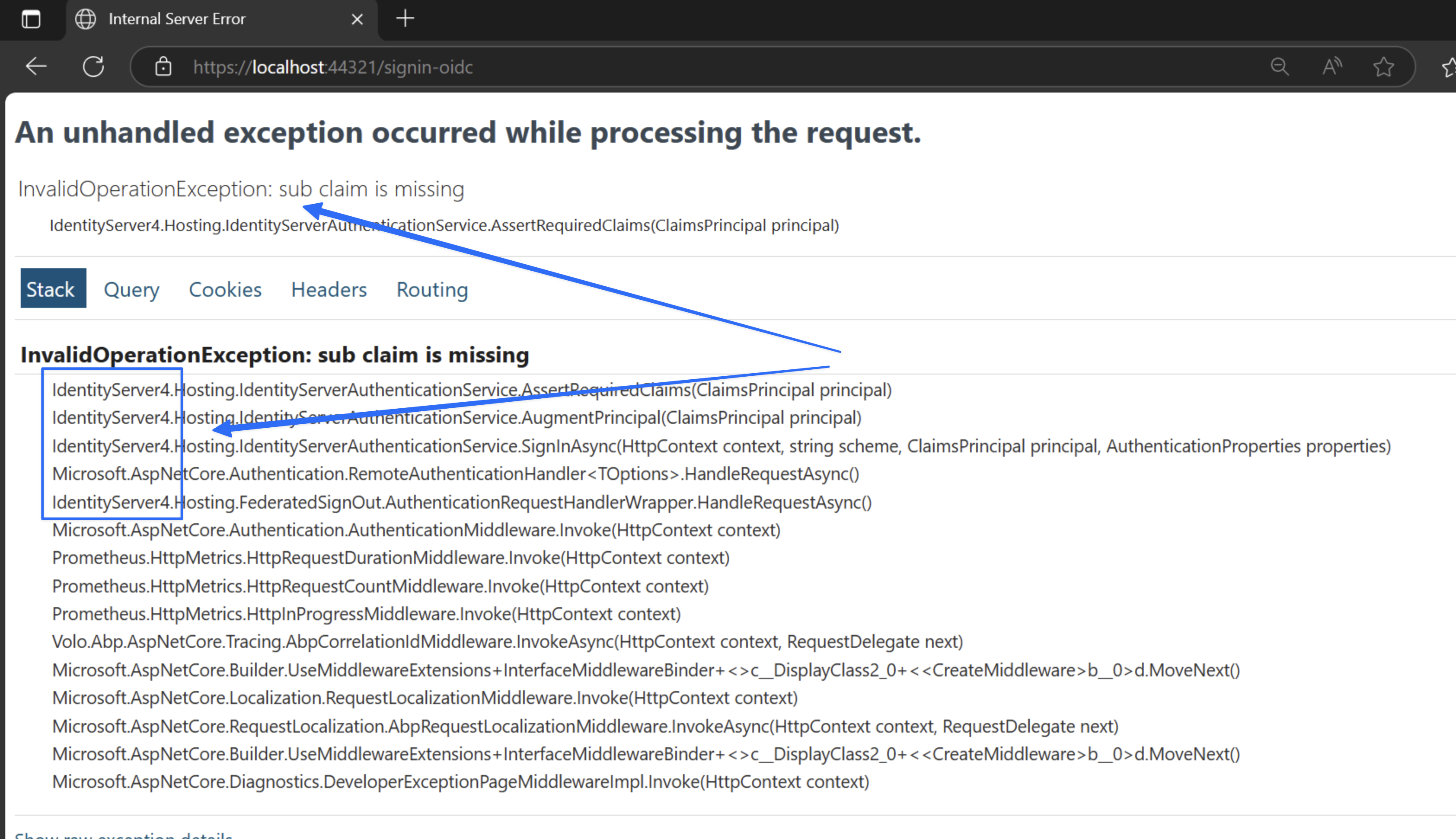
The error
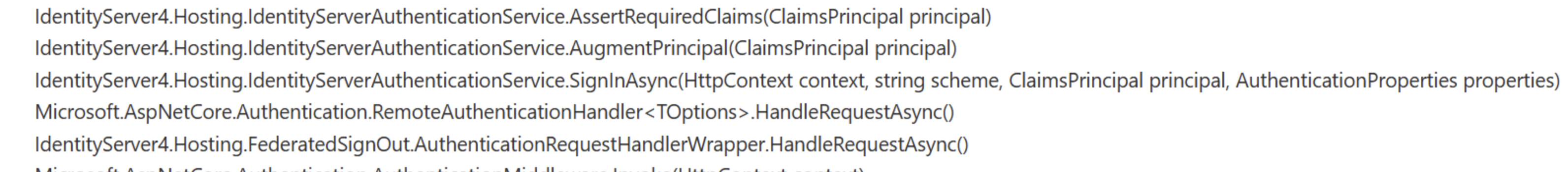
InvalidOperationException: sub claim is missingafter upgrading to ABP 9.0 (while still using IdentityServer4) is due to a missingsub(subject) claim in the authentication response. IdentityServer4 requires thesubclaim to identify the user.In ABP 9.0, there have been significant changes and migration steps, especially regarding authentication and claims handling. If you have not migrated to OpenIddict and are still using IdentityServer4, you must ensure that your authentication pipeline and claims transformation logic are compatible with the new ABP version.
Specifically, you should:
- Check your user claims generation logic and ensure the
subclaim is present and correctly mapped for the authenticated user. - Review any custom profile service or claims transformation code to ensure it is not omitting the
subclaim. - If you are using custom login or external authentication providers, ensure they provide the
subclaim in the identity token.
- Check your user claims generation logic and ensure the
For more details and migration steps, see:
These resources provide guidance on handling authentication and claims in ABP 9.0 and can help you resolve the missing
subclaim issue.
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
- Check your user claims generation logic and ensure the sub claim is present and correctly mapped for the authenticated user. - sub claim is mapped for the authenticated user.
- Review any custom profile service or claims transformation code to ensure it is not omitting the sub claim.- We did not implemented any custom logic.
- If you are using custom login or external authentication providers, ensure they provide the sub claim in the identity token. - We did not implemented any custom logic and not using any external authentication providers
-
0
hi @viswajwalith
Is https://localhost:44321/ an Identity Server website? Does it contain the
AddIdentityServer?Are you signed in by external login?
Thanks
-
0
Dear Maliming,
Is https://localhost:44321/ an Identity Server website? - No, It is not Identity server, it is Back office Web. Are you signed in by external login? - No
-
0
-
0
Hi Maliming,
can you share your Email id.
-
0
hi
liming.ma@volosoft.com
-
0
Hi Maliming,
Sent you email.
-
0
hi
Please remove
AddIdentityServerfromhttps://localhost:44321/ - Back office WebCan you also share the module code of
https://localhost:44321/ - Back office Web?Thanks.
-
0
Hi Maliming,
Sent you email.
-
0
Thanks, I've replied to the email.
-
0
It s not possible to send the code we may have the screenshare session to take this further.
-
0
-
0
[liming.ma@volosoft.com] said: hi
Your
Back office Webproject has an indirect dependency onIdentityServer4Please search code and remove it.
Hi, we made some changes to map all the claims received via token to claimsIdentity in "ConfigureServices" under web module file . After that change we are able to login and roles are showing as mapped but permissins are not mapping to the logged in user in backend.
If we check the permissions in JS we are able to see the proper permissions but not at backend so getting forbidden erros.
Please advise.
Note: We still using IdentityServer4 and if we are making callss to API via PostMan getting the data without any roles or permissions issues
options.Events = new OpenIdConnectEvents { OnRemoteFailure = context => { Log.Information("Remote login failed: " + context.Failure?.Message); return Task.CompletedTask; }, OnTokenValidated = context => { Log.Information("Token validated!"); var claimsIdentity = context.Principal.Identity as ClaimsIdentity; var idToken = context.ProtocolMessage.IdToken; var handler = new JwtSecurityTokenHandler(); var token = handler.ReadJwtToken(idToken); foreach (var claim in token.Claims) { if (!claimsIdentity.HasClaim(c => c.Type == claim.Type && c.Value == claim.Value)) { Log.Information($"Manually adding claim: {claim.Type} = {claim.Value}"); claimsIdentity.AddClaim(claim); } } return Task.CompletedTask; } }; -
0
hi
Please try to remove
IdentityServer4fromBack office Web projectfirst.Then, the claims problem you can see https://abp.io/community/articles/how-claim-type-works-in-asp-net-core-and-abp-framework-km5dw6g1
Thanks.
-
0
[liming.ma@volosoft.com] said: hi
Please try to remove
IdentityServer4fromBack office Web projectfirst.Then, the claims problem you can see https://abp.io/community/articles/how-claim-type-works-in-asp-net-core-and-abp-framework-km5dw6g1
Thanks.
Hi, Thanks for the response but I feel there is some miss-understanding, still we tried to find the reference for IdentityServer4 across our web project but no where we found that. If you can elobrate much more that might be useful.
Our Back Office Web Project has a reference to IdentityServer Web and Web dosent have reference to Identity4 and we checked over there as well but not able to find any clue
Also we are not in a plans to OpenIdDict and want to continue with IdentityServer4 for now. Do u think still IdentityServer4 need to be removed from web project?
-
0
-
0
[liming.ma@volosoft.com] said: hi
Removing IdentityServer4 from the
Back office Webproject will fix this error.As you can see. the IdentityServer4 is used in your
Back office WebprojectAs I mentioned earlier, we have overcome this issue by assigning the claims again but now facing the permissions issue
-
0
If we check the permissions in JS we are able to see the proper permissions but not at backend so getting forbidden erros.
Sorry for that. I missed it.
Can you check the claims value and type by adding a custom middleware after
UseAuthentication?app.UseAuthentication(); app.Use(async (httpContext, next) => { var claims = httpContext.User.Claims; var currentUser = httpContext.RequestServices.GetRequiredService<ICurrentUser>().GetAllClaims(); var userid = AbpClaimTypes.UserId; var username = AbpClaimTypes.UserName; var roleClaimType = AbpClaimTypes.Role; await next(httpContext); });Thanks.
-
0
[liming.ma@volosoft.com] said:
If we check the permissions in JS we are able to see the proper permissions but not at backend so getting forbidden erros.
Sorry for that. I missed it.
Can you check the claims value and type by adding a custom middleware after
UseAuthentication?app.UseAuthentication(); app.Use(async (httpContext, next) => { var claims = httpContext.User.Claims; var currentUser = httpContext.RequestServices.GetRequiredService<ICurrentUser>().GetAllClaims(); var userid = AbpClaimTypes.UserId; var username = AbpClaimTypes.UserName; var roleClaimType = AbpClaimTypes.Role; await next(httpContext); });Thanks.
Thanks for the quick response, I belive this need to be added in Web Module file right. will give a try and update you back.
-
0
hi
Add it to the project that has
forbidden errosAnd can you share the debug logs forforbidden erros?https://abp.io/support/questions/8622/How-to-enable-Debug-logs-for-troubleshoot-problems
Thanks.
-
0
[liming.ma@volosoft.com] said: hi
Add it to the project that has
forbidden errosAnd can you share the debug logs forforbidden erros?https://abp.io/support/questions/8622/How-to-enable-Debug-logs-for-troubleshoot-problems
Thanks.
Hi We have added the code in both web and one of the service still getting the autorization error, I have emails the log files to ur email id
-
0
hi
Request finished HTTP/2 GET https://localhost:44321/api/identity/roles?filter=&sorting=name%20asc&skipCount=0&maxResultCount=10 - 401
The
Exceego.EHSWatch.AppV3.Web.use C# HTTP remote proxy to call the Identity/role API.Can you share the debug logs from
Identity/role APIwebsite?By the way, you are not enabled the
debuglogs forMicrosoftnamespace. See https://abp.io/support/questions/8622/How-to-enable-Debug-logs-for-troubleshoot-problemsvar loggerConfiguration = new LoggerConfiguration() .MinimumLevel.Debug() .MinimumLevel.Override("Microsoft.EntityFrameworkCore", LogEventLevel.Warning) .Enrich.FromLogContext() .WriteTo.Async(c => c.File("Logs/logs.txt"))Thanks.
-
0
Hi,
Sent you email.
-
0
hi
The Microsoft logs level still not Debug
Please use the log configuration code below.
var loggerConfiguration = new LoggerConfiguration() .MinimumLevel.Debug() .MinimumLevel.Override("Microsoft.EntityFrameworkCore", LogEventLevel.Warning) .Enrich.FromLogContext() .WriteTo.Async(c => c.File("Logs/logs.txt"))2025-06-30 19:52:16.805 +05:30 [INF] Request starting HTTP/1.1 GET http://localhost:44371/api/employee-service/dashboard-pages?PageId=HOMEDASHBOARD&SkipCount=0&MaxResultCount=20000&api-version=1.0 - null 0 2025-06-30 19:52:17.252 +05:30 [INF] Executing endpoint 'Exceego.EHSWatch.AppV3.EmployeeService.Controllers.DashboardPages.DashboardPageController.GetListAsync (Exceego.EHSWatch.AppV3.EmployeeService.HttpApi)' 2025-06-30 19:52:18.685 +05:30 [INF] Authorization failed. These requirements were not met: PermissionRequirement: EmployeeService.CustomReports 2025-06-30 19:52:19.936 +05:30 [INF] Request finished HTTP/1.1 GET https://localhost:44371/api/employee-service/dashboard-pages?PageId=HOMEDASHBOARD&SkipCount=0&MaxResultCount=20000&api-version=1.0 - 403 0 null 3131.5555msThese requirements were not met: PermissionRequirement: EmployeeService.CustomReports
Does your current user have
EmployeeService.CustomReportspermission?If the
403error only happened onExceego.EHSWatch.AppV3.EmployeeService.HttpApi.Host.website.Please enable the
Debuglog level and share again.Also output some info to the logs.
app.UseAuthentication(); app.Use(async (httpContext, next) => { var logger = httpContext.RequestServices.GetRequiredService<ILogger<EmployeeServiceHttpApiHostModule>>(); var claims = httpContext.User.Claims.Select(x => new { x.Type, x.Value }).ToList(); logger.LogError("HttpContext.User Claims:"); logger.LogError(JsonSerializer.Serialize(claims)); var currentUser = httpContext.RequestServices.GetRequiredService<ICurrentUser>().GetAllClaims().Select(x => new { x.Type, x.Value }).ToList(); logger.LogError("Current User Claims:"); logger.LogError(JsonSerializer.Serialize(currentUser)); var userid = AbpClaimTypes.UserId; var username = AbpClaimTypes.UserName; var roleClaimType = AbpClaimTypes.Role; logger.LogError($"UserId Claim Type: {userid}"); logger.LogError($"UserName Claim Type: {username}"); logger.LogError($"Role Claim Type: {roleClaimType}"); var authorizationHeader = httpContext.Request.Headers["Authorization"]; logger.LogError(!string.IsNullOrEmpty(authorizationHeader) ? $"Authorization Header: {authorizationHeader}" : "Authorization Header is missing or empty."); await next(httpContext); });Thanks.